98-367 Exam Question 41
What are three examples of two-factor authentication? (Choose three.)
98-367 Exam Question 42
Which of the following is a technique used to attack an Ethernet wired or wireless network?
98-367 Exam Question 43
Which of the following steps will help in system or host hardening? Each correct answer represents a complete solution. Choose two.
98-367 Exam Question 44
You work as a Network Administrator for TechMart Inc. The company has a Windows-based network. After completing a security audit of the company's Microsoft Windows Server 2008 R2 file servers, you have determined that folder and share security requires a revision on the basis of corporate reorganization. You have noticed that some shares on the file system are not secured. Which of the following will you use to prevent unauthorized changes to computers on the domain?
98-367 Exam Question 45
You are setting up Remote Desktop on your computer. Your computer is a member of a domain.
Your firewall configuration is shown in the following image:
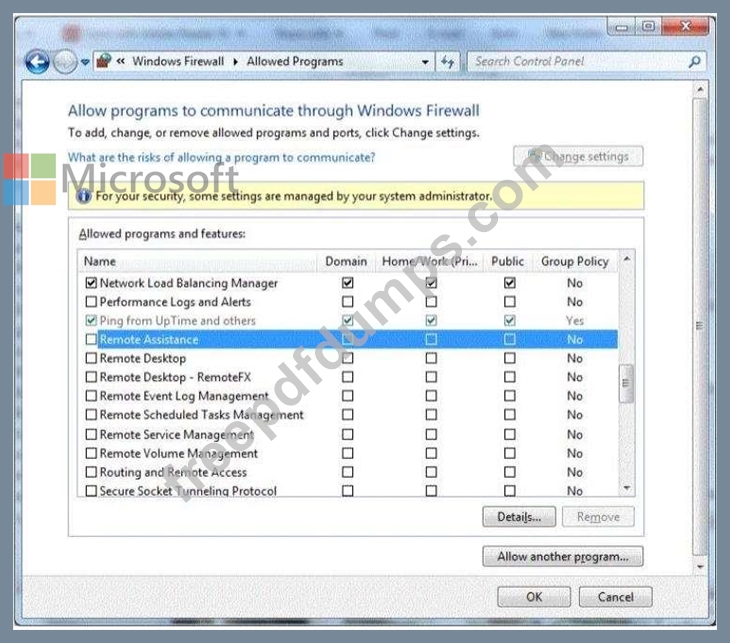
You need to allow Remote Desktop to be able to get through your firewall for users on your company's network.
Which settings should you enable?
Your firewall configuration is shown in the following image:

You need to allow Remote Desktop to be able to get through your firewall for users on your company's network.
Which settings should you enable?


