CRISC Exam Question 61
Which of the following should be done FIRST when developing a data protection management plan?
Correct Answer: B
A data protection management plan is a document that outlines how an organization will protect its sensitive data from unauthorized access, use, disclosure, or loss. A data protection management plan should include the following components1:
* The scope and objectives of the data protection management plan, and how it aligns with the organization's data protection policy and strategy
* The roles and responsibilities of the data protection team and other stakeholders, and how they will communicate and coordinate
* The data protection risks and threats that the organization faces, and how they will be assessed and prioritized
* The data protection controls and measures that the organization will implement and maintain, and how they will be monitored and evaluated
* The data protection incidents and breaches that the organization may encounter, and how they will be reported and resolved
* The data protection training and awareness programs that the organization will provide and conduct, and how they will be measured and improved The first step that should be done when developing a data protection management plan is to identify critical data. This means that the organization should:
* Define what constitutes sensitive data in the organization, such as personal data, confidential data, or regulated data
* Identify and classify the sensitive data that the organization collects, processes, stores, or transfers, and assign appropriate labels or tags
* Determine the value and importance of the sensitive data to the organization and its stakeholders, and the potential impacts or consequences of data loss or compromise
* Map the data flows and locations of the sensitive data within the organization and across its partners or vendors, and document the data lifecycle stages and activities By identifying critical data, the organization can:
* Establish a clear and consistent understanding of the data protection scope and objectives, and ensure that they are relevant and realistic
* Provide a comprehensive and accurate data inventory that can support the data protection risk assessment and control implementation
* Identify and prioritize the data protection needs and requirements of the organization and its stakeholders, and align them with the data protection laws and standards
* Communicate and report the data protection status and performance to the stakeholders and regulators, and ensure transparency and accountability References = Guide to Developing a Data Protection Management Programme
* The scope and objectives of the data protection management plan, and how it aligns with the organization's data protection policy and strategy
* The roles and responsibilities of the data protection team and other stakeholders, and how they will communicate and coordinate
* The data protection risks and threats that the organization faces, and how they will be assessed and prioritized
* The data protection controls and measures that the organization will implement and maintain, and how they will be monitored and evaluated
* The data protection incidents and breaches that the organization may encounter, and how they will be reported and resolved
* The data protection training and awareness programs that the organization will provide and conduct, and how they will be measured and improved The first step that should be done when developing a data protection management plan is to identify critical data. This means that the organization should:
* Define what constitutes sensitive data in the organization, such as personal data, confidential data, or regulated data
* Identify and classify the sensitive data that the organization collects, processes, stores, or transfers, and assign appropriate labels or tags
* Determine the value and importance of the sensitive data to the organization and its stakeholders, and the potential impacts or consequences of data loss or compromise
* Map the data flows and locations of the sensitive data within the organization and across its partners or vendors, and document the data lifecycle stages and activities By identifying critical data, the organization can:
* Establish a clear and consistent understanding of the data protection scope and objectives, and ensure that they are relevant and realistic
* Provide a comprehensive and accurate data inventory that can support the data protection risk assessment and control implementation
* Identify and prioritize the data protection needs and requirements of the organization and its stakeholders, and align them with the data protection laws and standards
* Communicate and report the data protection status and performance to the stakeholders and regulators, and ensure transparency and accountability References = Guide to Developing a Data Protection Management Programme
CRISC Exam Question 62
The number of tickets to rework application code has significantly exceeded the established threshold. Which of the following would be the risk practitioner s BEST recommendation?
Correct Answer: A
* A root cause analysis is a process of identifying and understanding the underlying or fundamental causes or factors that contribute to or result in a problem or incident that has occurred or may occur in the organization. A root cause analysis can provide useful insights and solutions on the origin and nature of the problem or incident, and prevent or reduce its recurrence or impact.
* Performing a root cause analysis is the risk practitioner's best recommendation when the number of tickets to rework application code has significantly exceeded the established threshold, because it can help the organization to address the following questions:
* Why did the application code require rework?
* What were the errors or defects in the application code?
* How did the errors or defects affect the functionality or usability of the application?
* Who was responsible or accountable for the application code development and testing?
* When and how were the errors or defects detected and reported?
* What were the costs or consequences of the rework for the organization and its stakeholders?
* How can the errors or defects be prevented or minimized in the future?
* Performing a root cause analysis can help the organization to improve and optimize the application code quality and performance, and to reduce or eliminate the need for rework. It can also help the organization to align the application code development and testing with the organization's objectives and requirements, and to comply with the organization's policies and standards.
* The other options are not the risk practitioner's best recommendations when the number of tickets to rework application code has significantly exceeded the established threshold, because they do not address the main purpose and benefit of performing a root cause analysis, which is to identify and understand the underlying or fundamental causes or factors that contribute to or result in the problem or incident.
* Performing a code review is a process of examining and evaluating the application code for its quality, functionality, and security, using the input and feedback from the peers, experts, or tools.
Performing a code review can help the organization to identify and resolve the errors or defects in the application code, but it is not the risk practitioner's best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders.
* Implementing version control software is a process of using a software tool to manage and track the changes and modifications to the application code, and to ensure the consistency and integrity of the application code. Implementing version control software can help the organization to control and monitor the application code development and testing, but it is not the risk practitioner's best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders.
* Implementing training on coding best practices is a process of providing and facilitating the learning and development of the skills and knowledge on the principles, guidelines, and standards for the application code development and testing. Implementing training on coding best practices can help the organization to enhance the competence and performance of the application code developers and testers, but it is not the risk practitioner's best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders. References =
* ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
* ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 189
* CRISC Practice Quiz and Exam Prep
* Performing a root cause analysis is the risk practitioner's best recommendation when the number of tickets to rework application code has significantly exceeded the established threshold, because it can help the organization to address the following questions:
* Why did the application code require rework?
* What were the errors or defects in the application code?
* How did the errors or defects affect the functionality or usability of the application?
* Who was responsible or accountable for the application code development and testing?
* When and how were the errors or defects detected and reported?
* What were the costs or consequences of the rework for the organization and its stakeholders?
* How can the errors or defects be prevented or minimized in the future?
* Performing a root cause analysis can help the organization to improve and optimize the application code quality and performance, and to reduce or eliminate the need for rework. It can also help the organization to align the application code development and testing with the organization's objectives and requirements, and to comply with the organization's policies and standards.
* The other options are not the risk practitioner's best recommendations when the number of tickets to rework application code has significantly exceeded the established threshold, because they do not address the main purpose and benefit of performing a root cause analysis, which is to identify and understand the underlying or fundamental causes or factors that contribute to or result in the problem or incident.
* Performing a code review is a process of examining and evaluating the application code for its quality, functionality, and security, using the input and feedback from the peers, experts, or tools.
Performing a code review can help the organization to identify and resolve the errors or defects in the application code, but it is not the risk practitioner's best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders.
* Implementing version control software is a process of using a software tool to manage and track the changes and modifications to the application code, and to ensure the consistency and integrity of the application code. Implementing version control software can help the organization to control and monitor the application code development and testing, but it is not the risk practitioner's best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders.
* Implementing training on coding best practices is a process of providing and facilitating the learning and development of the skills and knowledge on the principles, guidelines, and standards for the application code development and testing. Implementing training on coding best practices can help the organization to enhance the competence and performance of the application code developers and testers, but it is not the risk practitioner's best recommendation, because it does not indicate why the application code required rework, and how the errors or defects affected the organization and its stakeholders. References =
* ISACA, CRISC Review Manual, 7th Edition, 2022, pp. 40-41, 47-48, 54-55, 58-59, 62-63
* ISACA, CRISC Review Questions, Answers & Explanations Database, 2022, QID 189
* CRISC Practice Quiz and Exam Prep
CRISC Exam Question 63
A newly hired risk practitioner finds that the risk register has not been updated in the past year. What is the risk practitioner's BEST course of action?
Correct Answer: A
The best course of action for a newly hired risk practitioner who finds that the risk register has not been updated in the past year is to identify changes in risk factors and initiate risk reviews. This would help the risk practitioner to update the risk register with the current and relevant information on the risks facing the enterprise, such as their sources, drivers, indicators, likelihood, impact, and responses. It would also help the risk practitioner to evaluate the effectiveness of the existing controls, and to identify any new or emerging risks that need to be addressed. Identifying changes in risk factors and initiating risk reviews would enable the risk practitioner to maintain the accuracy and completeness of the risk register, and to provide valuable input for the risk management process. References = Risk and Information Systems Control Study Manual, 7th Edition, Chapter 5, Section 5.1.1, page 2271
CRISC Exam Question 64
Which of the following contributes MOST to the effective implementation of risk responses?
Correct Answer: C
Appropriate resources contribute most to the effective implementation of risk responses. Resources include people, time, money, equipment, and materials that are needed to execute the risk responses. Without appropriate resources, the risk responses may not be implemented properly, timely, or efficiently, and may not achieve the desired outcomes. The other options are not as important as appropriate resources, as they are related to the understanding, comparison, or documentation of the risk responses, which are less critical than the execution of the risk responses. References = Risk and Information Systems Control Study Manual, Chapter 3: IT Risk Response, Section 3.3: IT Risk Response Implementation, page 145.
CRISC Exam Question 65
After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments:
Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor's control environment?
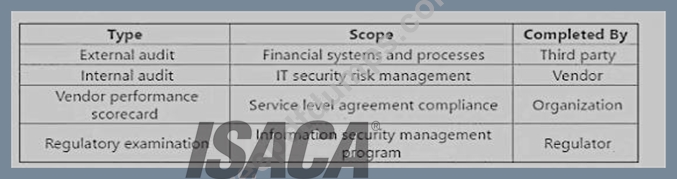
Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor's control environment?

Correct Answer: A
An external audit is the most reliable input to evaluate residual risk in the vendor's control environment, as it provides an independent and objective assessment of the vendor's financial systems and processes. An external audit is conducted by a third party, such as a certified public accountant (CPA) or a professional auditing firm, that follows the generally accepted auditing standards (GAAS) and the generally accepted accounting principles (GAAP). An external audit can help to verify the accuracy and completeness of the vendor's financial statements, identify any material misstatements or errors, and evaluate the effectiveness and efficiency of the vendor's internal controls. An external audit can also provide assurance and confidence to the organization and other stakeholders that the vendor is complying with the relevant laws, regulations, and contractual obligations.
The other options are not the most reliable inputs to evaluate residual risk in the vendor's control environment. An internal audit is conducted by the vendor itself, which may introduce bias or conflict of interest. An internal audit may also have a different scope, methodology, or quality than an external audit. A vendor performance scorecard is completed by the organization, which may not have the sufficient access, expertise, or authority to assess the vendor's control environment. A vendor performance scorecard may also focus more on the service level agreement (SLA) compliance, rather than the financial systems and processes.
A regulatory examination is conducted by a regulator, such as a government agency or a standard-setting body, which may have a different purpose, criteria, or perspective than the organization. A regulatory examination may also have a limited scope, frequency, or transparency. References = Guide to Vendor Risk Assessment | Smartsheet, Understanding Inherent Vs. Residual Risk Assessments - Resolver, Assessing Internal Controls over Compliance - HCCA Official Site
The other options are not the most reliable inputs to evaluate residual risk in the vendor's control environment. An internal audit is conducted by the vendor itself, which may introduce bias or conflict of interest. An internal audit may also have a different scope, methodology, or quality than an external audit. A vendor performance scorecard is completed by the organization, which may not have the sufficient access, expertise, or authority to assess the vendor's control environment. A vendor performance scorecard may also focus more on the service level agreement (SLA) compliance, rather than the financial systems and processes.
A regulatory examination is conducted by a regulator, such as a government agency or a standard-setting body, which may have a different purpose, criteria, or perspective than the organization. A regulatory examination may also have a limited scope, frequency, or transparency. References = Guide to Vendor Risk Assessment | Smartsheet, Understanding Inherent Vs. Residual Risk Assessments - Resolver, Assessing Internal Controls over Compliance - HCCA Official Site
- Other Version
- 3087ISACA.CRISC.v2025-01-04.q999
- 1388ISACA.CRISC.v2024-06-13.q683
- 2071ISACA.CRISC.v2024-04-02.q999
- 2668ISACA.CRISC.v2023-07-10.q544
- 5391ISACA.CRISC.v2022-05-25.q338
- 76ISACA.Actual4dump.CRISC.v2022-04-12.by.newman.349q.pdf
- 5199ISACA.CRISC.v2022-02-22.q349
- 5034ISACA.CRISC.v2021-10-27.q295
- 42ISACA.Updatedumps.CRISC.v2021-09-05.by.bonnie.114q.pdf
- Latest Upload
- 238ISACA.CGEIT.v2025-09-19.q537
- 153Fortinet.FCP_FWF_AD-7.4.v2025-09-18.q62
- 153Scrum.SAFe-Practitioner.v2025-09-18.q63
- 143Workday.Workday-Prism-Analytics.v2025-09-17.q17
- 131Oracle.1Z0-1055-24.v2025-09-17.q28
- 128Oracle.1Z1-182.v2025-09-17.q32
- 240Nutanix.NCP-US-6.5.v2025-09-16.q73
- 263Oracle.1z0-071.v2025-09-16.q232
- 202Oracle.1Z1-922.v2025-09-16.q125
- 318CyberArk.PAM-CDE-RECERT.v2025-09-15.q100
[×]
Download PDF File
Enter your email address to download ISACA.CRISC.v2025-08-27.q675 Practice Test

