SC-400 Exam Question 36
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add a folderpath to the file path exclusions.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add a folderpath to the file path exclusions.
Does this meet the goal?
SC-400 Exam Question 37
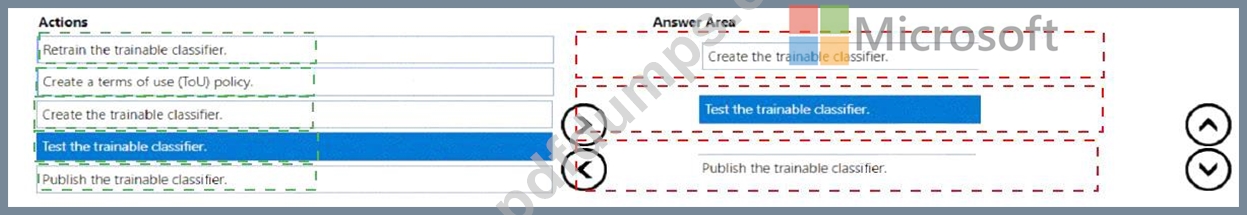
You need to create a trainable classifier that can be used as a condition in an auto-apply retention label policy.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
SC-400 Exam Question 38
In Microsoft Exchange Online, you have a retention policy named Policy1 that applies a retention tag named Tag1.
You plan to remove Tag1 from Policy1.
What will occur when you remove the tag from Policy1?
You plan to remove Tag1 from Policy1.
What will occur when you remove the tag from Policy1?
SC-400 Exam Question 39
You have a Microsoft 365 tenant that uses trainable classifiers.
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.
Which file categories can be used as seed content?
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.
Which file categories can be used as seed content?
SC-400 Exam Question 40
You need to recommend a solution that meets the compliance requirements for viewing DLP tooltip justifications.
What should you recommend?
What should you recommend?