CAS-005 Exam Question 76
Audit findings indicate several user endpoints are not utilizing full disk encryption During me remediation process, a compliance analyst reviews the testing details for the endpoints and notes the endpoint device configuration does not support full disk encryption Which of the following is the most likely reason me device must be replaced'
CAS-005 Exam Question 77
A user from the sales department opened a suspicious file attachment. The sales department then contacted the SOC to investigate a number of unresponsive systems, and the team successfully identified the file and the origin of the attack. Which of the following is the next step of the incident response plan?
CAS-005 Exam Question 78
A security analyst is reviewing the following authentication logs:
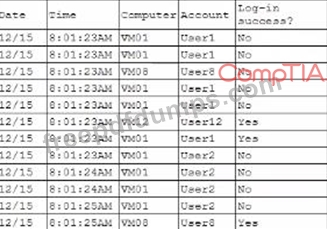
Which of thefollowing should the analyst do first?

Which of thefollowing should the analyst do first?
CAS-005 Exam Question 79
Which of the following best describes the challenges associated with widespread adoption of homomorphic encryption techniques?
CAS-005 Exam Question 80
After several companies in the financial industry were affected by a similar incident, they shared information about threat intelligence and the malware used for exploitation. Which of the following should the companies do to best indicate whether the attacks are being conducted by the same actor?

