SC-400 Exam Question 31
You have a new Microsoft 365 tenant.
You need to ensure that custom trainable classifiers can be created in the tenant.
To which role should you be assigned to perform the configuration?
You need to ensure that custom trainable classifiers can be created in the tenant.
To which role should you be assigned to perform the configuration?
SC-400 Exam Question 32
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You recently discovered that the developers at your company emailed Azure Storage keys in plain text to third parties.
You need to ensure that when Azure Storage keys are emailed, the emails are encrypted.
Solution: You create a data loss prevention (DLP) policy that has only the Exchange email location selected.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You recently discovered that the developers at your company emailed Azure Storage keys in plain text to third parties.
You need to ensure that when Azure Storage keys are emailed, the emails are encrypted.
Solution: You create a data loss prevention (DLP) policy that has only the Exchange email location selected.
Does this meet the goal?
SC-400 Exam Question 33
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add the application to the unallowed apps list.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add the application to the unallowed apps list.
Does this meet the goal?
SC-400 Exam Question 34
You are configuring a retention label named Label1 as shown in the following exhibit.
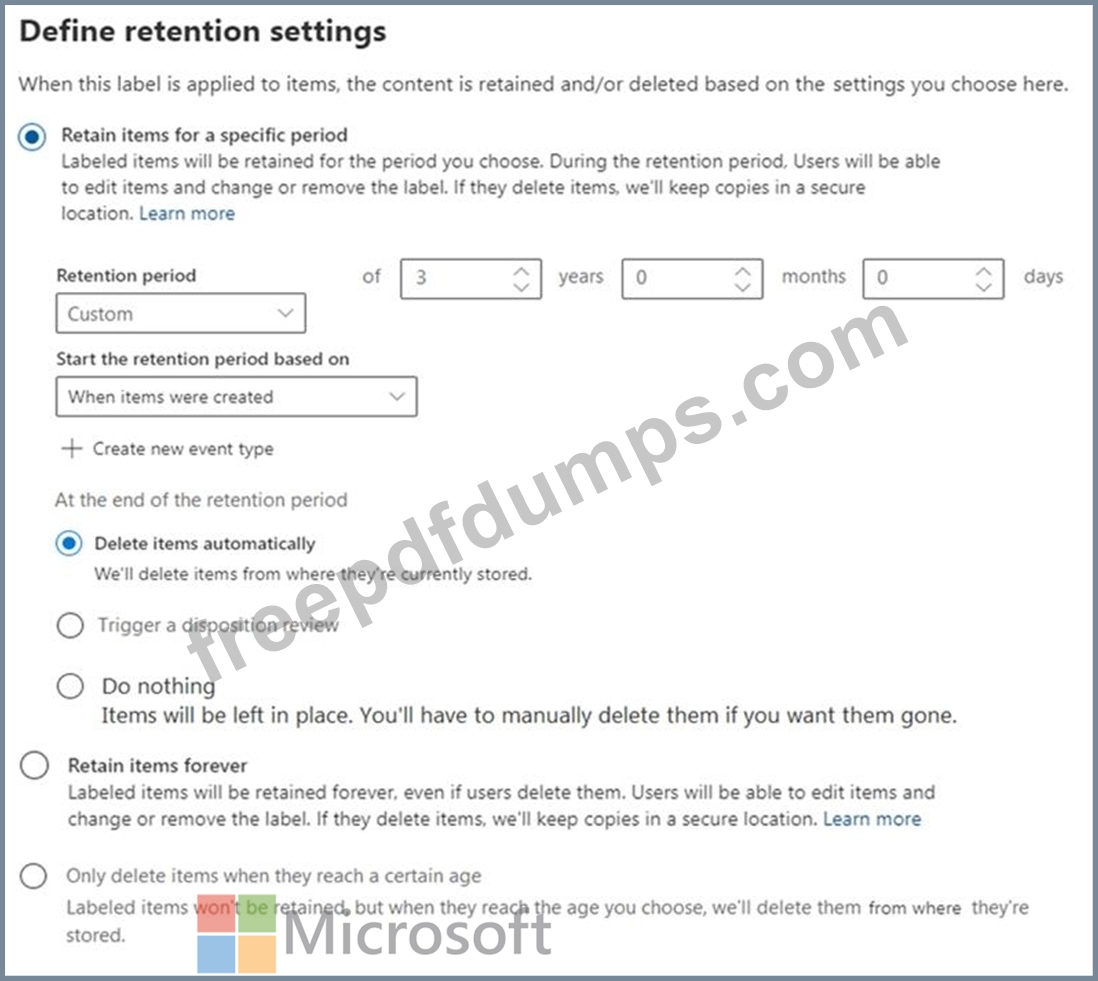
You need to ensure that documents that have Label1 applied are deleted three years after the end of your company's fiscal year.
What should you do?

You need to ensure that documents that have Label1 applied are deleted three years after the end of your company's fiscal year.
What should you do?
SC-400 Exam Question 35
You have the files shown in the following table.

You configure a retention policy as shown in the following exhibit.

The current date is January 1, 2021.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.


You configure a retention policy as shown in the following exhibit.

The current date is January 1, 2021.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.



