98-367 Exam Question 76
HOTSPOT
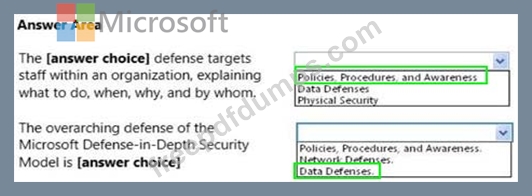
You are an intern for a company where your manager wants to be sure you understand the social engineering threats that may occur. Your manager emphasizes the principles of the Microsoft Defense-in-Depth Security Model shown in the following image: Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
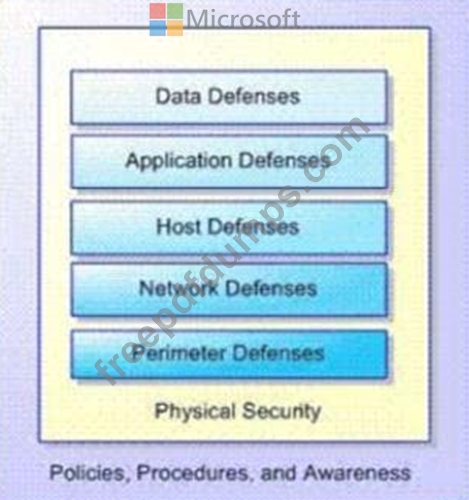


You are an intern for a company where your manager wants to be sure you understand the social engineering threats that may occur. Your manager emphasizes the principles of the Microsoft Defense-in-Depth Security Model shown in the following image: Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.



98-367 Exam Question 77
Mark works as a Systems Administrator for TechMart Inc. The company has a Windows-based network. The company is adding an open, high-speed, wireless access for their customers secured wireless for employees at all 37 branches. He wants to check the various security concerns for ensuring that business traffic is secured. He is also under pressure to make this new feature a winning strategy for a company. In which of the following ways can Mark add another level of security after implanting encryption techniques for the business wireless traffic? Each correct answer represents a complete solution. Choose all that apply.
98-367 Exam Question 78
Which of the following areas of a network contains DNS serversWeb servers for Internet users?
98-367 Exam Question 79
Setting a database to run on a cluster of servers is an example of applying:
98-367 Exam Question 80
Which two characteristics should you recommend for a user's domain password? (Choose two.)