350-201 Exam Question 56
Refer to the exhibit. Which indicator of compromise is represented by this STIX?
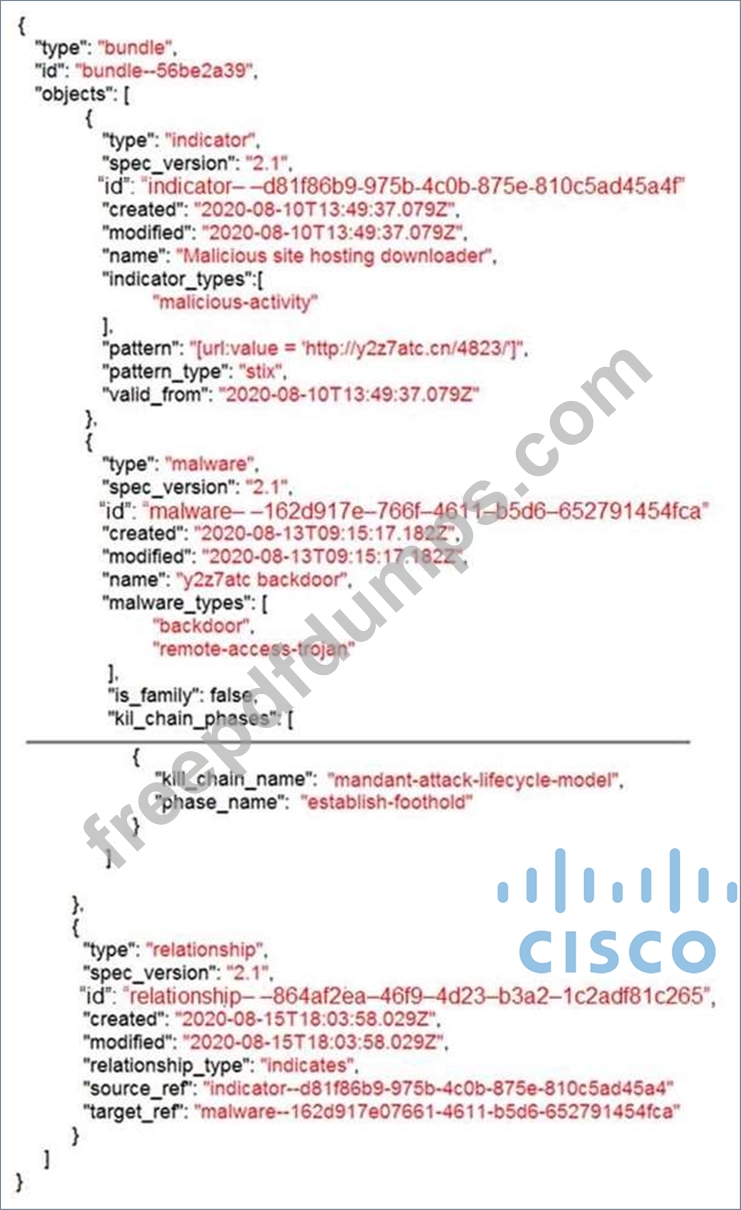

350-201 Exam Question 57
An engineer implemented a SOAR workflow to detect and respond to incorrect login attempts and anomalous user behavior. Since the implementation, the security team has received dozens of false positive alerts and negative feedback from system administrators and privileged users. Several legitimate users were tagged as a threat and their accounts blocked, or credentials reset because of unexpected login times and incorrectly typed credentials. How should the workflow be improved to resolve these issues?
350-201 Exam Question 58
Which action should be taken when the HTTP response code 301 is received from a web application?
350-201 Exam Question 59
How does Wireshark decrypt TLS network traffic?
350-201 Exam Question 60
An engineer receives an incident ticket with hundreds of intrusion alerts that require investigation. An analysis of the incident log shows that the alerts are from trusted IP addresses and internal devices. The final incident report stated that these alerts were false positives and that no intrusions were detected. What action should be taken to harden the network?

