200-901 Exam Question 136
What is a difference between a synchronous API and an asynchronous API?
200-901 Exam Question 137
Refer to the exhibit.
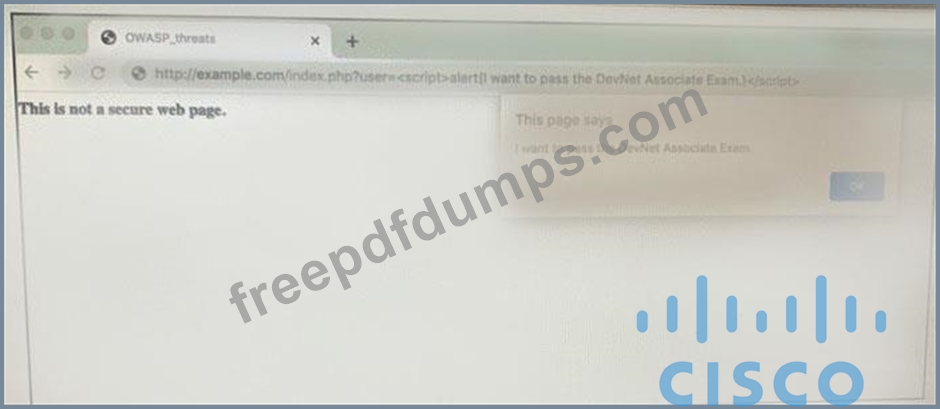
Which OWASP threat does this example demonstrate?

Which OWASP threat does this example demonstrate?
200-901 Exam Question 138
What operation is performed with YANG model-driven programmability in NX-OS?
200-901 Exam Question 139

Refer to the exhibit. A developer is part of a team that is working on an open-source project in which source code is hosted in a public GitHub repository. While the application was built, security concerns were addressed by encrypting the credentials on the server. After a few months, the developer realized that a hacker managed to gain access to the account. The exhibit contains part of the source code for the login process. Why was the attacker able to access the developer's account?
200-901 Exam Question 140
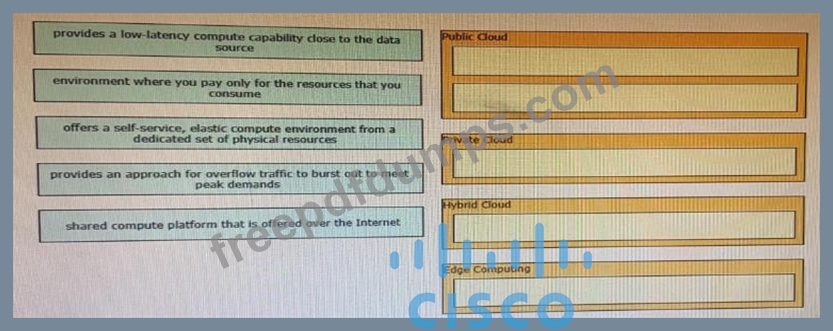
Drag and drop the descriptions from the left onto correct application deployment models on the right.