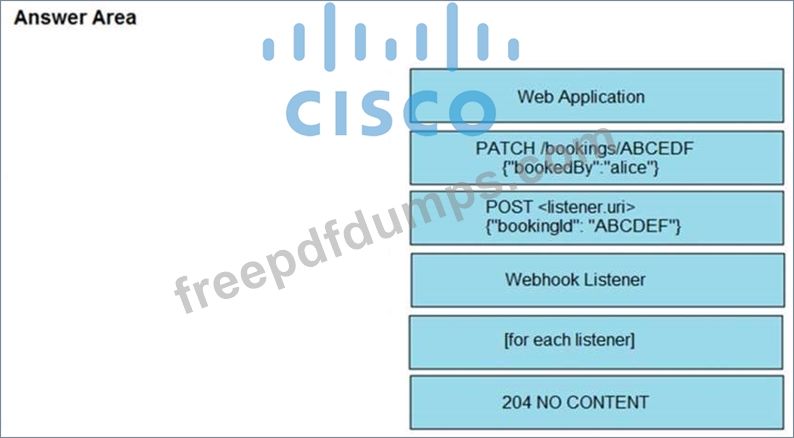
350-901 Exam Question 186
Drag and Drop Question
Refer to the exhibit above and click on the tab in the top left corner to view a diagram that describes the typical flow of requests involved when a webhook is created for a booking service.
Drag and drop the requests from the left onto the item numbers on the right that match the missing sections in the sequence diagram to design the complete flow of requests involved as a booking is updated from a web application.
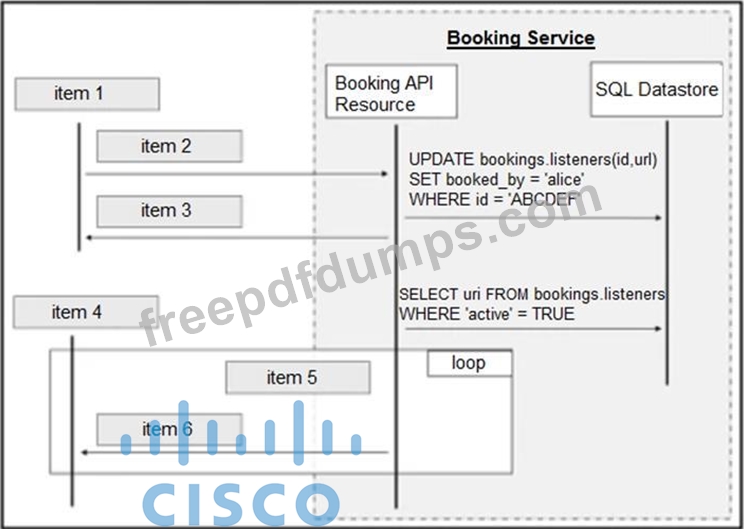
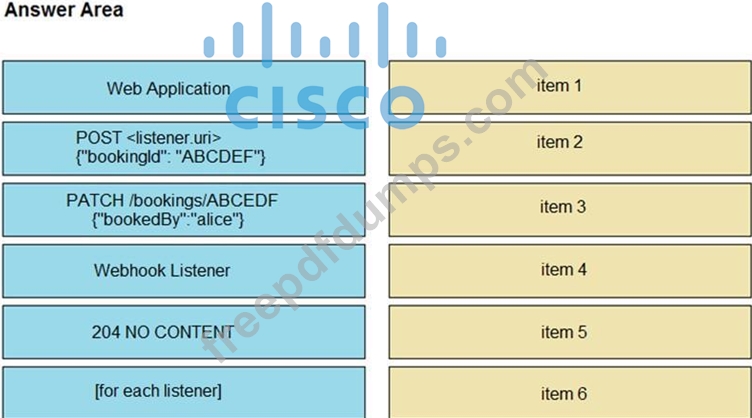
Refer to the exhibit above and click on the tab in the top left corner to view a diagram that describes the typical flow of requests involved when a webhook is created for a booking service.
Drag and drop the requests from the left onto the item numbers on the right that match the missing sections in the sequence diagram to design the complete flow of requests involved as a booking is updated from a web application.


350-901 Exam Question 187
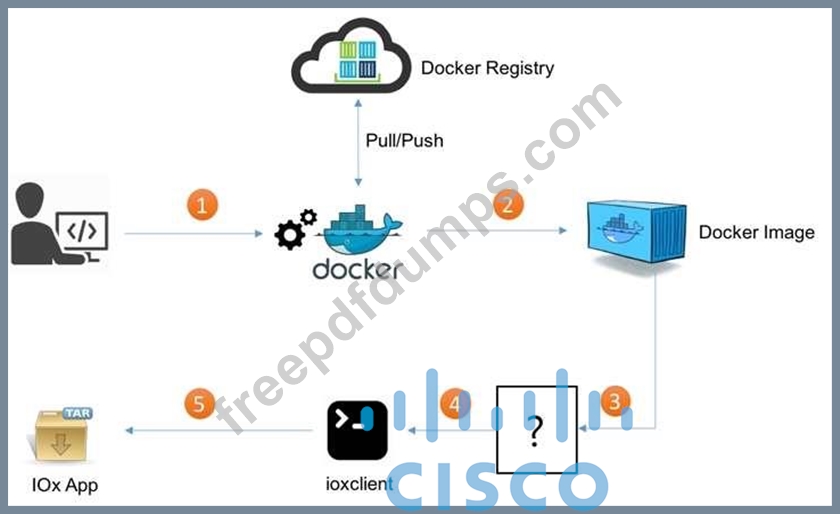
Refer to the exhibit. What is the missing step in deploying a Docker container to IOx?
350-901 Exam Question 188
Refer to the exhibit.
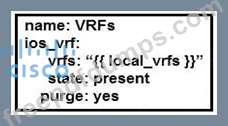
The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?

The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?
350-901 Exam Question 189
Refer to the exhibits which show the documentation associated with the create port object API cafl in Cisco Firepower Threat Defense, and a cURL command. Which data payload completes the cURL command to run the APi call?
A)
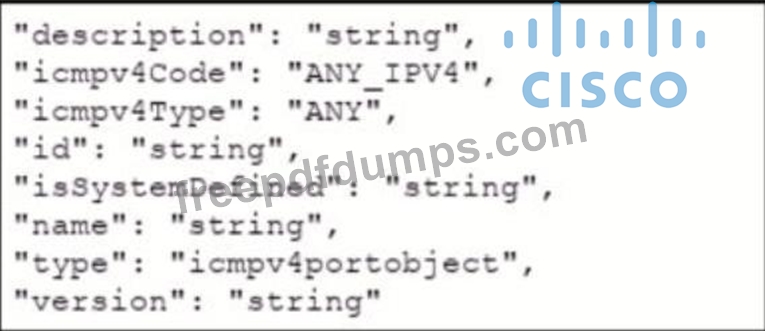
B)
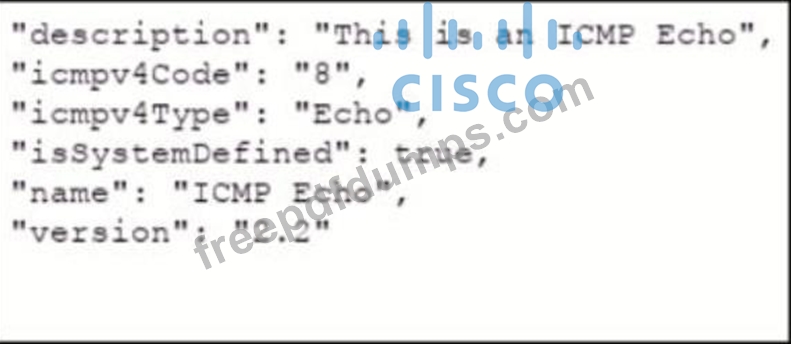
C)
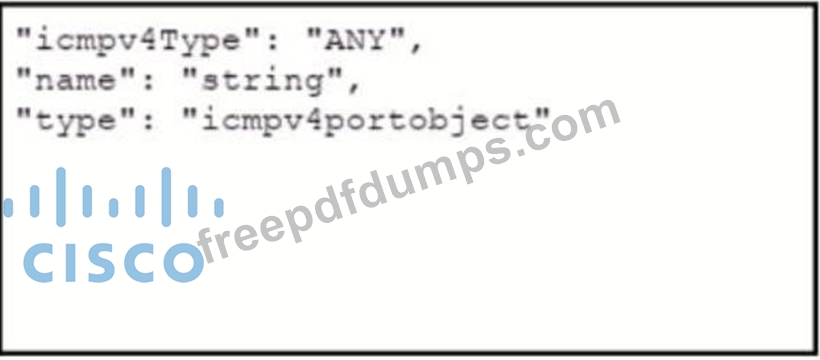
D)
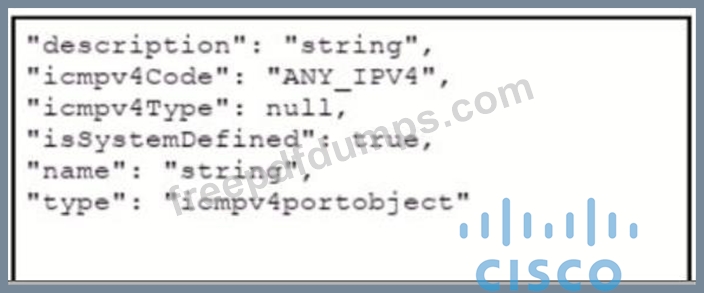
A)

B)

C)

D)

350-901 Exam Question 190
Refer to the exhibit.

A developer created a Python script to retrieve information about Meraki devices in a local network deployment After requesting a security review of the code the security analyst has observed poor secret storage practices What is the appropriate secret storage approach''

A developer created a Python script to retrieve information about Meraki devices in a local network deployment After requesting a security review of the code the security analyst has observed poor secret storage practices What is the appropriate secret storage approach''