200-201 Exam Question 6
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.
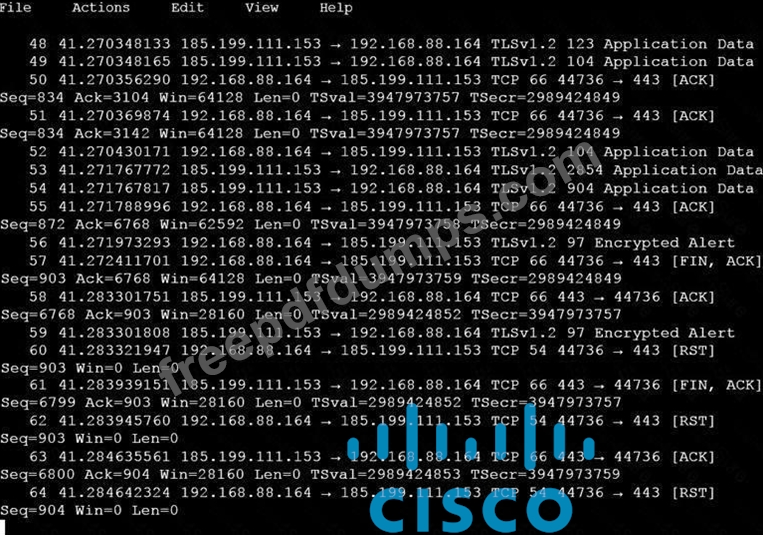
Which obfuscation technique is the attacker using?

Which obfuscation technique is the attacker using?
200-201 Exam Question 7
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
200-201 Exam Question 8

Refer to the exhibit. Which event is occurring?
200-201 Exam Question 9
An analyst discovers that a legitimate security alert has been dismissed.
Which signature caused this impact on network traffic?
Which signature caused this impact on network traffic?
200-201 Exam Question 10
Refer to the exhibit.

Which event is occurring?

Which event is occurring?

