312-96 Exam Question 1
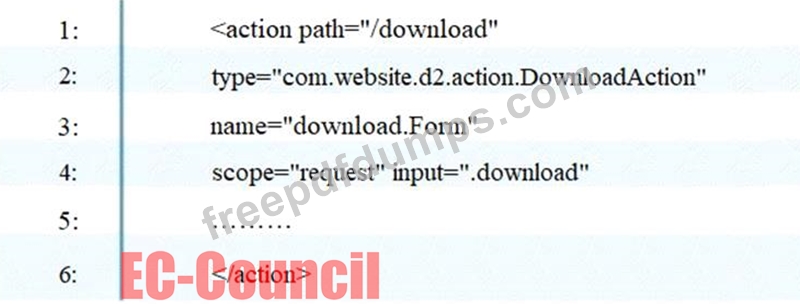
To enable the struts validator on an application, which configuration setting should be applied in the struts validator configuration file?

312-96 Exam Question 2
Jacob, a Security Engineer of the testing team, was inspecting the source code to find security vulnerabilities.
Which type of security assessment activity Jacob is currently performing?
Which type of security assessment activity Jacob is currently performing?
312-96 Exam Question 3
Which of the risk assessment model is used to rate the threats-based risk to the application during threat modeling process?
312-96 Exam Question 4
A US-based ecommerce company has developed their website www.ec-sell.com to sell their products online. The website has a feature that allows their customer to search products based on the price. Recently, a bug bounty has discovered a security flaw in the Search page of the website, where he could see all products from the database table when he altered the website URL http://www.ec-sell.com/products.jsp?val=100 to http://www.ec-sell.com/products.jsp?val=200 OR '1'='1 -. The product.jsp page is vulnerable to
312-96 Exam Question 5
Which of the following relationship is used to describe security use case scenario?

