HPE6-A71 Exam Question 76
An administrator configures an ArubaOS-Switch for per-user tunneled node. Which protocols does the switch use to establish and maintain a connection with the Aruba Mobility Controller (MC)? (Select two.)
HPE6-A71 Exam Question 77
Refer to the exhibit.

The administrator expects the AP to connect to a cluster, but the AP fails to connect. The administrator examines the configuration of an AP from apboot mode shown in the exhibit. What can the administrator determine about the configuration of the AP?

The administrator expects the AP to connect to a cluster, but the AP fails to connect. The administrator examines the configuration of an AP from apboot mode shown in the exhibit. What can the administrator determine about the configuration of the AP?
HPE6-A71 Exam Question 78
What is true about the operation of the Aruba Mobility Controller (MC) shown below?
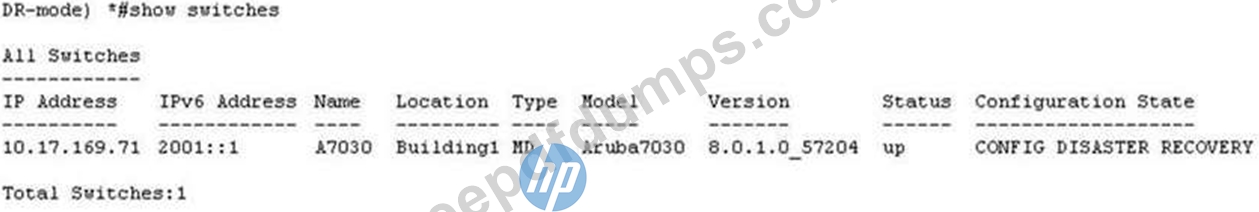

HPE6-A71 Exam Question 79
Refer to the exhibit.
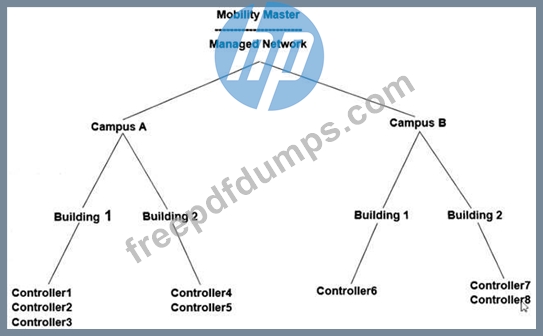
An administrator wants to centralize administrative access to the Aruba Mobility Controllers (MC) and Mobility Master (MM). ClearPass is set up and the preferred authentication protocol is TACACS+. Where should the administrator perform this configuration in the MM hierarchy shown in the exhibit?

An administrator wants to centralize administrative access to the Aruba Mobility Controllers (MC) and Mobility Master (MM). ClearPass is set up and the preferred authentication protocol is TACACS+. Where should the administrator perform this configuration in the MM hierarchy shown in the exhibit?
HPE6-A71 Exam Question 80
Refer to the exhibit.
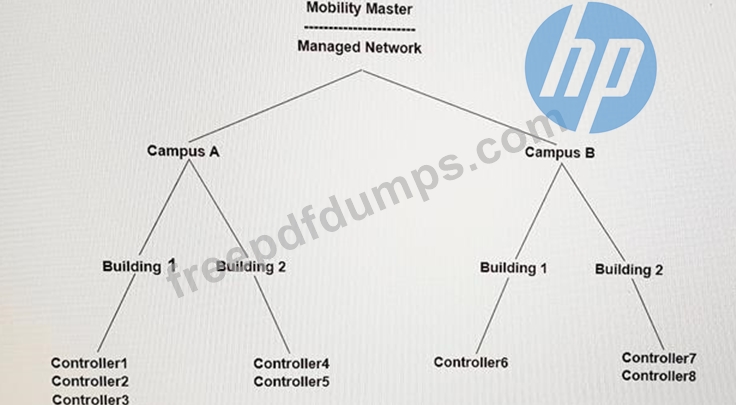
Anadministrator wants to centralize administrative access to the Aruba Mobility Controllers (MC) and Mobility Master (MM). ClearPass is set up and the preferred authentication protocols is TACACS+. Where should the administrator perform this configuration inthe MM hierarchy shown in the exhibit?

Anadministrator wants to centralize administrative access to the Aruba Mobility Controllers (MC) and Mobility Master (MM). ClearPass is set up and the preferred authentication protocols is TACACS+. Where should the administrator perform this configuration inthe MM hierarchy shown in the exhibit?

