AZ-400 Exam Question 31
Task 7
You need to prepare a network security group (NSG) named az400 38443478 nsgl to host an Azure DevOps pipeline agent. The solution must allow only the required outbound port for Azure DevOps and deny all other inbound and outbound access to the Internet See the solution below in explanation.
You need to prepare a network security group (NSG) named az400 38443478 nsgl to host an Azure DevOps pipeline agent. The solution must allow only the required outbound port for Azure DevOps and deny all other inbound and outbound access to the Internet See the solution below in explanation.
AZ-400 Exam Question 32
Your company uses Azure Artifacts for package management.
You need to configure an upstream source in Azure Artifacts for Python packages.
Which repository type should you use as an upstream source?
You need to configure an upstream source in Azure Artifacts for Python packages.
Which repository type should you use as an upstream source?
AZ-400 Exam Question 33
You have a GitHub repository that contains the source code for an app.
You need to identify all the changes made between versions 1.4.16 and 1.6.12 of the source code.
How should you complete the Get command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Git _________ ____________ | helper-script > changes.txt
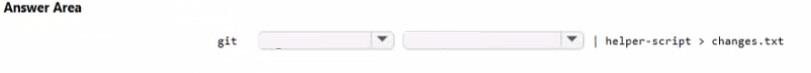
You need to identify all the changes made between versions 1.4.16 and 1.6.12 of the source code.
How should you complete the Get command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Git _________ ____________ | helper-script > changes.txt

AZ-400 Exam Question 34
You are deploying a new application that uses Azure virtual machines.
You plan to use the Desired State Configuration (DSC) extension on the virtual machines.
You need to ensure that the virtual machines always have the same Windows features installed.
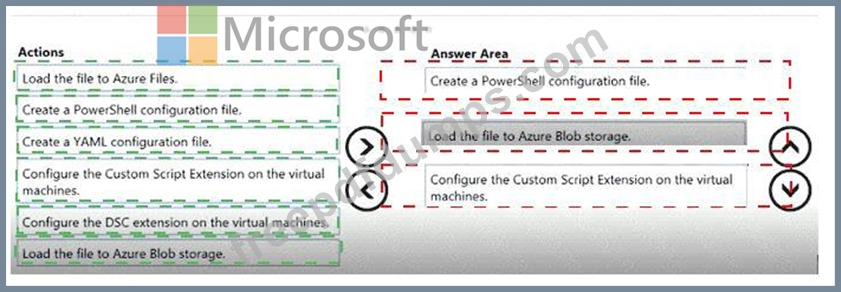
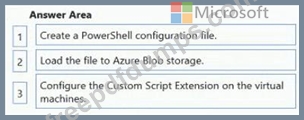
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
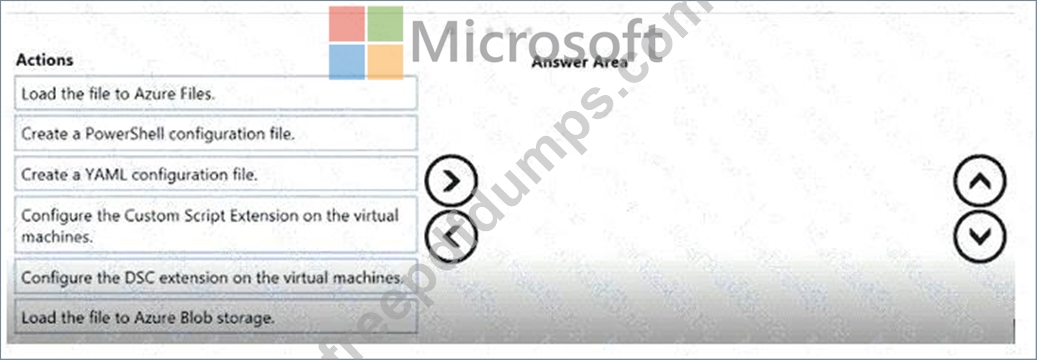
You plan to use the Desired State Configuration (DSC) extension on the virtual machines.
You need to ensure that the virtual machines always have the same Windows features installed.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-400 Exam Question 35
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You plan to update the Azure DevOps strategy of your company.
You need to identify the following issues as they occur during the company's development process:
* Licensing violations
* Prohibited libraries
Solution: You implement automated security testing.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You plan to update the Azure DevOps strategy of your company.
You need to identify the following issues as they occur during the company's development process:
* Licensing violations
* Prohibited libraries
Solution: You implement automated security testing.
Does this meet the goal?