301b Exam Question 21
An IT administrator wants to log which server is being load balanced to by a user with IP address
10.10.10.25.
Which iRule should the LTM Specialist use to fulfill the request?
10.10.10.25.
Which iRule should the LTM Specialist use to fulfill the request?
301b Exam Question 22
-- Exhibit -
-- Exhibit --
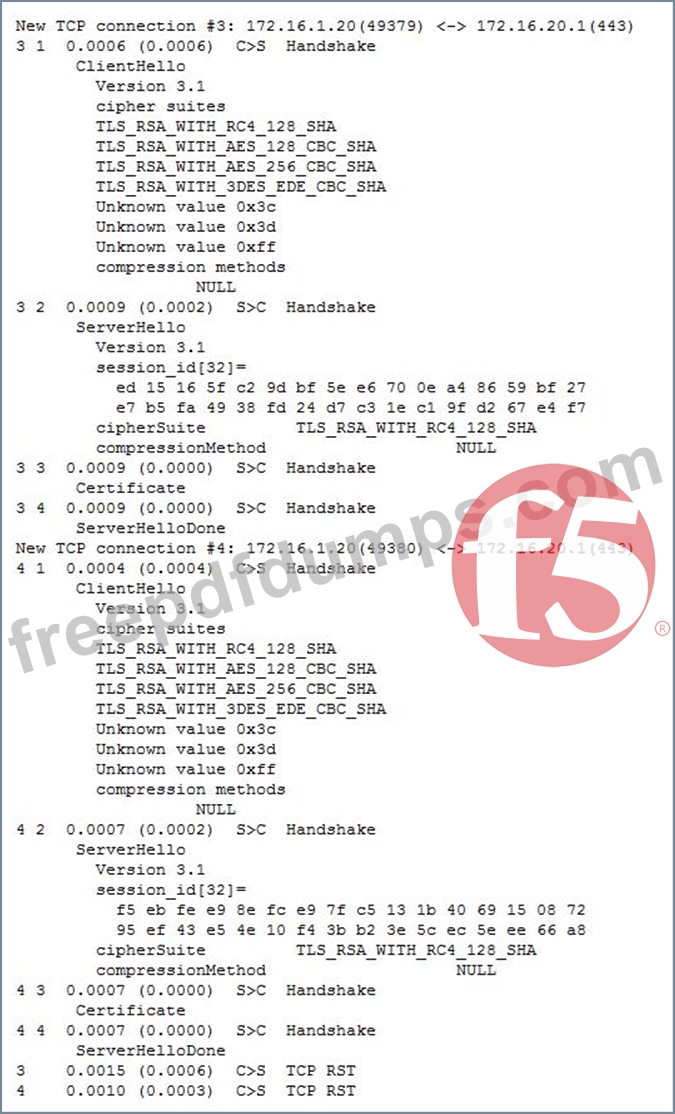
Refer to the exhibits.
After upgrading LTM from v10 to v11, users are unable to connect to an application. The virtual server is using a client SSL profile for re-terminating SSL for payload inspection, but a server SSL profile is being used to re-encrypt the request.
A client side ssldump did NOT show any differences between the traffic going directly to the server and the traffic being processed by the LTM device. However, packet capture was done on the server, and differences were noted.
Which modification will allow the LTM device to process the traffic correctly?


-- Exhibit --
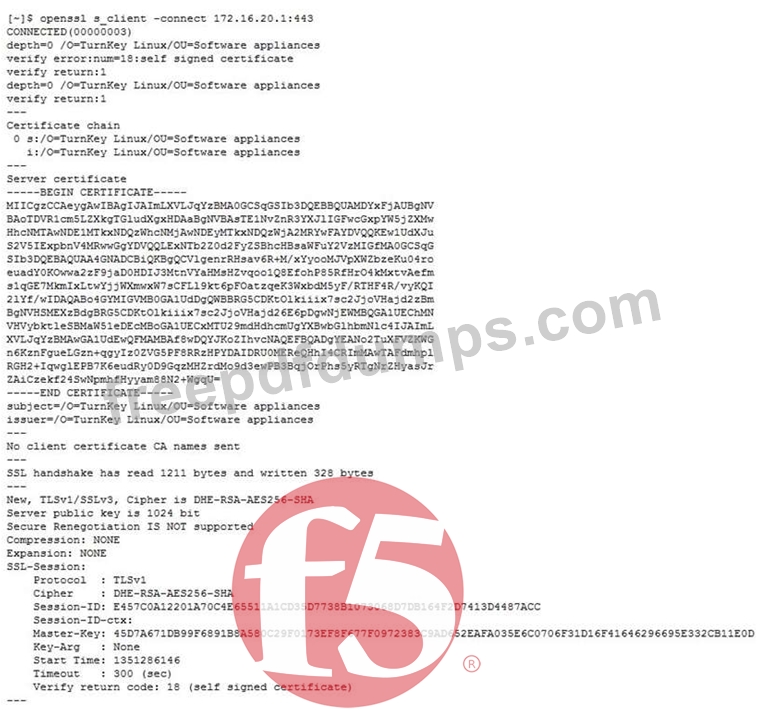
Refer to the exhibits.
After upgrading LTM from v10 to v11, users are unable to connect to an application. The virtual server is using a client SSL profile for re-terminating SSL for payload inspection, but a server SSL profile is being used to re-encrypt the request.
A client side ssldump did NOT show any differences between the traffic going directly to the server and the traffic being processed by the LTM device. However, packet capture was done on the server, and differences were noted.
Which modification will allow the LTM device to process the traffic correctly?
301b Exam Question 23
A failover event is recorded in the following log messages:
Jan 01 00:56:56 BIG-IP notice mcpd[5318]: 01070727:5: Pool /Common/my-pool member / Common/10.0.0.10:80 monitor status down.
Jan 01 00:56:56 BIG-IP notice sod[5855]: 010c0045:5: Leaving active, group score 10 peer group score 20.
Jan 01 00:56:56 BIG-IP notice sod[5855]: 010c0052:5: Standby for traffic group /Common/traffic-group-1.
Jan 01 00:56:56 BIG-IP notice sod[5855]: 010c0018:5: Standby
Jan 01 00:57:06 BIG-IP notice logger: /usr/bin/tmipsecd --tmmcount 4 ==> /usr/bin/bigstart stop racoon What is the cause of the failover?
Jan 01 00:56:56 BIG-IP notice mcpd[5318]: 01070727:5: Pool /Common/my-pool member / Common/10.0.0.10:80 monitor status down.
Jan 01 00:56:56 BIG-IP notice sod[5855]: 010c0045:5: Leaving active, group score 10 peer group score 20.
Jan 01 00:56:56 BIG-IP notice sod[5855]: 010c0052:5: Standby for traffic group /Common/traffic-group-1.
Jan 01 00:56:56 BIG-IP notice sod[5855]: 010c0018:5: Standby
Jan 01 00:57:06 BIG-IP notice logger: /usr/bin/tmipsecd --tmmcount 4 ==> /usr/bin/bigstart stop racoon What is the cause of the failover?
301b Exam Question 24
-- Exhibit -
-- Exhibit -
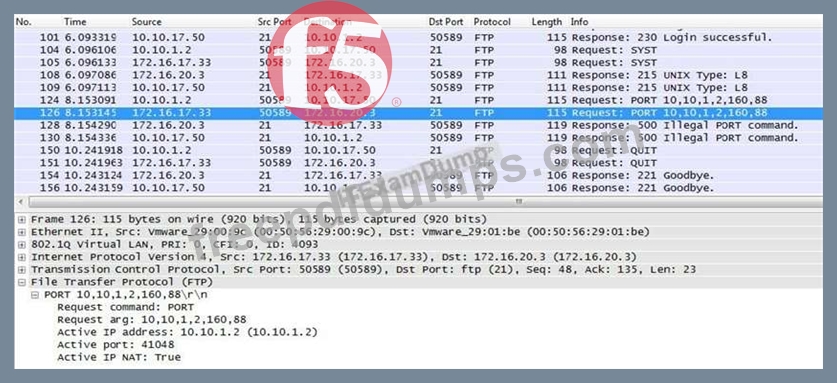
Refer to the exhibit.
An LTM Specialist is investigating reports that users are unable to perform some commands through an FTP virtual server. The users are receiving the FTP error "500 Illegal PORT command." The virtual server is configured to SNAT using automap. The LTM Specialist performs a capture on the server side of the LTM device.
Why is the server returning this error?

-- Exhibit -
Refer to the exhibit.
An LTM Specialist is investigating reports that users are unable to perform some commands through an FTP virtual server. The users are receiving the FTP error "500 Illegal PORT command." The virtual server is configured to SNAT using automap. The LTM Specialist performs a capture on the server side of the LTM device.
Why is the server returning this error?
301b Exam Question 25
There are three servers in the pool: 172.16.20.1, 172.16.20.2, and 172.16.20.3, with the virtual IP address 10.0.20.88.
A user CANNOT connect to an HTTP application. To understand the problem and find a solution, the LTM Specialist runs two concurrent traces on the LTM device, with the following results:
Trace on client side:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on 0.0, link-type EN10MB (Ethernet), capture size 96 bytes
22:22:07.423759 IP 172.16.20.100.53875 > 10.0.20.88.80: S 998346084:998346084(0)
win 5840 <mss 1460,sackOK,timestamp 67942058 0,nop,wscale 4>
22:22:07.424056 IP 10.0.20.88.80 > 172.16.20.100.53875: S 4671780:4671780(0) ack
998346085 win 4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392362490 67942058,sackOK,eol> 22:22:07.424776 IP 172.16.20.100.53875 > 10.0.20.88.80: . ack 1 win 365
<nop,nop,timestamp 67942058 2392362490>
22:22:07.424790 IP 172.16.20.100.53875 > 10.0.20.88.80: P 1:149(148) ack 1 win 365 <nop,nop,timestamp 67942058 2392362490> 22:22:07.424891 IP 10.0.20.88.80 > 172.16.20.100.53875: . ack 149 win 4528
<nop,nop,timestamp 2392362491 67942058>
22:22:12.024850 IP 10.0.20.88.80 > 172.16.20.100.53875: R 1:1(0) ack 149 win 4528
6 packets captured
6 packets received by filter
0 packets dropped by kernel
Trace on server side:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on internal, link-type EN10MB (Ethernet), capture size 96 bytes
22:22:07.424881 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win
4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392362491 0,sackOK,eol>
22:22:08.424893 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win 4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392363491 0,sackOK,eol>
22:22:09.625082 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win 4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392364691 0,sackOK,eol>
22:22:10.825194 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win 4380 <mss 1460,sackOK,eol>
4 packets captured 4 packets received by filter 0 packets dropped by kernel
What should the LTM Specialist do to solve the problem?
A user CANNOT connect to an HTTP application. To understand the problem and find a solution, the LTM Specialist runs two concurrent traces on the LTM device, with the following results:
Trace on client side:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on 0.0, link-type EN10MB (Ethernet), capture size 96 bytes
22:22:07.423759 IP 172.16.20.100.53875 > 10.0.20.88.80: S 998346084:998346084(0)
win 5840 <mss 1460,sackOK,timestamp 67942058 0,nop,wscale 4>
22:22:07.424056 IP 10.0.20.88.80 > 172.16.20.100.53875: S 4671780:4671780(0) ack
998346085 win 4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392362490 67942058,sackOK,eol> 22:22:07.424776 IP 172.16.20.100.53875 > 10.0.20.88.80: . ack 1 win 365
<nop,nop,timestamp 67942058 2392362490>
22:22:07.424790 IP 172.16.20.100.53875 > 10.0.20.88.80: P 1:149(148) ack 1 win 365 <nop,nop,timestamp 67942058 2392362490> 22:22:07.424891 IP 10.0.20.88.80 > 172.16.20.100.53875: . ack 149 win 4528
<nop,nop,timestamp 2392362491 67942058>
22:22:12.024850 IP 10.0.20.88.80 > 172.16.20.100.53875: R 1:1(0) ack 149 win 4528
6 packets captured
6 packets received by filter
0 packets dropped by kernel
Trace on server side:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on internal, link-type EN10MB (Ethernet), capture size 96 bytes
22:22:07.424881 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win
4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392362491 0,sackOK,eol>
22:22:08.424893 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win 4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392363491 0,sackOK,eol>
22:22:09.625082 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win 4380 <mss 1460,nop,wscale 0,nop,nop,timestamp 2392364691 0,sackOK,eol>
22:22:10.825194 IP 172.16.20.100.53875 > 172.16.20.2.80: S 51116678:51116678(0) win 4380 <mss 1460,sackOK,eol>
4 packets captured 4 packets received by filter 0 packets dropped by kernel
What should the LTM Specialist do to solve the problem?

