PCNSE Exam Question 151
Refer to the exhibit.
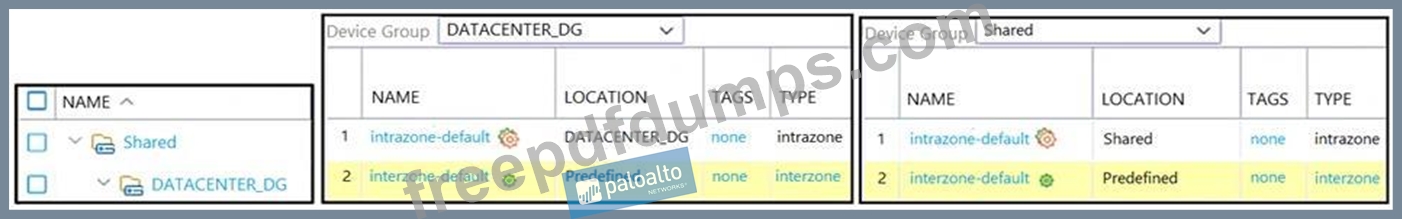
Based on the screenshots above, what is the correct order in which the various rules are deployed to firewalls inside the DATACENTER_DG device group?

Based on the screenshots above, what is the correct order in which the various rules are deployed to firewalls inside the DATACENTER_DG device group?
PCNSE Exam Question 152
An administrator is attempting to create policies tor deployment of a device group and template stack.
When creating the policies, the zone drop down list does not include the required zone.
What must the administrator do to correct this issue?
When creating the policies, the zone drop down list does not include the required zone.
What must the administrator do to correct this issue?
PCNSE Exam Question 153
An engineer configures a destination NAT policy to allow inbound access to an internal server in the DMZ. The NAT policy is configured with the following values:
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
PCNSE Exam Question 154
A client has a sensitive application server in their data center and is particularly concerned about resource exhaustion because of distributed denial-of-service attacks.
How can the Palo Alto Networks NGFW be configured to specifically protect this server against resource exhaustion originating from multiple IP addresses (DDoS attack)?
How can the Palo Alto Networks NGFW be configured to specifically protect this server against resource exhaustion originating from multiple IP addresses (DDoS attack)?
PCNSE Exam Question 155
An administrator has been tasked with deploying SSL Forward Proxy.
Which two types of certificates are used to decrypt the traffic? (Choose two.)
Which two types of certificates are used to decrypt the traffic? (Choose two.)

