312-49v10 Exam Question 1
Data is striped at a byte level across multiple drives, and parity information is distributed among all member drives.
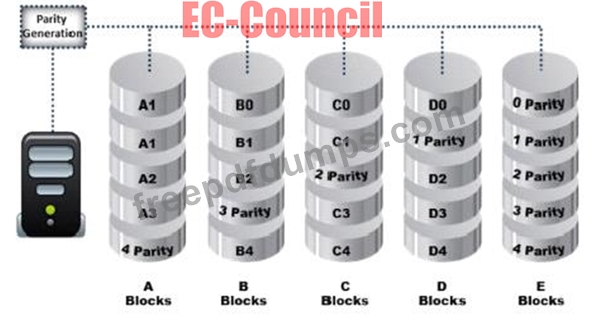
What RAID level is represented here?

What RAID level is represented here?
312-49v10 Exam Question 2
You are working as a Computer forensics investigator for a corporation on a computer abuse case. You discover evidence that shows the subject of your investigation is also embezzling money from the company. The company CEO and the corporate legal counsel advise you to contact law enforcement and provide them with the evidence that you have found. The law enforcement officer that responds requests that you put a network sniffer on your network and monitor all traffic to the subject's computer. You inform the officer that you will not be able to comply with that request because doing so would:
312-49v10 Exam Question 3
You are contracted to work as a computer forensics investigator for a regional bank that has four 30 TB storage area networks that store customer data.
What method would be most efficient for you to acquire digital evidence from this network?
What method would be most efficient for you to acquire digital evidence from this network?
312-49v10 Exam Question 4
What command-line tool enables forensic Investigator to establish communication between an Android device and a forensic workstation in order to perform data acquisition from the device?
312-49v10 Exam Question 5
Julia is a senior security analyst for Berber Consulting group. She is currently working on a contract for a small accounting firm in Florid a. They have given her permission to perform social engineering attacks on the company to see if their in-house training did any good. Julia calls the main number for the accounting firm and talks to the receptionist. Julia says that she is an IT technician from the company's main office in Iowa. She states that she needs the receptionist's network username and password to troubleshoot a problem they are having. Julia says that Bill Hammond, the CEO of the company, requested this information. After hearing the name of the CEO, the receptionist gave Julia all the information she asked for. What principal of social engineering did Julia use?

