300-740 Exam Question 6
Security audit reports are crucial for:
300-740 Exam Question 7
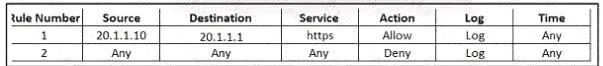
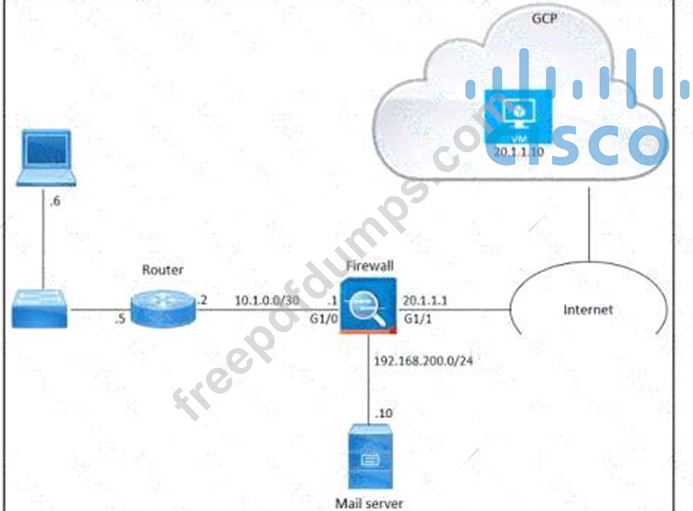
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
300-740 Exam Question 8
For enforcing application policy at the network security edge, which of the following are critical?
300-740 Exam Question 9
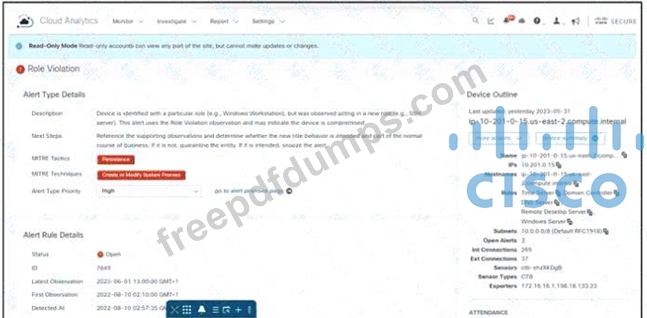
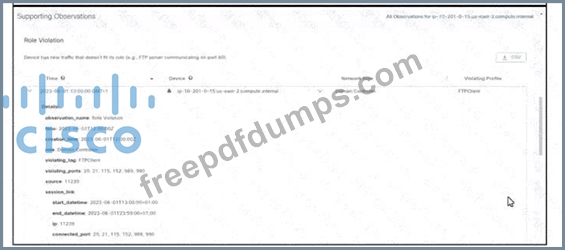
Refer to the exhibit. An engineer is troubleshooting an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?
300-740 Exam Question 10
Upon detecting a user or application compromise, the first action should be to:

