200-201 Exam Question 116
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
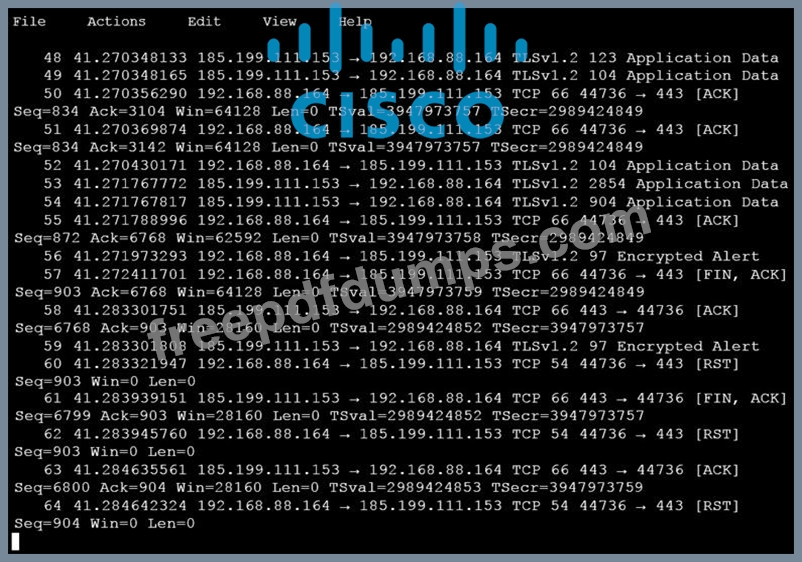
Which obfuscation technique is the attacker using?

Which obfuscation technique is the attacker using?
200-201 Exam Question 117
Refer to the exhibit.
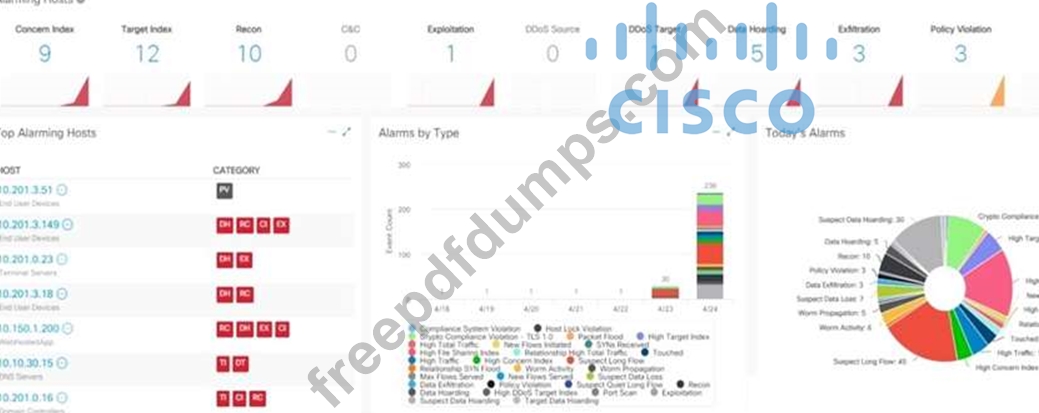
What is the potential threat identified in this Stealthwatch dashboard?

What is the potential threat identified in this Stealthwatch dashboard?
200-201 Exam Question 118
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
200-201 Exam Question 119
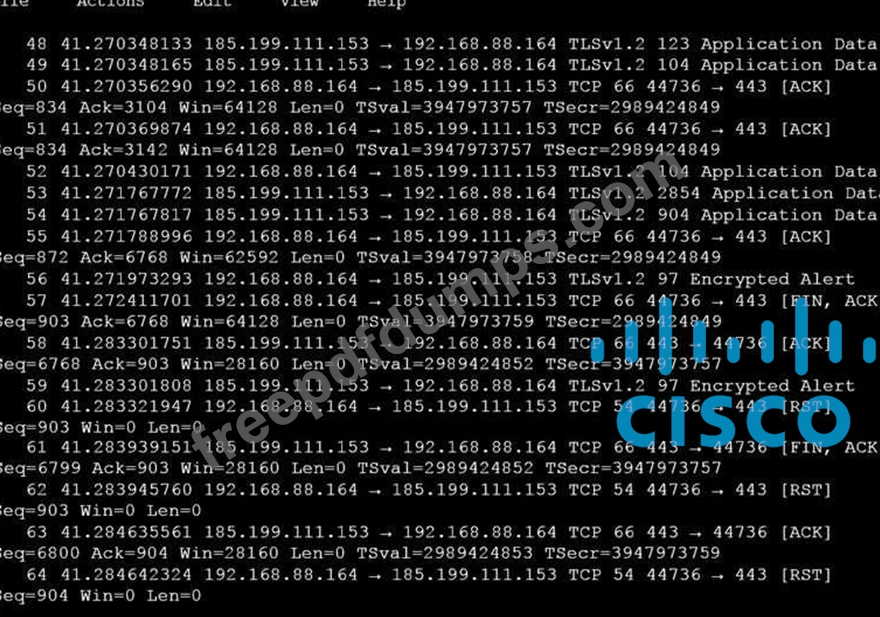
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.
Which obfuscation technique is the attacker using?
200-201 Exam Question 120
What is a difference between data obtained from Tap and SPAN ports?

