CRISC Exam Question 386
Which of the following statements are true for enterprise's risk management capability maturity level 3?
CRISC Exam Question 387
Which of the following is MOST important for an organization to consider when developing its IT strategy?
CRISC Exam Question 388
The analysis of which of the following will BEST help validate whether suspicious network activity is malicious?
CRISC Exam Question 389
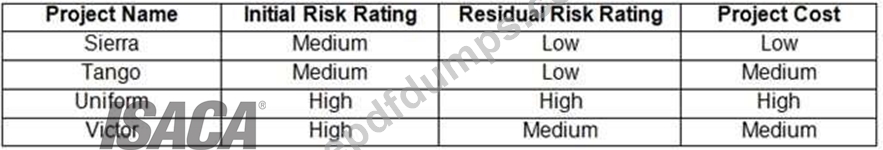
What can be determined from the risk scenario chart?

CRISC Exam Question 390
One of an organization's key IT systems cannot be patched because the patches interfere with critical business application functionalities. Which of the following would be the risk practitioner's BEST recommendation?


