H12-722 Exam Question 16
Which two of the following options use similar attack methods and generate a large number of useless reply packets, occupying network bandwidth and consuming device resources?
H12-722 Exam Question 17
The following figure shows the configuration of the URL filtering configuration file. Which of the following statements is true about this configuration?
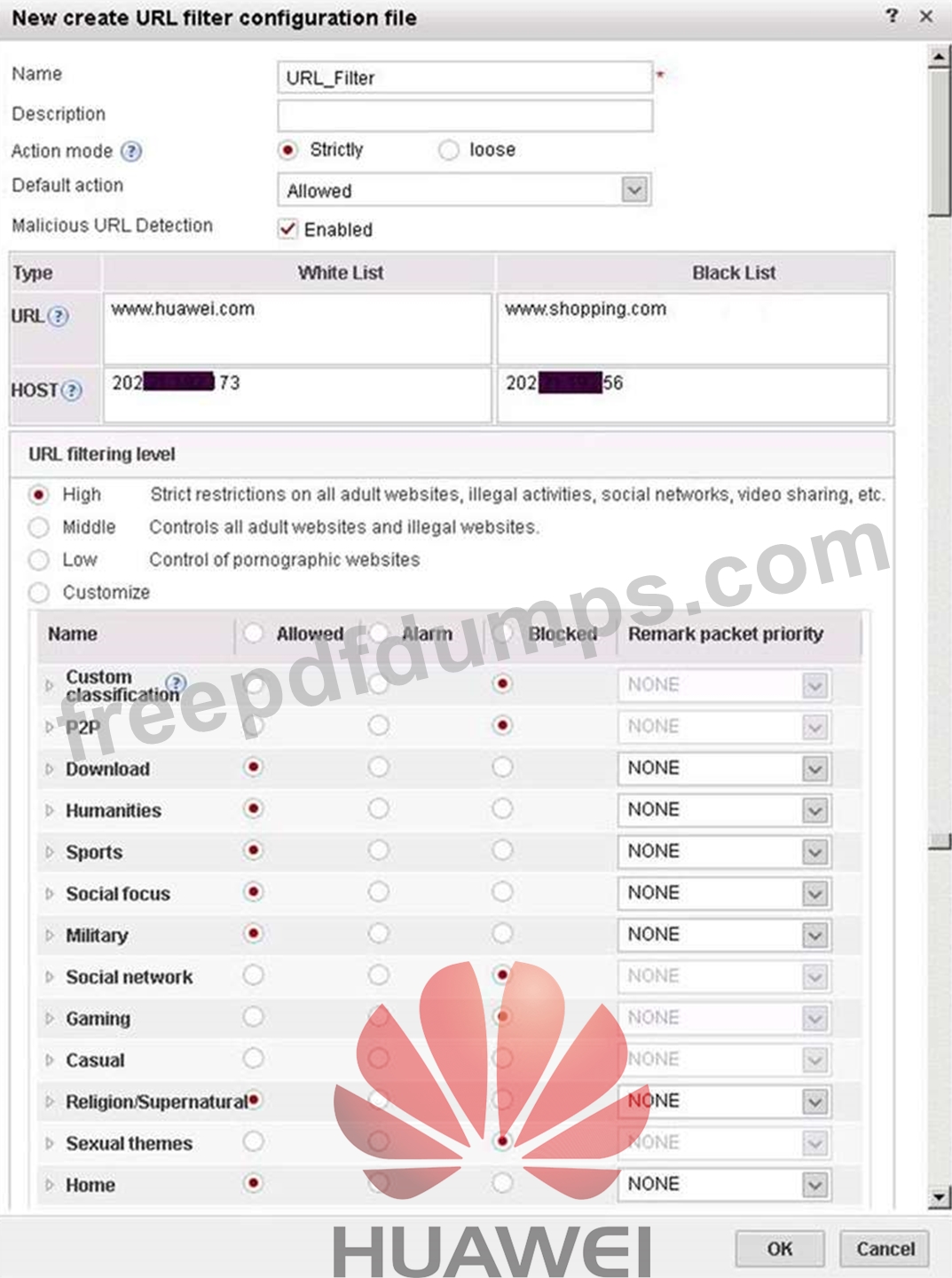

H12-722 Exam Question 18
The core technology of content security lies in anomaly detection, and the concept of defense lies in continuous monitoring and analysis.
H12-722 Exam Question 19
Threats detected by the big data intelligent security analysis platform will be synchronized to each network device at the same time C and then collected from the network device Collect it in the log for continuous learning and optimization.
H12-722 Exam Question 20
The processing flow of IPS has the following steps;
1. Reorganize application data
2. Match the signature
3. Message processing
4. Protocol identification
Which of the following is the correct order of the processing flow?
1. Reorganize application data
2. Match the signature
3. Message processing
4. Protocol identification
Which of the following is the correct order of the processing flow?

