JN0-348 Exam Question 71
Which two statements are true about a unified ISSU? (Choose two.)
JN0-348 Exam Question 72
Click the Exhibit button.
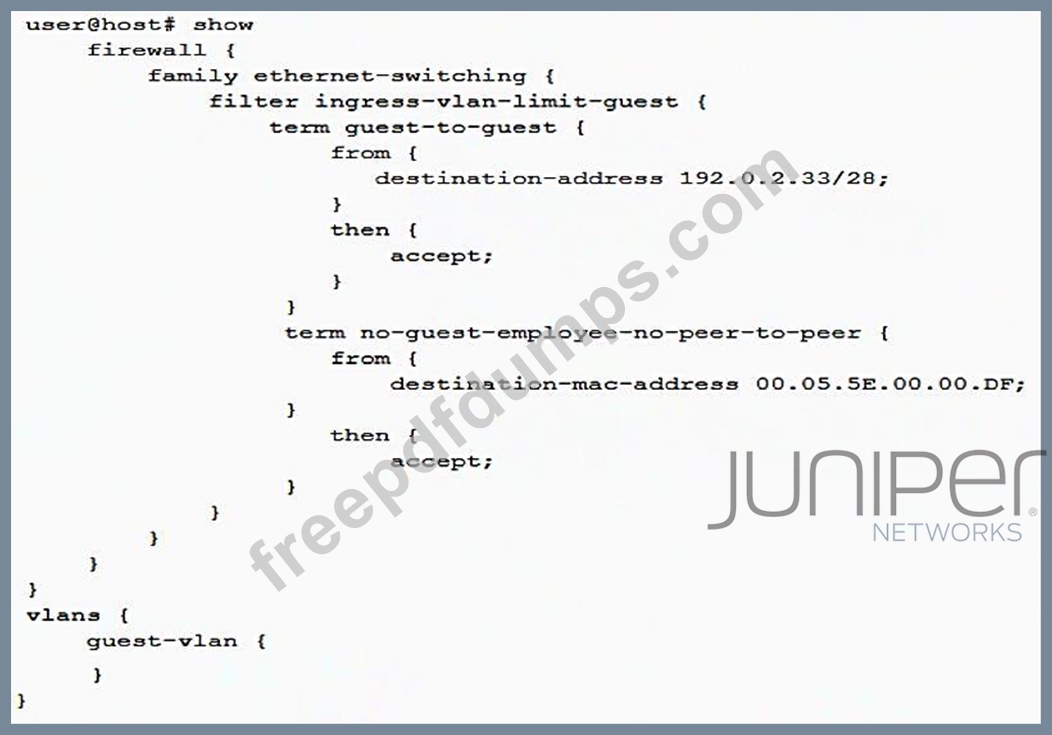
A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic.
In this scenario, what must you do to implement the security policy?

A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic.
In this scenario, what must you do to implement the security policy?
JN0-348 Exam Question 73
You have configured the route with an IS-IS metric of 2048. However, the IS-IS interface metric of 63 is being applied for the interface of this router.
What must you do to enable larger metric value?
What must you do to enable larger metric value?
JN0-348 Exam Question 74
There is a GRE tunnel configured over the Internet between Router-1 and Router-2. An OSPF adjacency is configured over this GRE tunnel. However, the OSPF adjacency briefly reaches the Full state before it is torn down. This cycle repeats indefinitely.
Which two actions would you perform to solve this problem? (Choose two.)
Which two actions would you perform to solve this problem? (Choose two.)
JN0-348 Exam Question 75
You must implement filter-based forwarding. You need to direct traffic from 192.168.1.0/24 through vr1 and traffic from 10.210.0.128/26 through vr2.
Which configuration is correct in this scenario?
Which configuration is correct in this scenario?

