CISA Exam Question 76
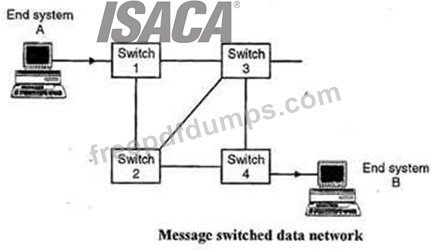
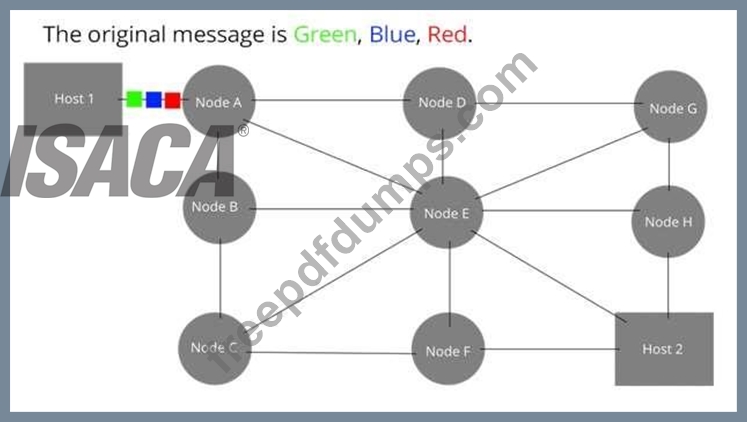
Identify the WAN message switching technique being used from the description presented below:
"Data is routed in its entirety from the source node to the destination node, one hope at a time. During message routing, every intermediate switch in the network stores the whole message. If the entire network's resources are engaged or the network becomes blocked, this WAN switching technology stores and delays the message until ample resources become available for effective transmission of the message. "
"Data is routed in its entirety from the source node to the destination node, one hope at a time. During message routing, every intermediate switch in the network stores the whole message. If the entire network's resources are engaged or the network becomes blocked, this WAN switching technology stores and delays the message until ample resources become available for effective transmission of the message. "
CISA Exam Question 77
Which of the following is the GREATEST benefit of implementing an incident management process?
CISA Exam Question 78
Which of the following forms of evidence for the auditor would be considered the MOST reliable?
CISA Exam Question 79
An IS auditor is reviewing the remote access methods of a company used to access system remotely.
Which of the following is LEAST preferred remote access method from a security and control point of view?
Which of the following is LEAST preferred remote access method from a security and control point of view?
CISA Exam Question 80
A company has implemented an IT segregation of duties policy In a role-based environment, which of the following roles may be assigned to an application developer?