350-901 Exam Question 41
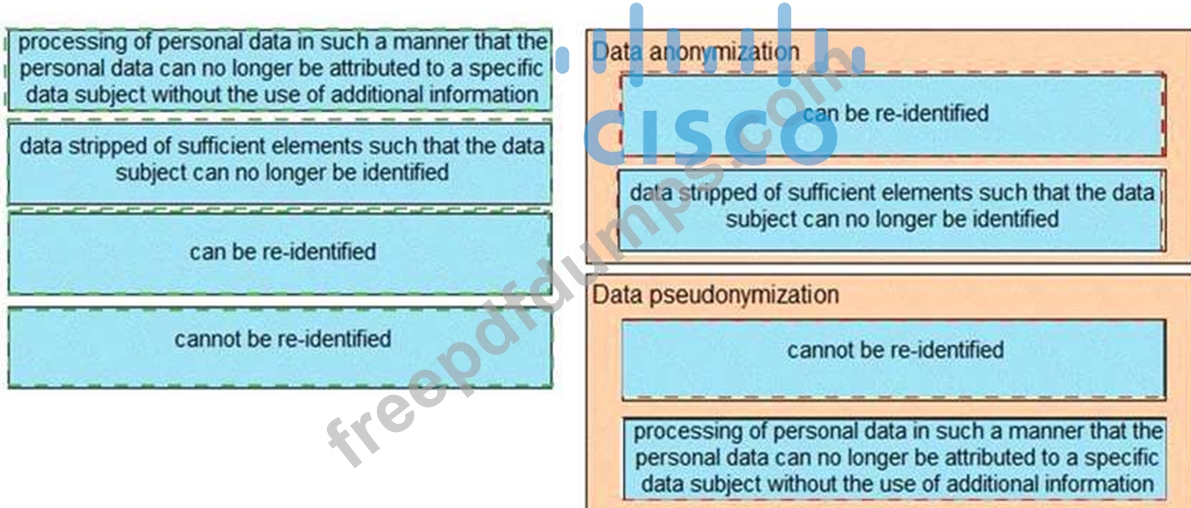
Which two strategies are used to protect personally identifiable information? (Choose two.)
350-901 Exam Question 42
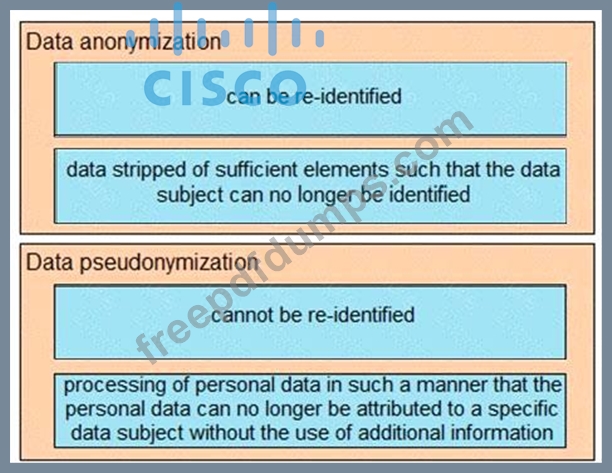
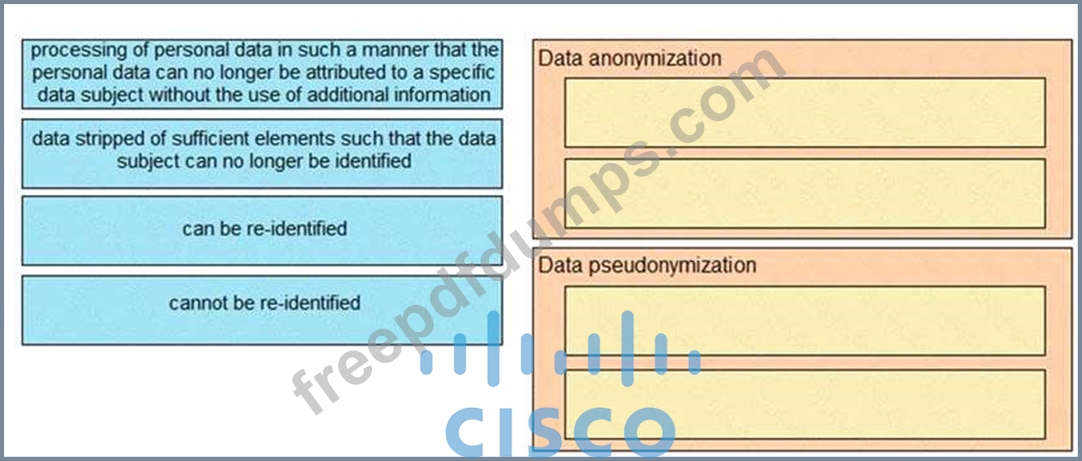
Drag and drop the characteristics from the left onto the correct data processing techniques on the right, in the context of GDPR.

350-901 Exam Question 43
Which two techniques protect against injection attacks? (Choose two.)
350-901 Exam Question 44
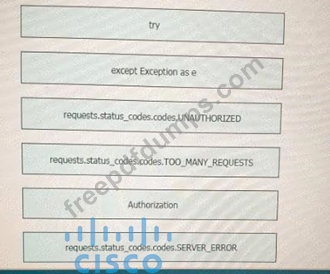
Refer to theexhibit.
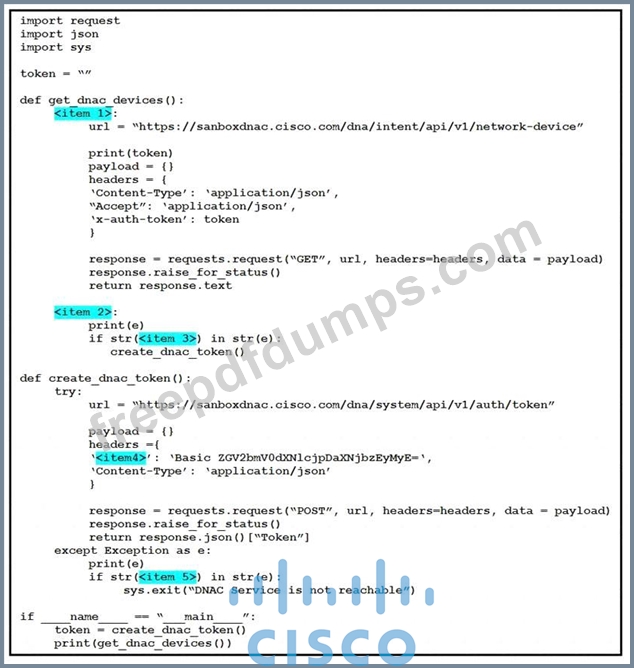
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.


Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.

350-901 Exam Question 45
Refer to the exhibit.
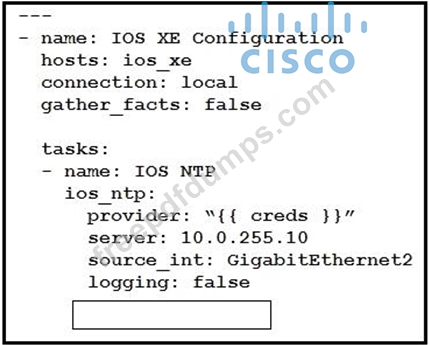
Which key value pair from the ios_ntp Ansible module creates an NTP server peer?

Which key value pair from the ios_ntp Ansible module creates an NTP server peer?