MS-102 Exam Question 1
You have a Microsoft 365 subscription that contains the devices shown in the following table.
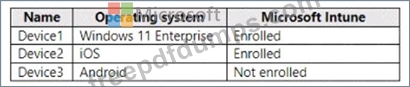
You install Microsoft Word on all the devices.
You plan to configure policies to meet the following requirements:
* Word files created by using Windows devices must be encrypted automatically.
* If an Android device becomes jailbroken, access to corporate data must be blocked from Word.
* For iOS devices, users must be prevented from using native or third-party mail clients to connect to Microsoft 365.
Which type of polio/ should you configure for each device? To answer, drag the appropriate policy types to the correct devices. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.


You install Microsoft Word on all the devices.
You plan to configure policies to meet the following requirements:
* Word files created by using Windows devices must be encrypted automatically.
* If an Android device becomes jailbroken, access to corporate data must be blocked from Word.
* For iOS devices, users must be prevented from using native or third-party mail clients to connect to Microsoft 365.
Which type of polio/ should you configure for each device? To answer, drag the appropriate policy types to the correct devices. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-102 Exam Question 2
You have a Microsoft 365 E5 tenant.
You plan to deploy a monitoring solution that meets the following requirements:
* Captures Microsoft Teams channel messages that contain threatening or violent language.
* Alerts a reviewer when a threatening or violent message is identified.
What should you include in the solution?
You plan to deploy a monitoring solution that meets the following requirements:
* Captures Microsoft Teams channel messages that contain threatening or violent language.
* Alerts a reviewer when a threatening or violent message is identified.
What should you include in the solution?
MS-102 Exam Question 3
You have a Microsoft 365 ES tenant.
You have the alerts shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
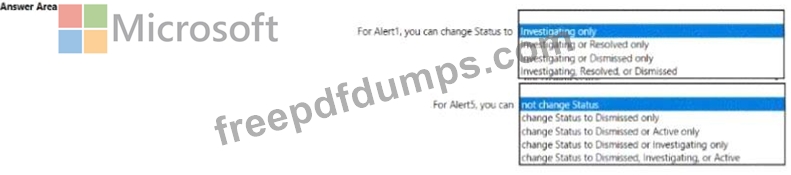
You have the alerts shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

MS-102 Exam Question 4
You have a Microsoft 365 E5 subscription.
You need to create a Conditional Access policy that will require the use of FID02 security keys only when users join their Windows devices to Microsoft Entra ID.
How should you configure the policy? To answer, select the appropriate options in the answer area.
NOTE Each correct selection is worth one point.

You need to create a Conditional Access policy that will require the use of FID02 security keys only when users join their Windows devices to Microsoft Entra ID.
How should you configure the policy? To answer, select the appropriate options in the answer area.
NOTE Each correct selection is worth one point.

MS-102 Exam Question 5
You have a Microsoft 365 E5 tenant.
You need to create a policy that will trigger an alert when unusual Microsoft Office 365 usage patterns are detected.
What should you use to create the policy?
You need to create a policy that will trigger an alert when unusual Microsoft Office 365 usage patterns are detected.
What should you use to create the policy?







