MS-500 Exam Question 1
You have a Microsoft 365 E5 subscription that has Microsoft 365 Defender enabled.
You plan to deploy a third-party app named App1 that will receive alert data from Microsoft 365 Defender.
Which format will Microsoft 365 Defender use to send the alert data to App1?
You plan to deploy a third-party app named App1 that will receive alert data from Microsoft 365 Defender.
Which format will Microsoft 365 Defender use to send the alert data to App1?
MS-500 Exam Question 2
A user stores the following files in Microsoft OneDrive:
File.docx
ImportantFile.docx
File_Important.docx
You create a Microsoft Cloud App Security file policy Policy1 that has the filter shown in the following exhibit.
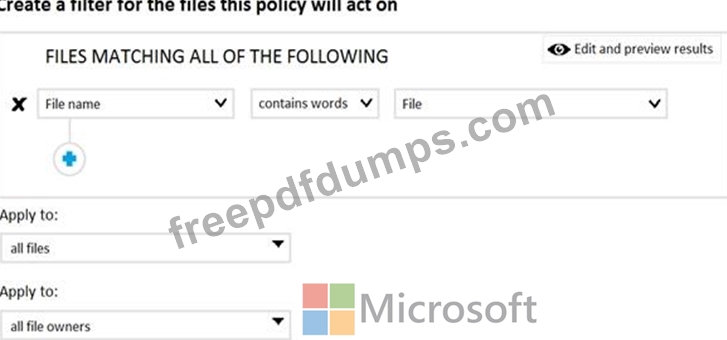
To which files does Policy1 apply?
File.docx
ImportantFile.docx
File_Important.docx
You create a Microsoft Cloud App Security file policy Policy1 that has the filter shown in the following exhibit.

To which files does Policy1 apply?
MS-500 Exam Question 3
You have a Microsoft 365 subscription. Auditing is enabled.
A user named User1 is a member of a dynamic security group named Group1.
You discover that User1 is no longer a member of Group1.
You need to search the audit log to identify why User1 was removed from Group1.
Which two actions should you use in the search? To answer, select the appropriate activities in the answer area.
NOTE: Each correct selection is worth one point.
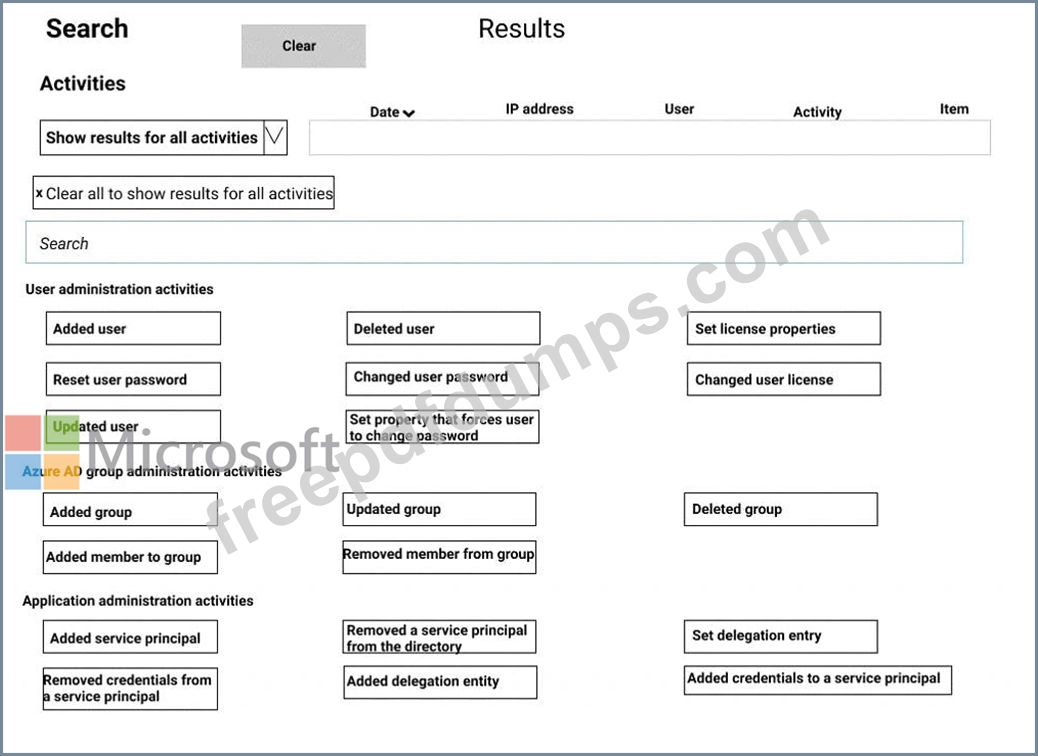
A user named User1 is a member of a dynamic security group named Group1.
You discover that User1 is no longer a member of Group1.
You need to search the audit log to identify why User1 was removed from Group1.
Which two actions should you use in the search? To answer, select the appropriate activities in the answer area.
NOTE: Each correct selection is worth one point.

MS-500 Exam Question 4
You have a Microsoft 365 subscription.
A security manager receives an email message every time a data loss prevention (DLP) policy match occurs.
You need to limit alert notifications to actionable DLP events.
What should you do?
A security manager receives an email message every time a data loss prevention (DLP) policy match occurs.
You need to limit alert notifications to actionable DLP events.
What should you do?
MS-500 Exam Question 5
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server.
You need to view Azure AD Connect events.
You use the Security event log on Server1.
Does that meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server.
You need to view Azure AD Connect events.
You use the Security event log on Server1.
Does that meet the goal?




