H12-711_V3.0-ENU Exam Question 161
Which of the following is not a symmetric encryption algorithm?
H12-711_V3.0-ENU Exam Question 162
After a cyber-attack event occurs, set up an isolation area, summarize data, and estimate losses according to the plan. Which of the above actions belong to the work content of the cyber security emergency response?
H12-711_V3.0-ENU Exam Question 163
aboutVGMPIn a description of group management, which of the following is false?
H12-711_V3.0-ENU Exam Question 164
When configuring security policies, you can control traffic based on the user's______.[fill in the blank]*
H12-711_V3.0-ENU Exam Question 165
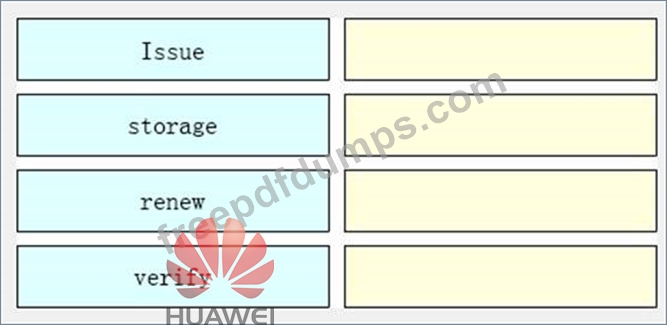
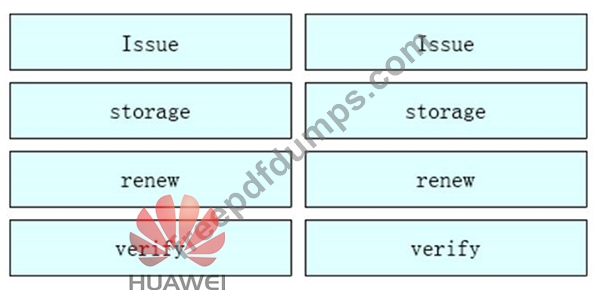
Please order the following steps about the PKI life cycle correctly