SC-300 Exam Question 191
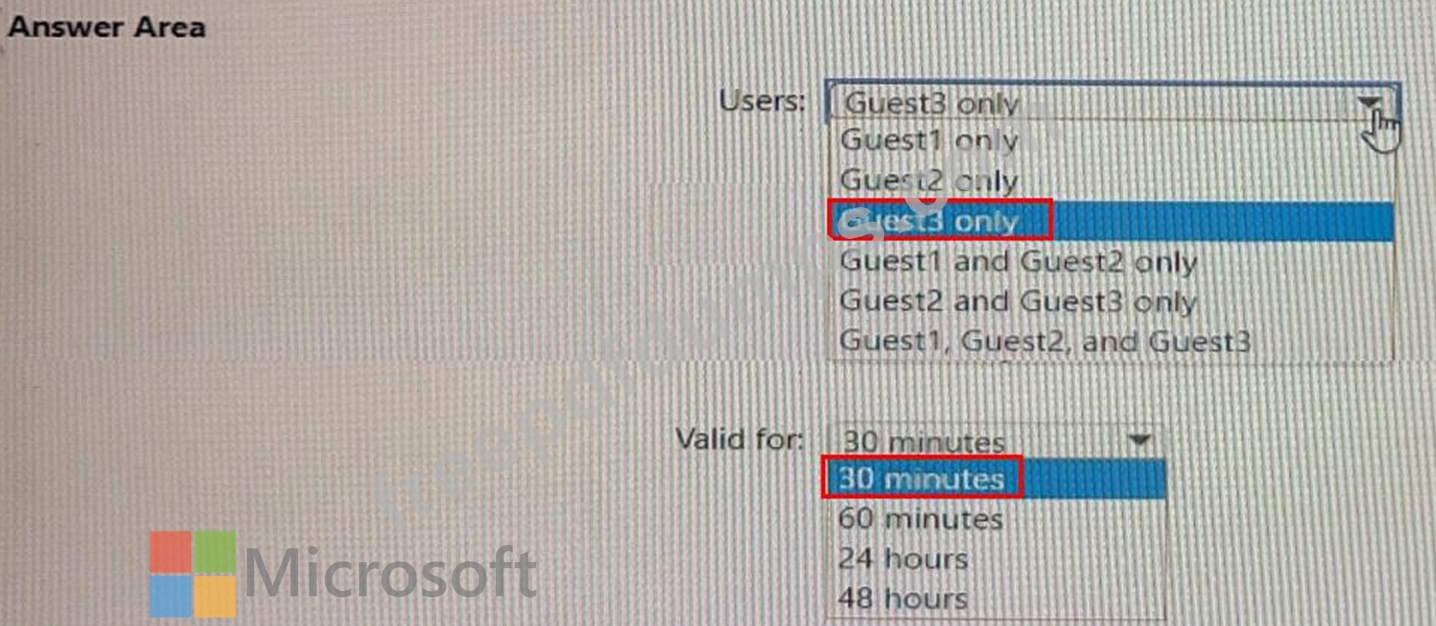
You have an Azure AD tenant named contoso.com that has Email one-time passcode for guests set to Yes.
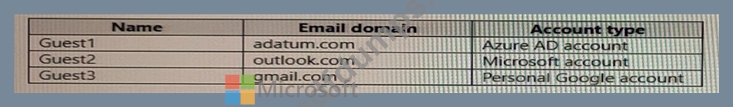
You invite the guest users shown in the following table.
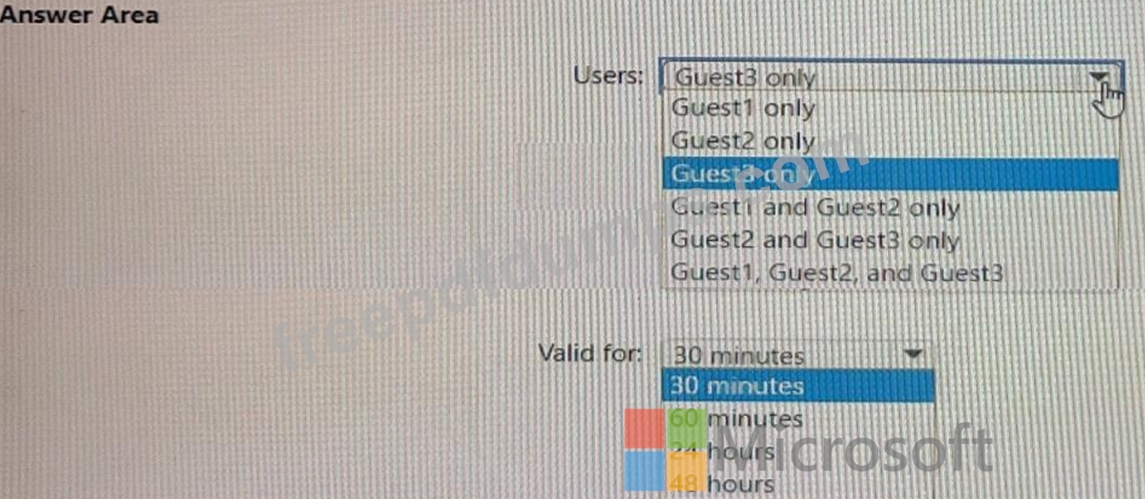
Which users will receive a one-time passcode, and how long will the passcode be valid? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You invite the guest users shown in the following table.

Which users will receive a one-time passcode, and how long will the passcode be valid? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 192
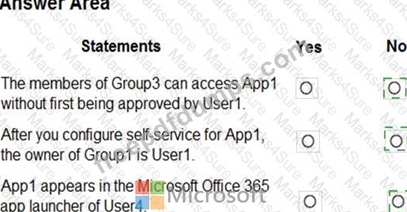
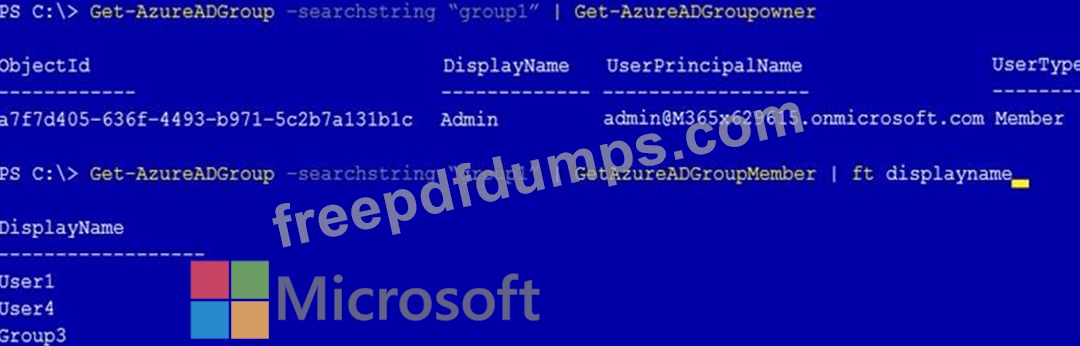
You have a Microsoft 365 tenant that contains a group named Group1 as shown in the Group1 exhibit. (Click the Group1 tab.)
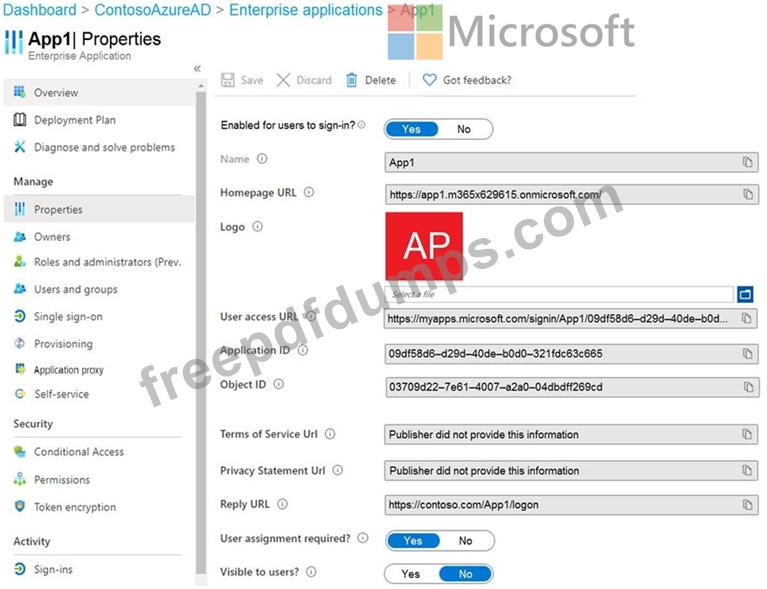
You create an enterprise application named App1 as shown in the App1 Properties exhibit. (Click the App1 Properties tab.)
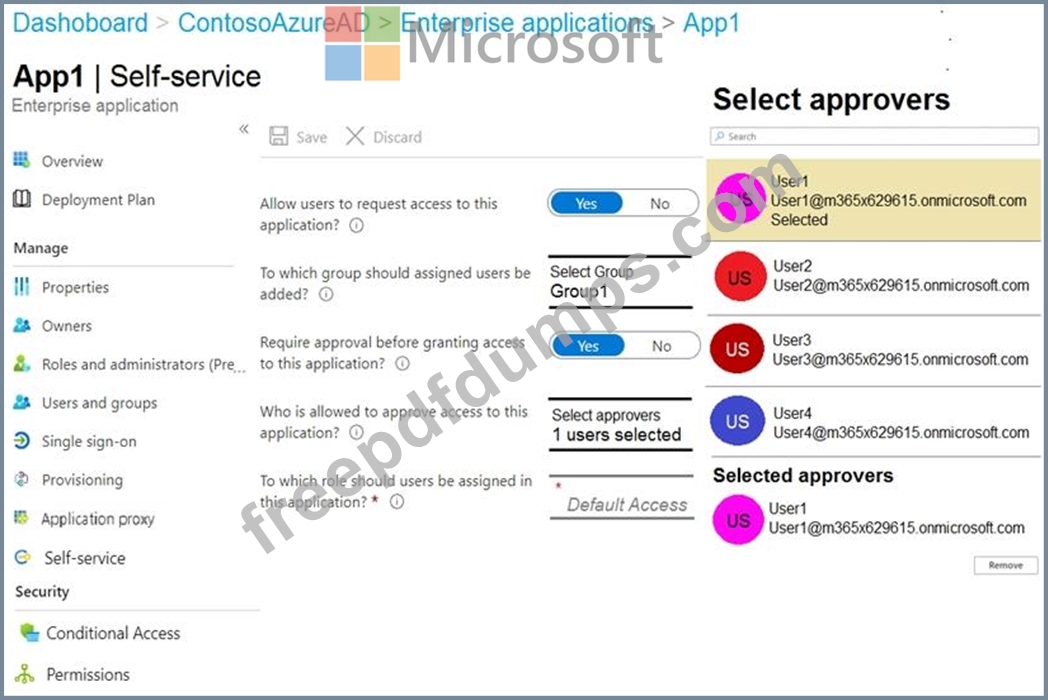
You configure self-service for App1 as shown in the App1 Self-service exhibit. (Click the App1 Self-service tab.)
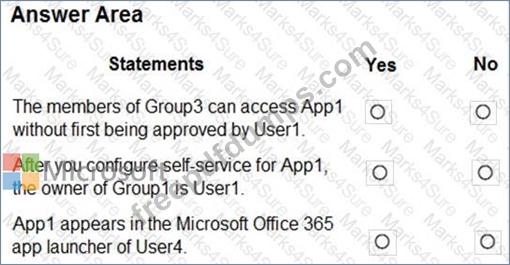
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You create an enterprise application named App1 as shown in the App1 Properties exhibit. (Click the App1 Properties tab.)

You configure self-service for App1 as shown in the App1 Self-service exhibit. (Click the App1 Self-service tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

SC-300 Exam Question 193
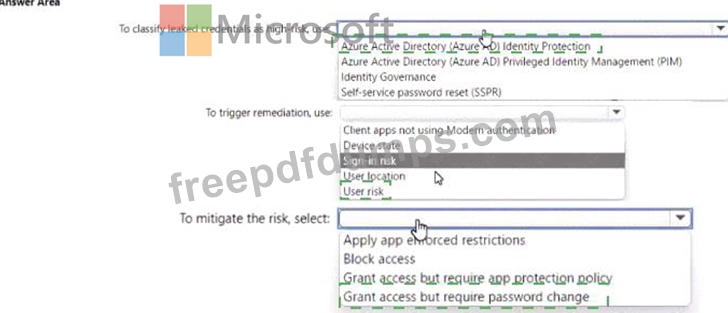
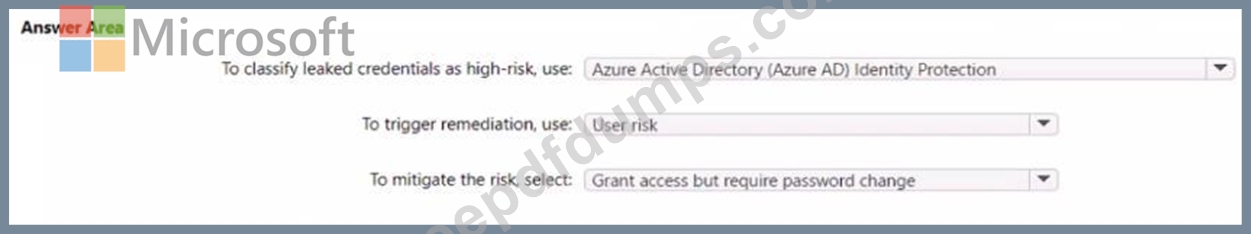
You have a Microsoft 365 tenant.
You need to Identity users who have leaked credentials. The solution must meet the following requirements:
* Identity sign-ms by users who are suspected of having leaked credentials.
* Flag the sign-ins as a high-risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options m the answer area.
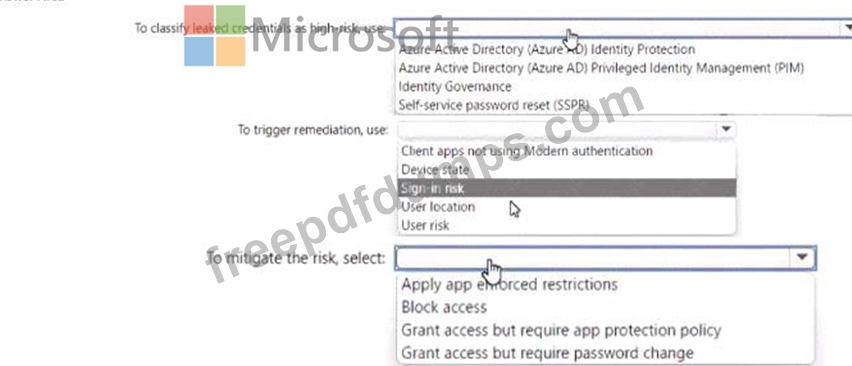
You need to Identity users who have leaked credentials. The solution must meet the following requirements:
* Identity sign-ms by users who are suspected of having leaked credentials.
* Flag the sign-ins as a high-risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options m the answer area.

SC-300 Exam Question 194
You have a Microsoft Exchange organization that uses an SMTP' address space of contoso.com.
Several users use their contoso.com email address for self-service sign up to Azure Active Directory (Azure AD).
You gain global administrator privileges to the Azure AD tenant that contains the self-signed users.
You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services.
Which PowerShell cmdlet should you run?
Several users use their contoso.com email address for self-service sign up to Azure Active Directory (Azure AD).
You gain global administrator privileges to the Azure AD tenant that contains the self-signed users.
You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services.
Which PowerShell cmdlet should you run?
SC-300 Exam Question 195
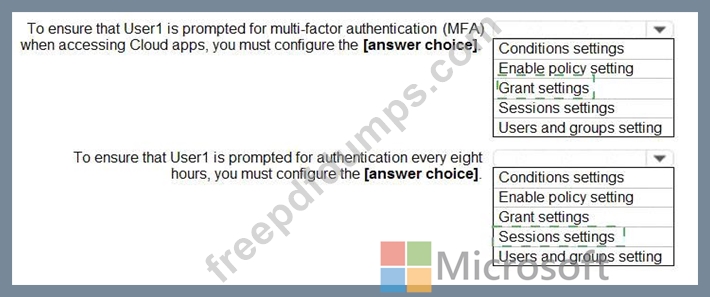
You have an Azure Active Directory (Azure AD) tenant that has Security defaults disabled.
You are creating a conditional access policy as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
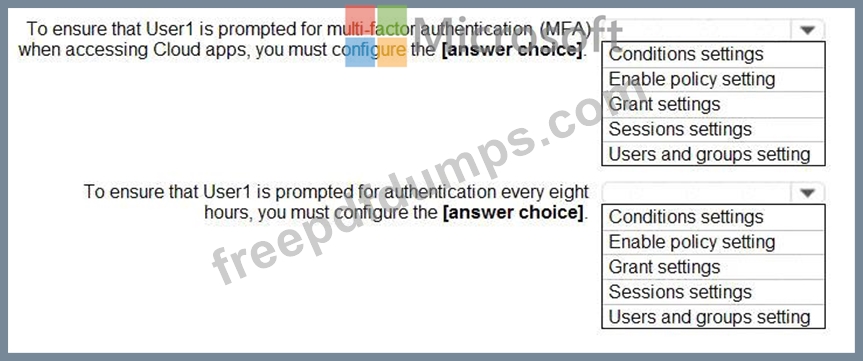
You are creating a conditional access policy as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.