350-201 Exam Question 26
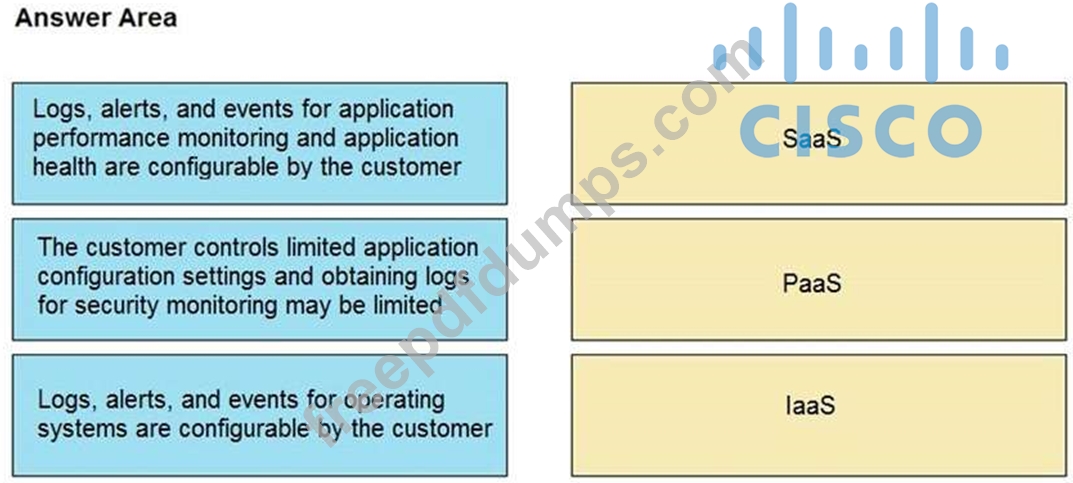
Drag and drop the telemetry-related considerations from the left onto their cloud service models on the right.

350-201 Exam Question 27
What is a limitation of cyber security risk insurance?
350-201 Exam Question 28
Refer to the exhibit.
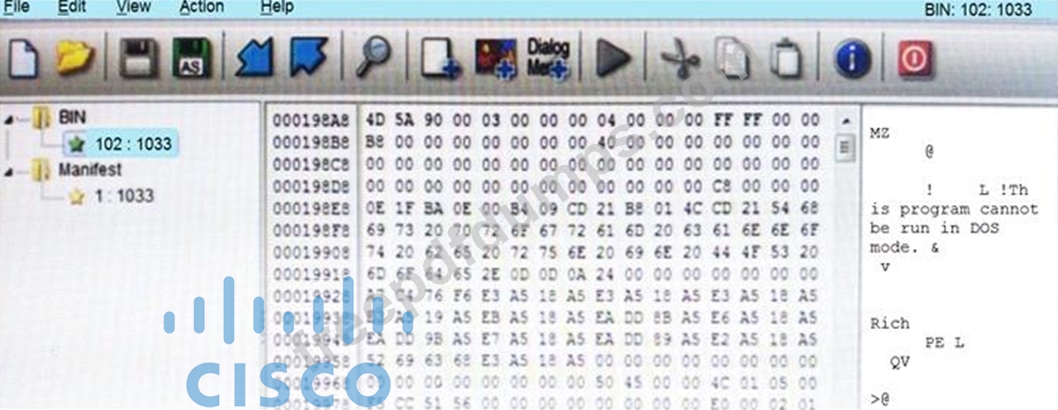
An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?

An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
350-201 Exam Question 29
An analyst is alerted for a malicious file hash. After analysis, the analyst determined that an internal workstation is communicating over port 80 with an external server and that the file hash is associated with Duqu malware. Which tactics, techniques, and procedures align with this analysis?
350-201 Exam Question 30
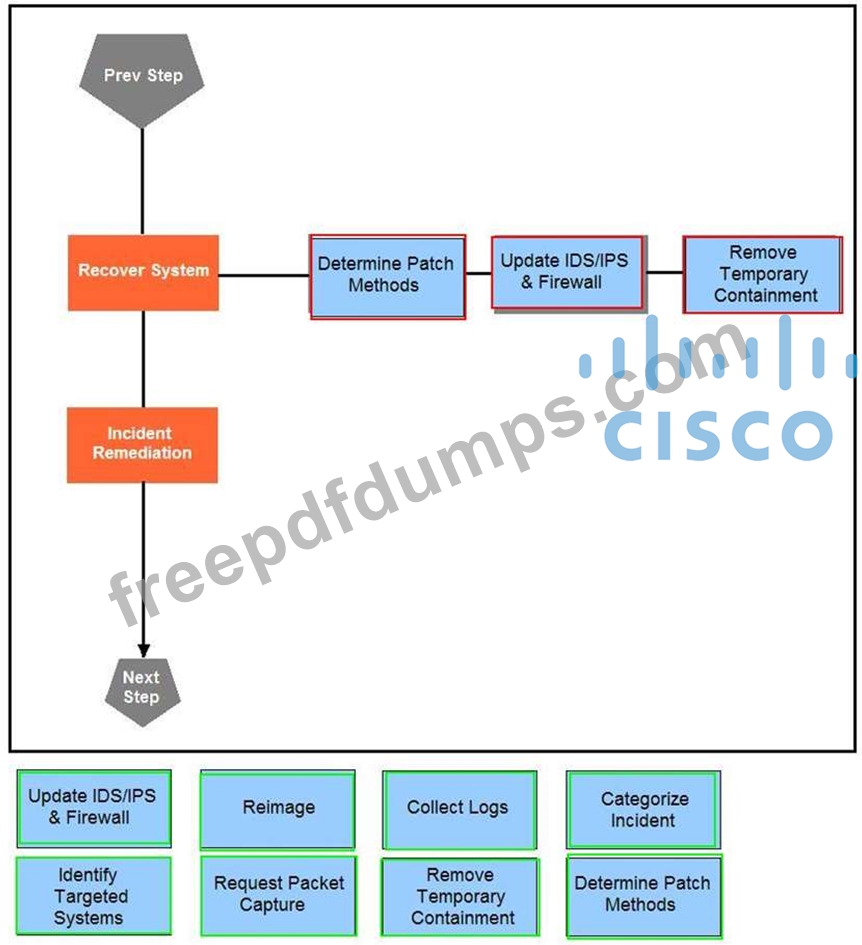
Drag and drop the actions below the image onto the boxes in the image for the actions that should be taken during this playbook step. Not all options are used.