200-901 Exam Question 141
Drag and Drop Question
Drag and drop the characteristics from the left onto the software development methodologies on the right.
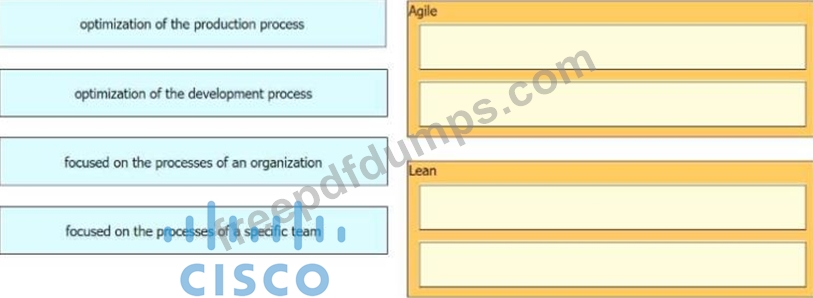
Drag and drop the characteristics from the left onto the software development methodologies on the right.

200-901 Exam Question 142
Refer to the exhibit.
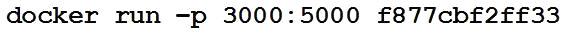
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
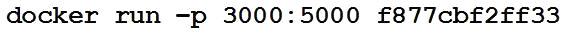
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
200-901 Exam Question 143
Refer to the exhibit. What does the load balancer enable in the network topology?
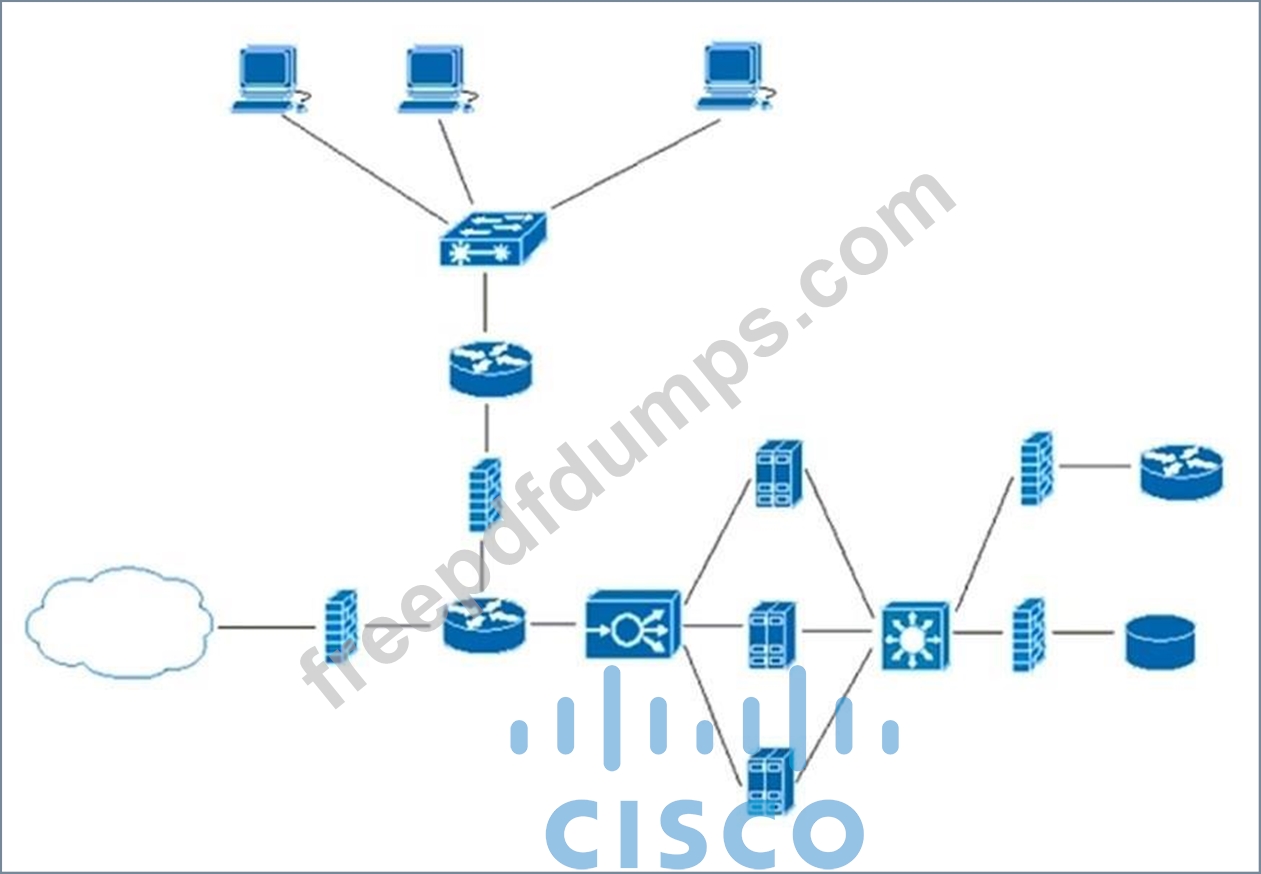

200-901 Exam Question 144
Refer to the exhibit.
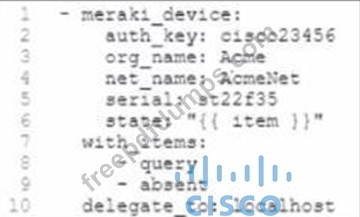
A security team observes an attack that originates from a Cisco Meraki device. To mitigate the attack, the team requests that the engineering team remove the /ice from the network. The security team also requests information about the device, such as Its name and location. Which tool must the engineering team use to meet the luirements by using tasks?

A security team observes an attack that originates from a Cisco Meraki device. To mitigate the attack, the team requests that the engineering team remove the /ice from the network. The security team also requests information about the device, such as Its name and location. Which tool must the engineering team use to meet the luirements by using tasks?
200-901 Exam Question 145
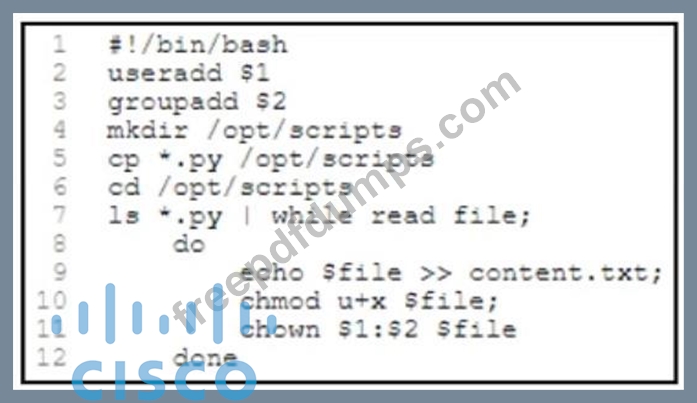
Refer to the exhibit. An engineer must add new users and set privileges for executing a few Python scripts. The engineer prepares a Bash script to automate this task. The script adds a user and a group from the command-line arguments, creates a directory, and copies the Python scripts to it. The script then changes to the directory and lists the scripts. Based on the script workflow, which process is being automated within the loop by using the list of Python scripts?