GCCC Exam Question 11
Which of the following baselines is considered necessary to implement the Boundary Defense CIS Control?
GCCC Exam Question 12
An organization has implemented a control for Controlled Use of Administrative Privileges. They are collecting audit data for each login, logout, and location for the root account of their MySQL server, but they are unable to attribute each of these logins to a specific user. What action can they take to rectify this?
GCCC Exam Question 13
An auditor is validating the policies and procedures for an organization with respect to a control for Data Recovery. The organization's control states they will completely back up critical servers weekly, with incremental backups every four hours. Which action will best verify success of the policy?
GCCC Exam Question 14
An organization is implementing an application software security control their custom-written code that provides web-based database access to sales partners. Which action will help mitigate the risk of the application being compromised?
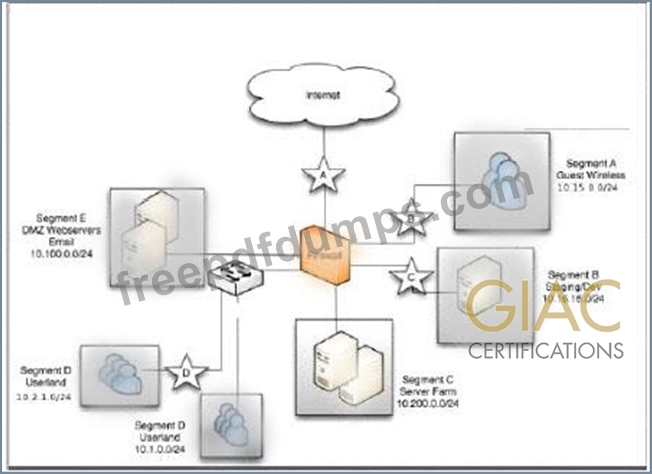
GCCC Exam Question 15
An organization has installed a firewall for Boundary Defense. It allows only outbound traffic from internal workstations for web and SSH, allows connections from the internet to the DMZ, and allows guest wireless access to the internet only. How can an auditor validate these rules?