200-201 Exam Question 96
Refer to the exhibit.
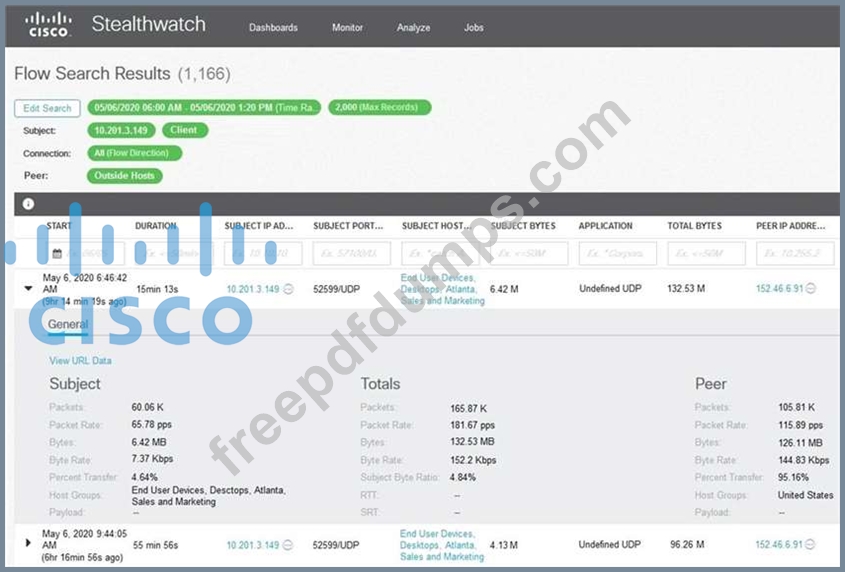
What is the potential threat identified in this Stealthwatch dashboard?

What is the potential threat identified in this Stealthwatch dashboard?
200-201 Exam Question 97
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
200-201 Exam Question 98
Which two elements are used for profiling a network? (Choose two.)
200-201 Exam Question 99
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
200-201 Exam Question 100
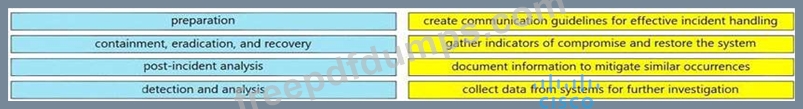
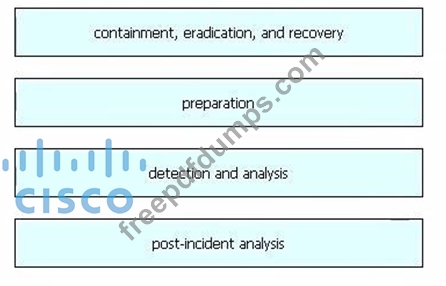
Drag and drop the elements from the left into the correct order for incident handling on the right.