AZ-303 Exam Question 1
You create the Azure resources shown in the following table.
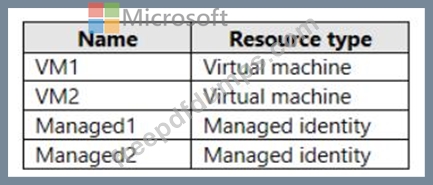
You attempt to add a role assignment to a resource group as shown in the following exhibit.
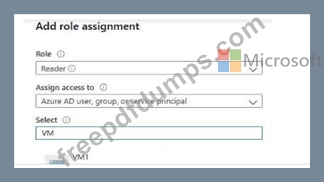
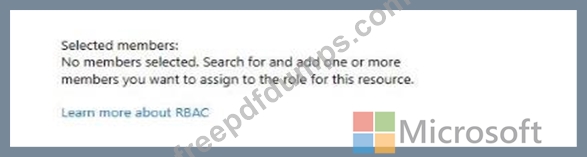
What should you do to ensure that you can assign VM2 the Reader role for the resource group?

You attempt to add a role assignment to a resource group as shown in the following exhibit.


What should you do to ensure that you can assign VM2 the Reader role for the resource group?
AZ-303 Exam Question 2
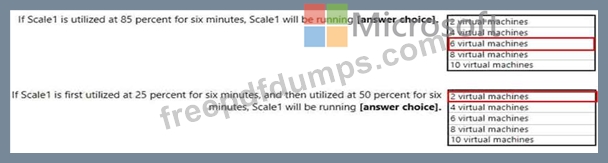
You create a virtual machine scale set named Scale1. Scale1 is configured as shown in the following exhibit.
The subscription contains the Azure SQL databases shown in the following table.
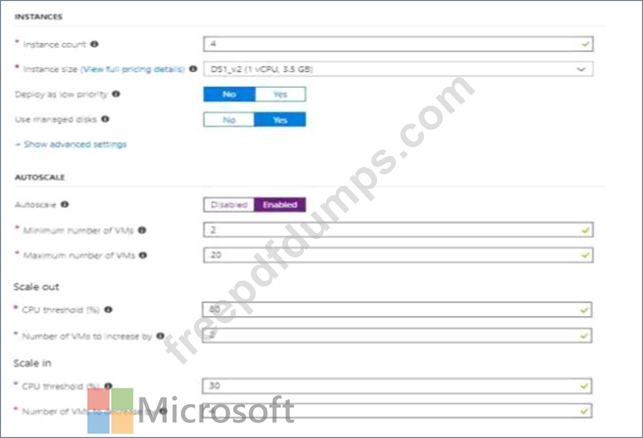
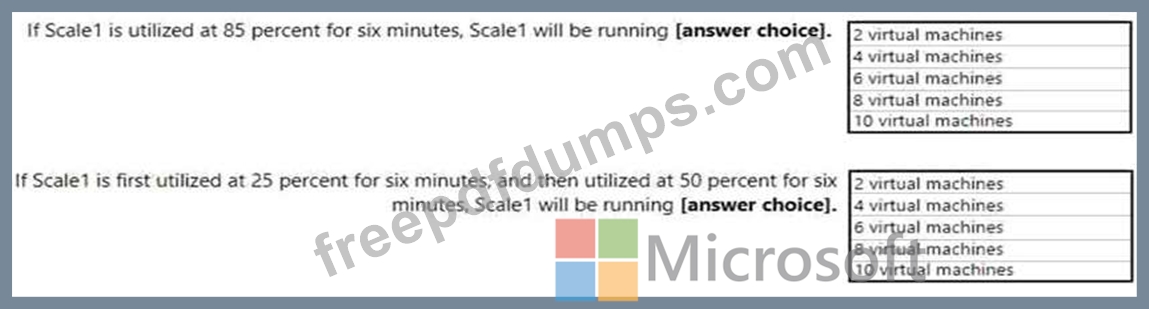
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
The subscription contains the Azure SQL databases shown in the following table.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

AZ-303 Exam Question 3
You have an on-premises virtual machine named VM1 configured as shown in the following exhibit.
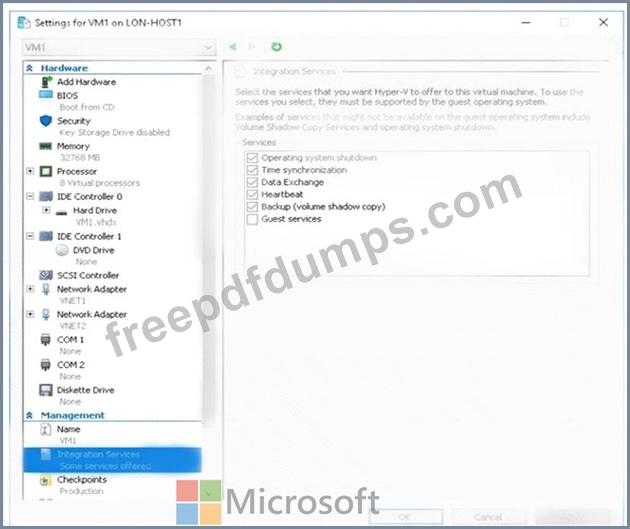
VM is started.
You need to create a new virtual machine image in Azure from VM1.
Which three actions should you perform before you create the new image? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.

VM is started.
You need to create a new virtual machine image in Azure from VM1.
Which three actions should you perform before you create the new image? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
AZ-303 Exam Question 4
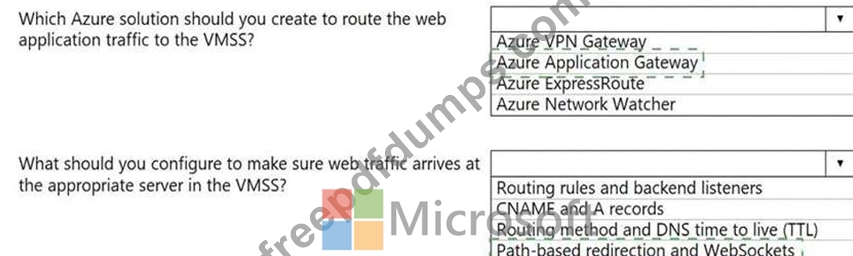
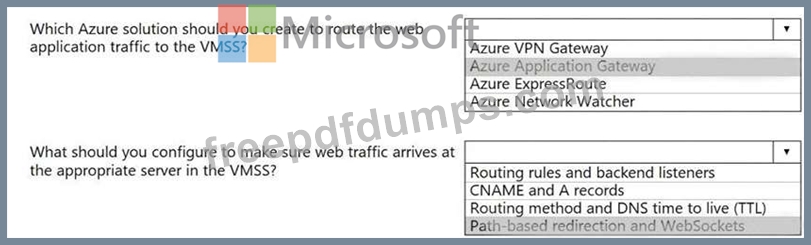
Your company hosts multiple websites by using Azure virtual machine scale sets (VMSS) that run Internet Information Server (IIS).
All network communications must be secured by using end to end Secure Socket Layer (SSL) encryption.
User sessions must be routed to the same server by using cookie-based session affinity.
The image shown depicts the network traffic flow for the websites to the VMSS.

Use the drop-down menus to select the answer choice that answers each question.
NOTE: Each correct selection is worth one point.
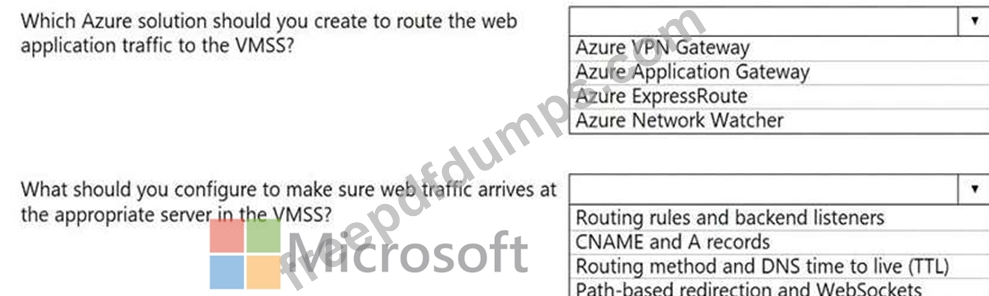
All network communications must be secured by using end to end Secure Socket Layer (SSL) encryption.
User sessions must be routed to the same server by using cookie-based session affinity.
The image shown depicts the network traffic flow for the websites to the VMSS.

Use the drop-down menus to select the answer choice that answers each question.
NOTE: Each correct selection is worth one point.

AZ-303 Exam Question 5
You have 10 Azure virtual machines on a subnet named Subnet1. Subnet1 is on a virtual network named VNet1.
You plan to deploy a public Azure Standard Load Balancer named LB1 to the same Azure region as the 10 virtual machines.
You need to ensure that traffic from all the virtual machines to the internet flows through LB1. The solution must prevent the virtual machines from being accessible on the internet.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You plan to deploy a public Azure Standard Load Balancer named LB1 to the same Azure region as the 10 virtual machines.
You need to ensure that traffic from all the virtual machines to the internet flows through LB1. The solution must prevent the virtual machines from being accessible on the internet.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.