DEA-1TT4 Exam Question 76
What is a benefit of link aggregation?
DEA-1TT4 Exam Question 77
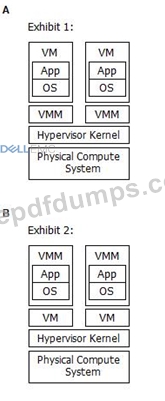
Which exhibit represents a Type 1 hypervisor?
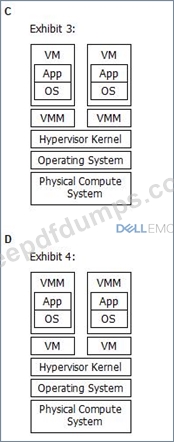


DEA-1TT4 Exam Question 78
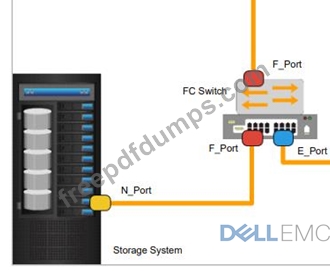
How do VSANs ensure security in an IT infrastructure?
DEA-1TT4 Exam Question 79
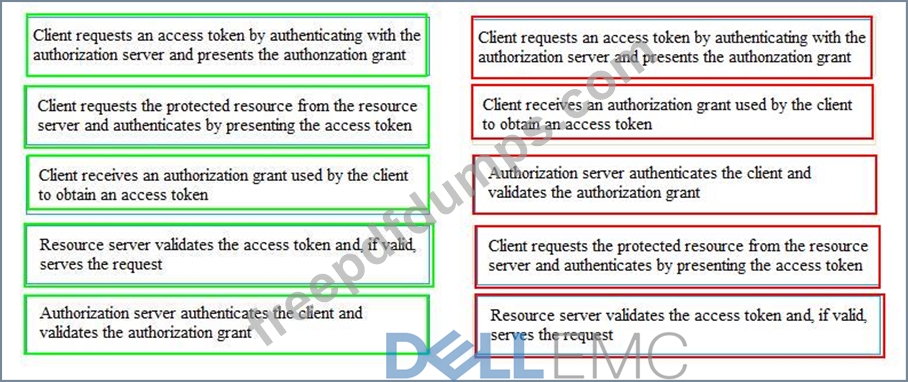
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?
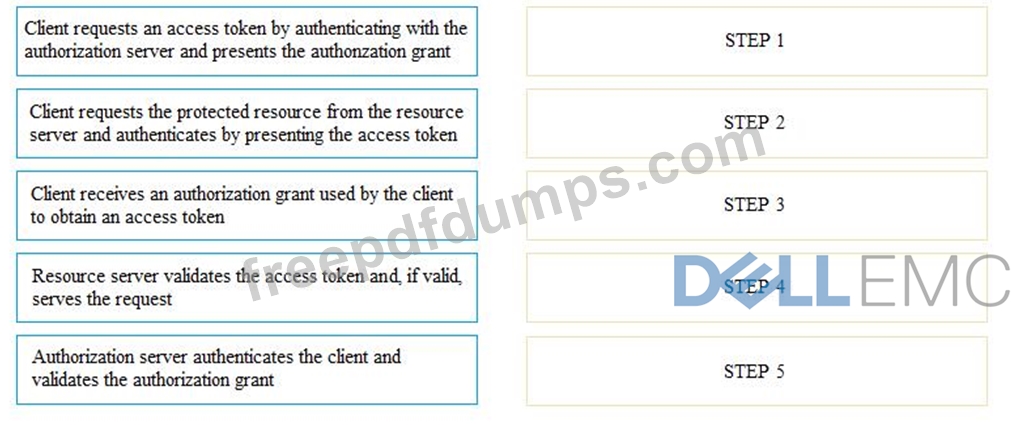
1. The client requests authorization from the resource owner. The authorization request can be made directly to the resource owner, or indirectly through the authorization server.
2. The client receives an authorization grant, which is a credential representing the resource owner's authorization to access its protected resources. It is used by the client to obtain an access token. Access tokens are credentials that are used to access protected resources. An access token is a string representing an authorization issued to the client. The string is usually opaque to the client. Tokens represent specific scopes and durations of access, granted by the resource owner, and enforced by the resource server and authorization server.
3. The client requests an access token by authenticating with the authorization server and presenting the authorization grant.
4. The authorization server authenticates the client and validates the authorization grant, and if valid, issues an access token.
5. The client requests the protected resource from the resource server and authenticates by presenting the access token.
6. The resource server validates the access token, and if valid, serves the request.

1. The client requests authorization from the resource owner. The authorization request can be made directly to the resource owner, or indirectly through the authorization server.
2. The client receives an authorization grant, which is a credential representing the resource owner's authorization to access its protected resources. It is used by the client to obtain an access token. Access tokens are credentials that are used to access protected resources. An access token is a string representing an authorization issued to the client. The string is usually opaque to the client. Tokens represent specific scopes and durations of access, granted by the resource owner, and enforced by the resource server and authorization server.
3. The client requests an access token by authenticating with the authorization server and presenting the authorization grant.
4. The authorization server authenticates the client and validates the authorization grant, and if valid, issues an access token.
5. The client requests the protected resource from the resource server and authenticates by presenting the access token.
6. The resource server validates the access token, and if valid, serves the request.
DEA-1TT4 Exam Question 80
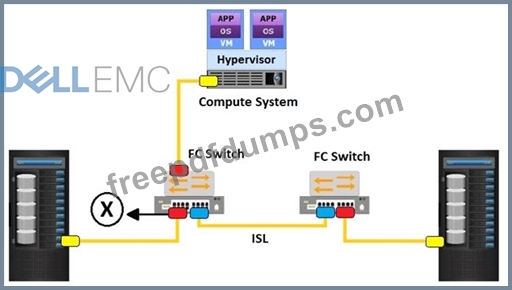
What does the "X" represent in the exhibit?