PCNSE Exam Question 326
An administrator wants multiple web servers in the DMZ to receive connections initiated from the internet. Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at
10.1.1.22.
Based on the information shown in the image, which NAT rule will forward web-browsing traffic correctly?
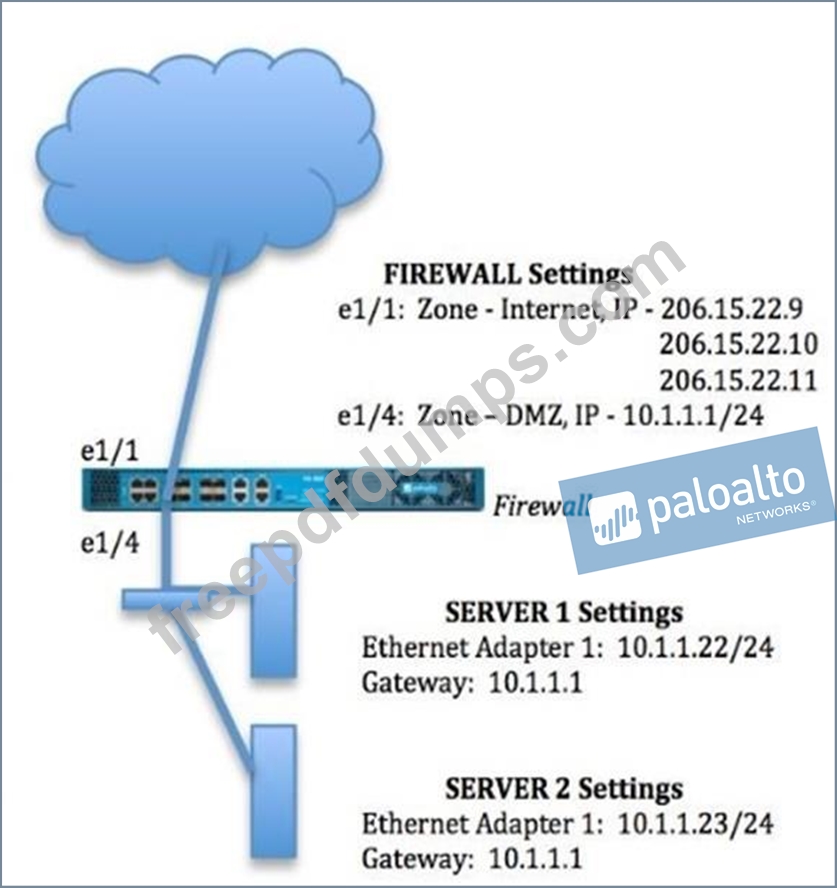
10.1.1.22.
Based on the information shown in the image, which NAT rule will forward web-browsing traffic correctly?

PCNSE Exam Question 327
An engineer notices that the tunnel monitoring has been failing for a day and the VPN should have failed over to a backup path.
What part of the network profile configuration should the engineer verify?
What part of the network profile configuration should the engineer verify?
PCNSE Exam Question 328
What file type upload is supported as part of the basic WildFire service?
PCNSE Exam Question 329
SSL Forward Proxy decryption is configured but the firewall uses Untrusted-CA to sign the website https //www important-website com certificate End-users are receiving me "security certificate is not trusted is warning Without SSL decryption the web browser shows that the website certificate is trusted and signed by a well-known certificate chain Well-Known- lntermediate and Well-Known-Root-CA.
The network security administrator who represents the customer requires the following two behaviors when SSL Forward Proxy is enabled:
1. End-users must not get the warning for the https://www.very-important-website.com website.
2. End-users should get the warning for any other untrusted website
Which approach meets the two customer requirements?
The network security administrator who represents the customer requires the following two behaviors when SSL Forward Proxy is enabled:
1. End-users must not get the warning for the https://www.very-important-website.com website.
2. End-users should get the warning for any other untrusted website
Which approach meets the two customer requirements?
PCNSE Exam Question 330
Which two actions are required to make Microsoft Active Directory users appear in a firewall traffic log? (Choose two.)

