AI-100 Exam Question 11
Your company uses several dots The bots use Azure Bot Service.
Several users report that some of the bots fail to return the expected results.
You plan to view the service health of the hot service.
You need 10 request the appropriate role to access the service health of the bot service. The solution must use the principle of least privilege.
Which role should you request?
Several users report that some of the bots fail to return the expected results.
You plan to view the service health of the hot service.
You need 10 request the appropriate role to access the service health of the bot service. The solution must use the principle of least privilege.
Which role should you request?
AI-100 Exam Question 12
You are designing a Custom Visions Service solution to identify fresh produce in grocery stores. The solution will be deployed as part of a mobile app.
You need to recommend the configuration for the Custom Vision API. The solution must minimize the size of the mobile app.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to recommend the configuration for the Custom Vision API. The solution must minimize the size of the mobile app.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AI-100 Exam Question 13
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have Azure IoT Edge devices that generate streaming data.
On the devices, you need to detect anomalies in the data by using Azure Machine Learning models.
Once an anomaly is detected, the devices must add information about the anomaly to the Azure IoT Hub stream.
Solution: You deploy Azure Stream Analytics as an IoT Edge module.
Does this meet the goal?
After you answer a question, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have Azure IoT Edge devices that generate streaming data.
On the devices, you need to detect anomalies in the data by using Azure Machine Learning models.
Once an anomaly is detected, the devices must add information about the anomaly to the Azure IoT Hub stream.
Solution: You deploy Azure Stream Analytics as an IoT Edge module.
Does this meet the goal?
AI-100 Exam Question 14
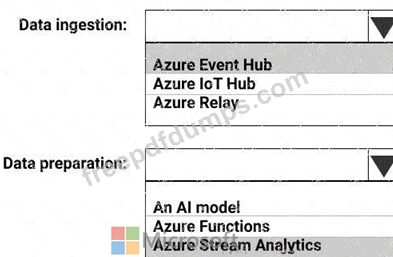
You are designing a solution that will analyze bank transactions in real time. The transactions will be evaluated by using an algorithm and classified into one of five groups. The transaction data will be enriched with information taken from Azure SQL Database before the transactions are sent to the classification process.
The enrichment process will require custom code. Data from different banks will require different stored procedures.
You need to develop a pipeline for the solution.
Which components should you use for data ingestion and data preparation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

The enrichment process will require custom code. Data from different banks will require different stored procedures.
You need to develop a pipeline for the solution.
Which components should you use for data ingestion and data preparation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AI-100 Exam Question 15
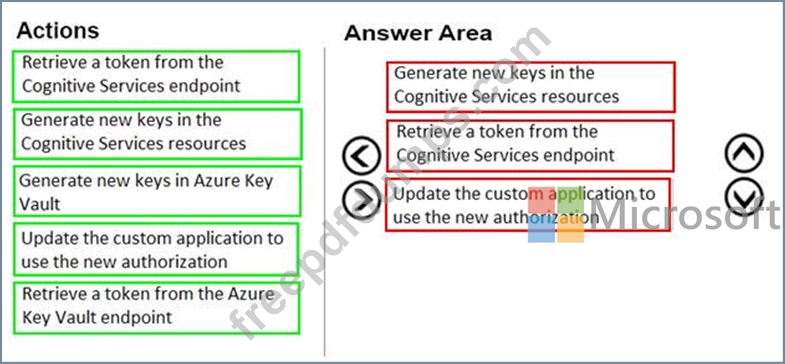
You develop a custom application that uses a token to connect to Azure Cognitive Services resources.
A new security policy requires that all access keys are changed every 30 days.
You need to recommend a solution to implement the security policy.
Which three actions should you recommend be performed every 30 days? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
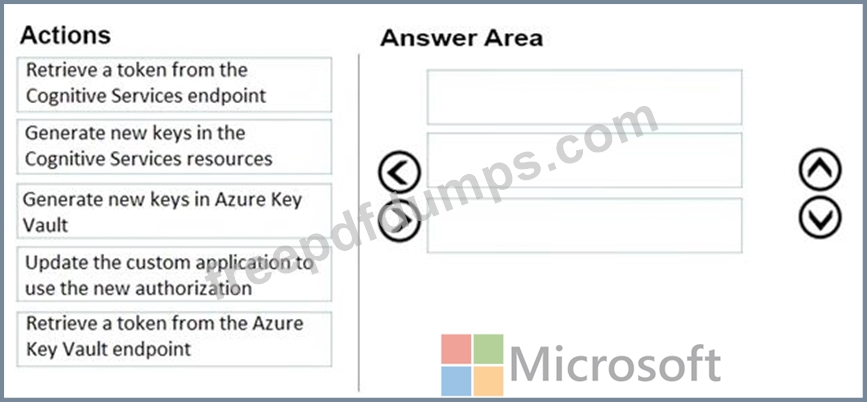
A new security policy requires that all access keys are changed every 30 days.
You need to recommend a solution to implement the security policy.
Which three actions should you recommend be performed every 30 days? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.