DEA-1TT5 Exam Question 21
What accurately describes the scale-out storage architecture?
Response:
Response:
DEA-1TT5 Exam Question 22
A company is planning to perform a cloud-based backup. They want to send their data over a public network to a cloud backup device.
Which security control mechanism helps to protect the data from an attacker?
Which security control mechanism helps to protect the data from an attacker?
DEA-1TT5 Exam Question 23
DRAG DROP
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?
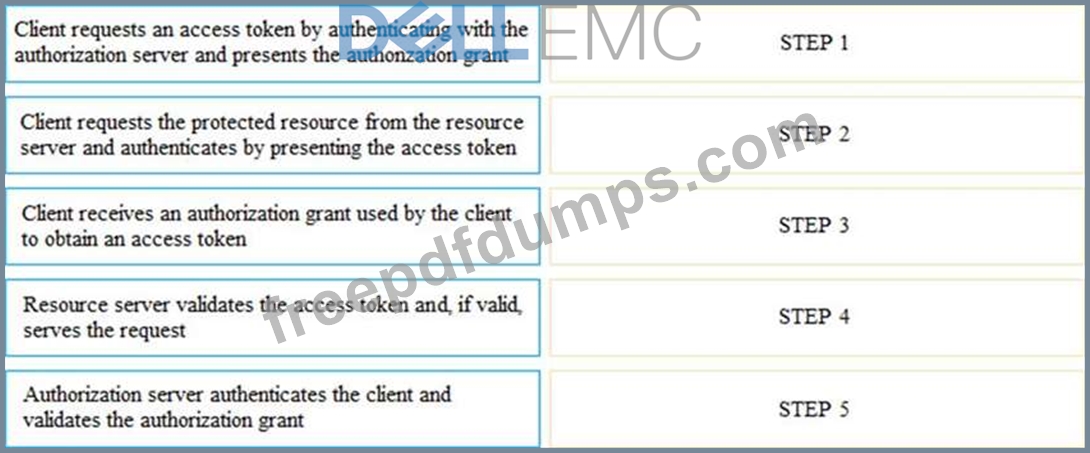
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?

DEA-1TT5 Exam Question 24
Which cloud deployment model allows provisioning of a cloud infrastructure only for use by a single organization having multiple consumers?
DEA-1TT5 Exam Question 25
An organization has an iSCSI storage system accessed by 20 compute systems running a hypervisor over a physical Ethernet network. The network enables the transfer of compute-to-compute, compute-to- storage, and management traffic.
The compute systems host several virtual machines that are accessed by 31 user groups. In addition, the network has two Ethernet core switches in an active/passive configuration and three edge switches that connect all the compute systems. Multiple VLAN trunk links exist between the core and the edge switches.
However, recently the user groups are experiencing performance issues due to excessive utilization of the core switch and the trunk links. What can be implemented to minimize the performance issues?
Response:
The compute systems host several virtual machines that are accessed by 31 user groups. In addition, the network has two Ethernet core switches in an active/passive configuration and three edge switches that connect all the compute systems. Multiple VLAN trunk links exist between the core and the edge switches.
However, recently the user groups are experiencing performance issues due to excessive utilization of the core switch and the trunk links. What can be implemented to minimize the performance issues?
Response:


