AZ-801 Exam Question 16
Your network contains an Active Directory Domain Services (AD DS) domain.
You need to implement a solution that meets the following requirements:
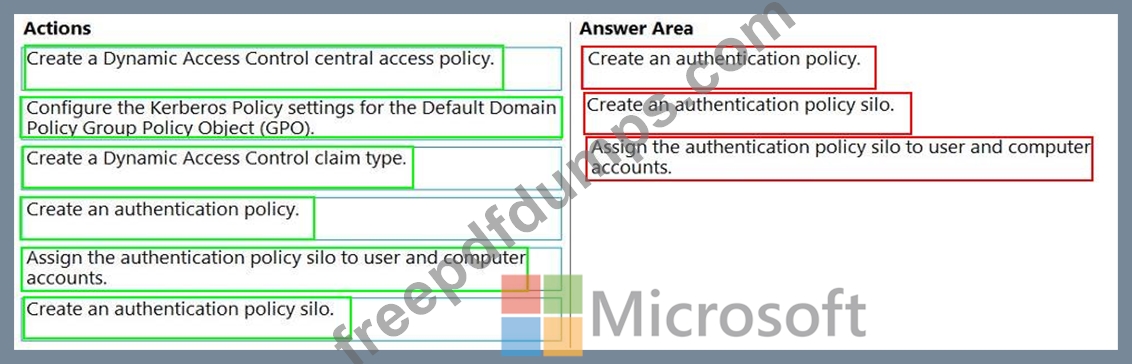
Ensures that the members of the Domain Admins group are allowed to sign in only to domain controllers Ensures that the lifetime of Kerberos Ticket Granting Ticket (TGT) for the members of the Domain Admins group is limited to one hour Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You need to implement a solution that meets the following requirements:
Ensures that the members of the Domain Admins group are allowed to sign in only to domain controllers Ensures that the lifetime of Kerberos Ticket Granting Ticket (TGT) for the members of the Domain Admins group is limited to one hour Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-801 Exam Question 17
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
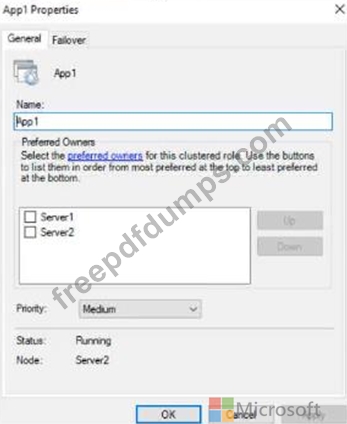
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
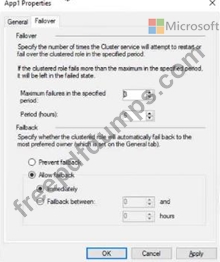
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the General settings, you move Server2 up.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)

The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)

Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the General settings, you move Server2 up.
Does this meet the goal?
AZ-801 Exam Question 18
You have a Microsoft Sentinel deployment and 100 Azure Arc-enabled on-premises servers. All the Azure Arc-enabled resources are in the same resource group.
You need to onboard the servers to Microsoft Sentinel. The solution must minimize administrative effort.
What should you use to onboard the servers to Microsoft Sentinel?
You need to onboard the servers to Microsoft Sentinel. The solution must minimize administrative effort.
What should you use to onboard the servers to Microsoft Sentinel?
AZ-801 Exam Question 19
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Tamper Protection.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Tamper Protection.
Does this meet the goal?
AZ-801 Exam Question 20
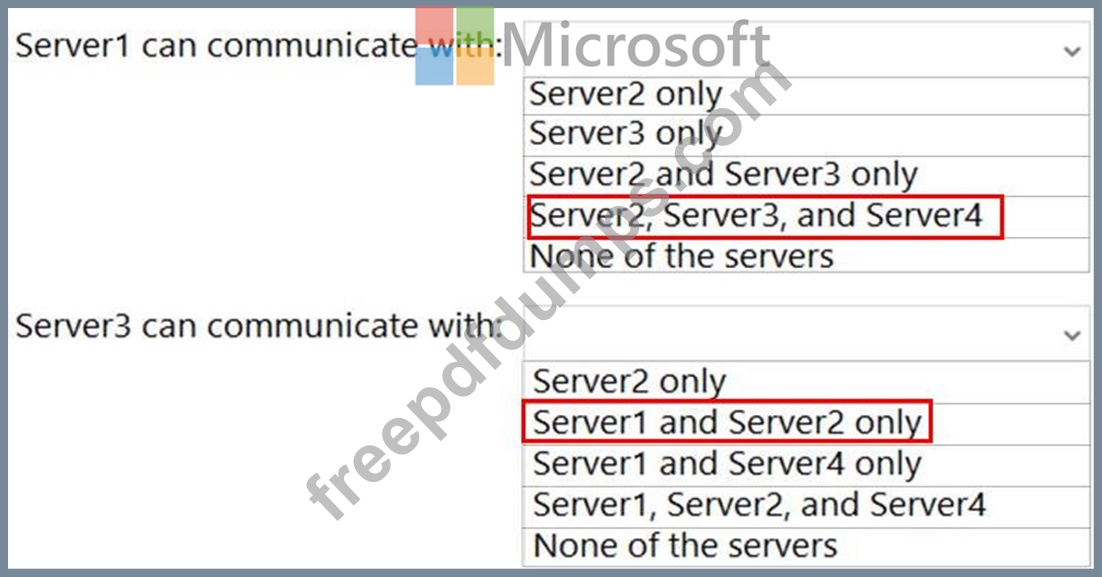
With which servers can Server1 and Server3 communicate? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
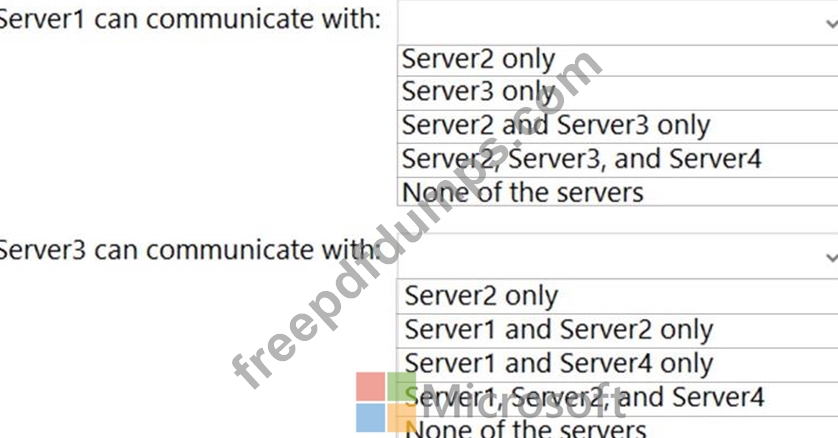
NOTE: Each correct selection is worth one point.