350-901 Exam Question 21
Which two techniques protect against injection attacks? (Choose two.)
350-901 Exam Question 22
Refer to the exhibit.
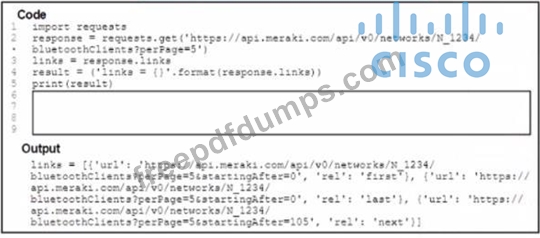
A Python script has these requirements
* Retrieve a list of Bluetooth clients seen by the access pants on a network.
* Print the content of the response
* Retrieve the next page only if it is available in the response headers What must be added where the code is missing to get the remaining pages by using the next link from the link response header of the last request?
A)
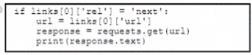
B)

C)

D)
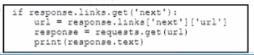

A Python script has these requirements
* Retrieve a list of Bluetooth clients seen by the access pants on a network.
* Print the content of the response
* Retrieve the next page only if it is available in the response headers What must be added where the code is missing to get the remaining pages by using the next link from the link response header of the last request?
A)

B)

C)

D)

350-901 Exam Question 23
FILL BLANK
A local Docker image has an image ID of 386231131. Fill in the blanks to complete the command in order to tag the image into the "cisco" repository with "version1 0'".

A local Docker image has an image ID of 386231131. Fill in the blanks to complete the command in order to tag the image into the "cisco" repository with "version1 0'".

350-901 Exam Question 24
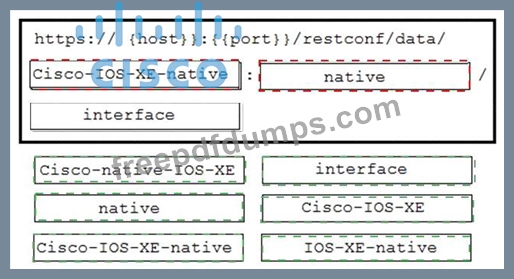
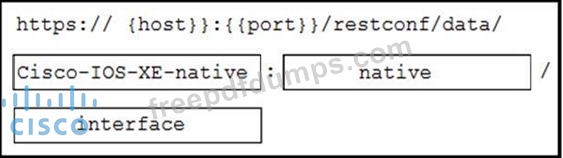
A network engineer needs to retrieve interface data using the Cisco IOS XE YANG Model. Drag and drop the components from the bottom onto the box where the code is missing to complete the RESTCONF URI. Not all options are used.
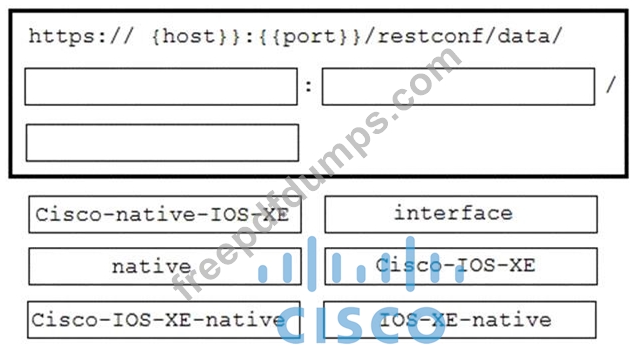

350-901 Exam Question 25
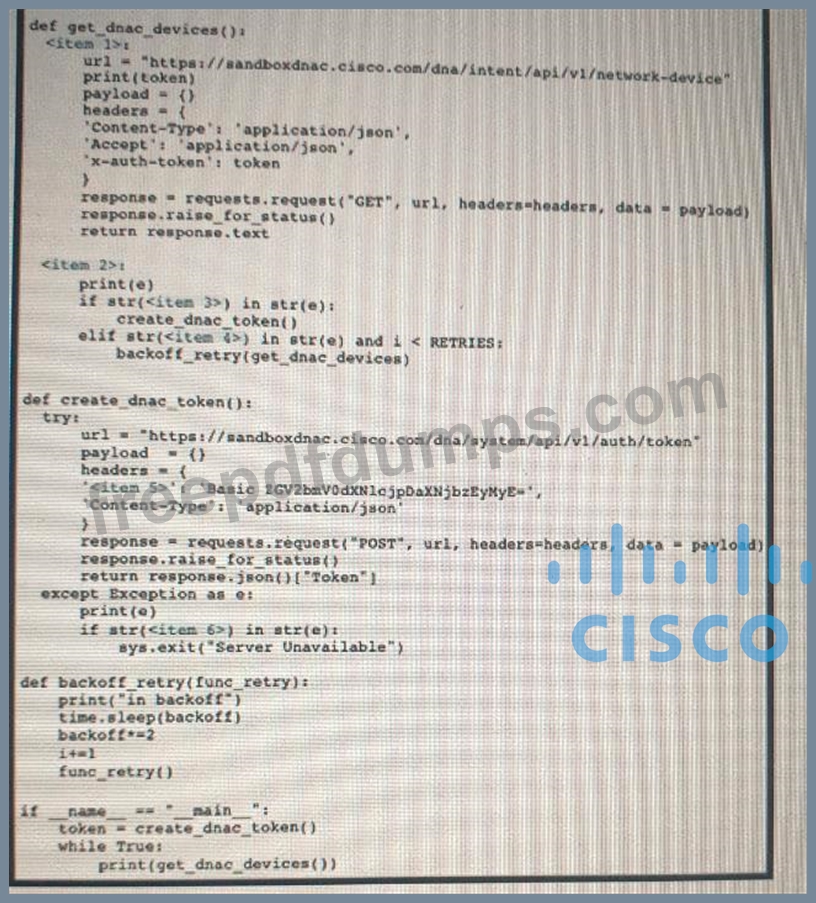
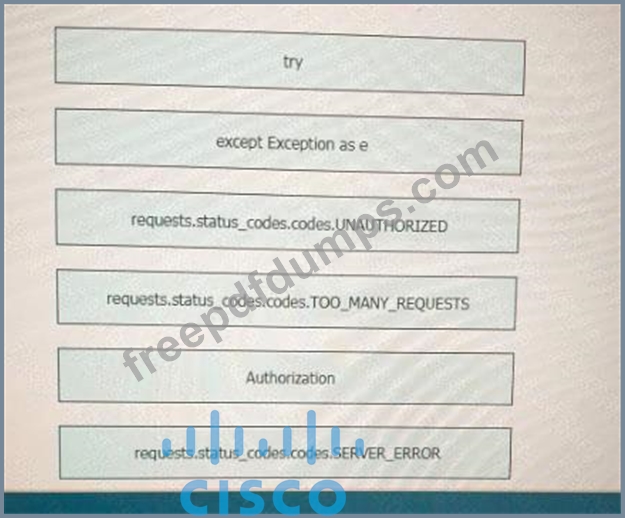
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.