SC-200 Exam Question 121
You have a Microsoft Sentinel workspace that contains an Azure AD data connector.
You need to associate a bookmark with an Azure AD-related incident.
What should you do? To answer, drag the appropriate blades to the correct tasks. Each blade may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content NOTE: Each correct selection is worth one point.

You need to associate a bookmark with an Azure AD-related incident.
What should you do? To answer, drag the appropriate blades to the correct tasks. Each blade may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content NOTE: Each correct selection is worth one point.

SC-200 Exam Question 122
You have a Microsoft 365 E5 subscription that uses Microsoft 365 Defender.
You need to review new attack techniques discovered by Microsoft and identify vulnerable resources in the subscription. The solution must minimize administrative effort Which blade should you use in the Microsoft 365 Defender portal?
You need to review new attack techniques discovered by Microsoft and identify vulnerable resources in the subscription. The solution must minimize administrative effort Which blade should you use in the Microsoft 365 Defender portal?
SC-200 Exam Question 123
You have a Microsoft 365 E5 subscription that contains Windows 11 and Linux CentOS devices.
In Microsoft Defender XDR, Deception is set to On.
You plan to create a deception rule that will use a custom lure.
You need to specify the type of file, and the planting path for for the custom lure, What should you specify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
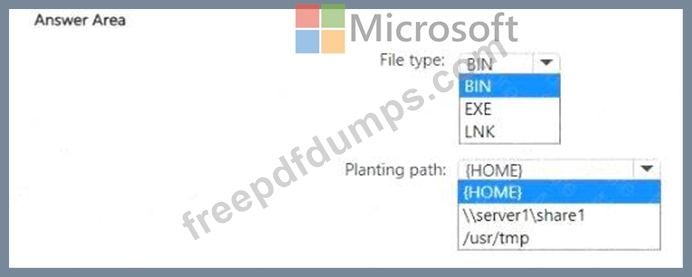
In Microsoft Defender XDR, Deception is set to On.
You plan to create a deception rule that will use a custom lure.
You need to specify the type of file, and the planting path for for the custom lure, What should you specify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-200 Exam Question 124
You have an Azure subscription named Sub1 and a Microsoft 365 subscription. Sub1 is linked to an Azure Active Directory (Azure AD) tenant named contoso.com.
You create an Azure Sentinel workspace named workspace1. In workspace1, you activate an Azure AD connector for contoso.com and an Office 365 connector for the Microsoft 365 subscription.
You need to use the Fusion rule to detect multi-staged attacks that include suspicious sign-ins to contoso.com followed by anomalous Microsoft Office 365 activity.
Which two actions should you perform? Each correct answer present part of the solution NOTE: Each correct selection is worth one point.
You create an Azure Sentinel workspace named workspace1. In workspace1, you activate an Azure AD connector for contoso.com and an Office 365 connector for the Microsoft 365 subscription.
You need to use the Fusion rule to detect multi-staged attacks that include suspicious sign-ins to contoso.com followed by anomalous Microsoft Office 365 activity.
Which two actions should you perform? Each correct answer present part of the solution NOTE: Each correct selection is worth one point.
SC-200 Exam Question 125
You have an Azure subscription that uses Microsoft Sentinel.
You need to minimize the administrative effort required to respond to the incidents and remediate the security threats detected by Microsoft Sentinel.
Which two features should you use? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to minimize the administrative effort required to respond to the incidents and remediate the security threats detected by Microsoft Sentinel.
Which two features should you use? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.