350-901 Exam Question 181
Refer to the exhibit.
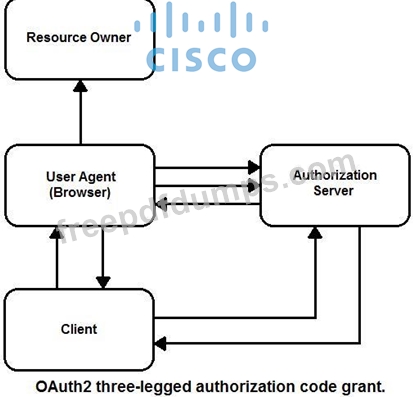
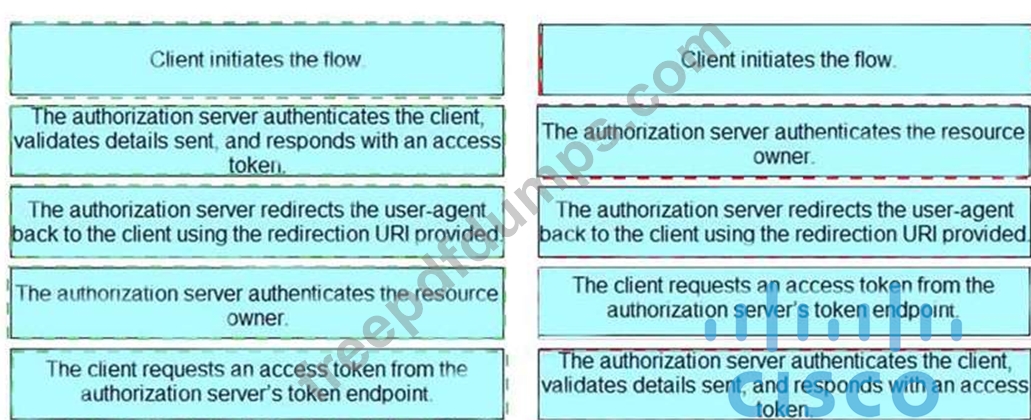
Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
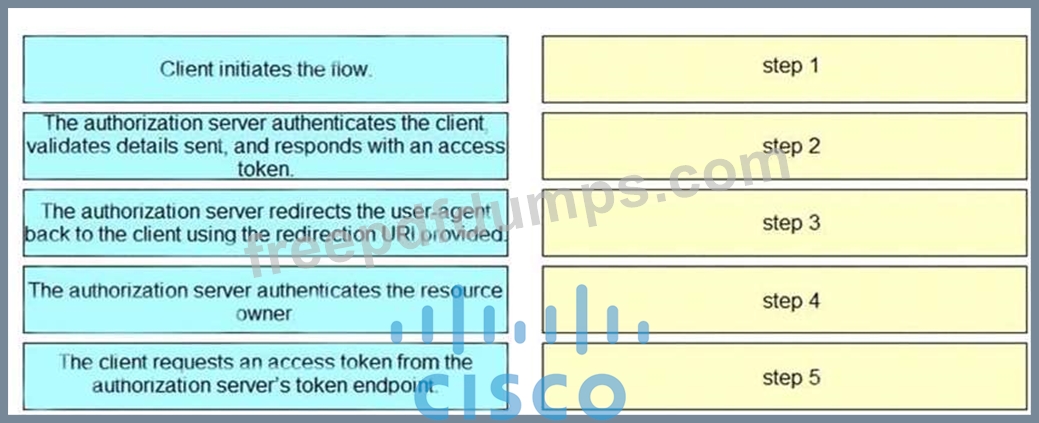

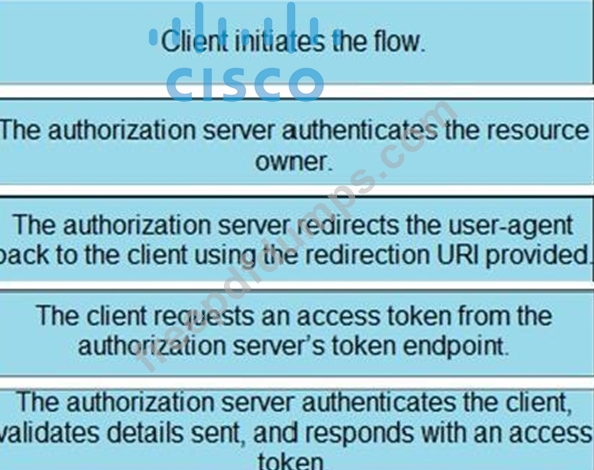
Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.

350-901 Exam Question 182
Refer to the exhibit.
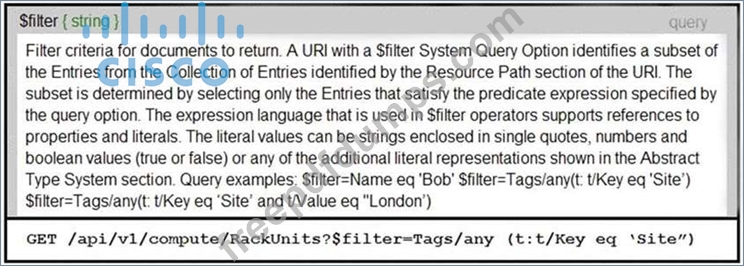
An Intersight API is being used to query RackUnit resources that have a tag keyword set to "Site". What is the expected output of this command?

An Intersight API is being used to query RackUnit resources that have a tag keyword set to "Site". What is the expected output of this command?
350-901 Exam Question 183
Which two strategies are used to protect personally identifiable information? (Choose two.)
350-901 Exam Question 184
To complete the Python script to enable the SSID with a name of "376699609" in the network resource "11111111" using the Meraki Dashboard API.


350-901 Exam Question 185
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct. Which action accomplishes this task?