300-740 Exam Question 31
To effectively manage a compromised system, it's important to first _________ the threat to stop its spread.
300-740 Exam Question 32
The primary goal of direct-internet-access policies for trusted business applications is to:
300-740 Exam Question 33
What are key considerations when implementing an integrated cloud security architecture?
300-740 Exam Question 34
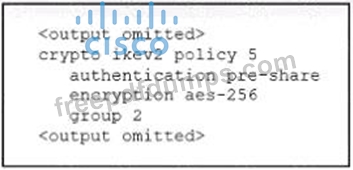
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv2 VPN that will use SHA-512 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which command must be run to meet the requirement?
300-740 Exam Question 35

Refer to the exhibit. A security engineer deployed Cisco Secure XDR, and during testing, the log entry shows a security incident. Which action must the engineer take first?

