CS0-002 Exam Question 1
Which of the following control types is an organization using when restoring a backup?
CS0-002 Exam Question 2
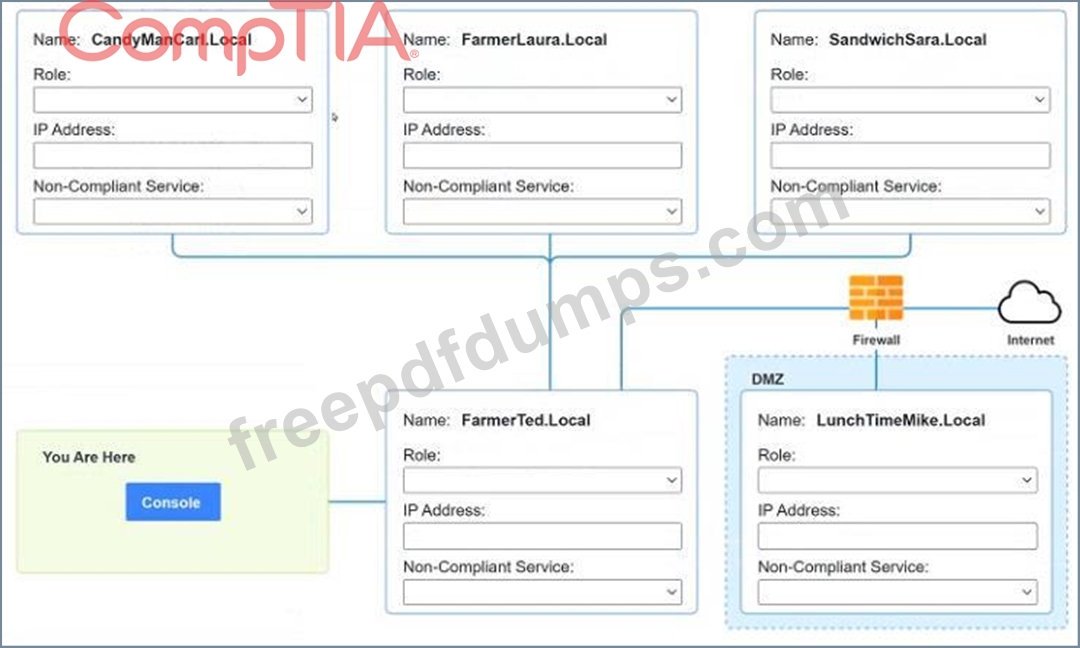
You are a penetration tester who is reviewing the system hardening guidelines for a company. Hardening guidelines indicate the following.
* There must be one primary server or service per device.
* Only default port should be used
* Non- secure protocols should be disabled.
* The corporate internet presence should be placed in a protected subnet Instructions :
* Using the available tools, discover devices on the corporate network and the services running on these devices.
You must determine
* ip address of each device
* The primary server or service each device
* The protocols that should be disabled based on the hardening guidelines
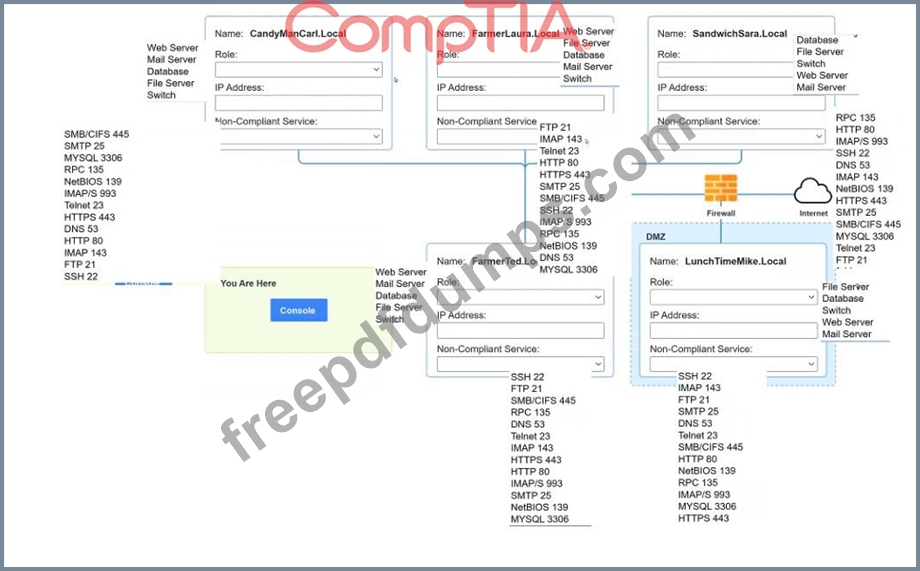
* There must be one primary server or service per device.
* Only default port should be used
* Non- secure protocols should be disabled.
* The corporate internet presence should be placed in a protected subnet Instructions :
* Using the available tools, discover devices on the corporate network and the services running on these devices.
You must determine
* ip address of each device
* The primary server or service each device
* The protocols that should be disabled based on the hardening guidelines


CS0-002 Exam Question 3
To prioritize the morning's work, an analyst is reviewing security alerts that have not yet been investigated.
Which of the following assets should be investigated FIRST?
Which of the following assets should be investigated FIRST?
CS0-002 Exam Question 4
An information security analyst is compiling data from a recent penetration test and reviews the following output:
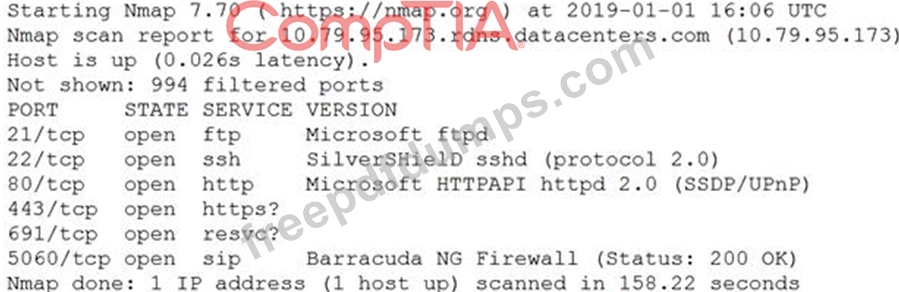
The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?

The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?
CS0-002 Exam Question 5
A security analyst has determined the security team should take action based on the following log:
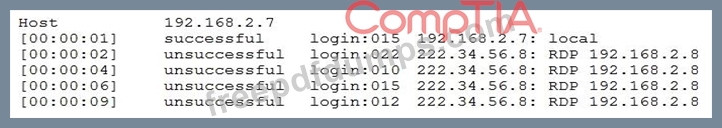
Which of the following should be used to improve the security posture of the system?

Which of the following should be used to improve the security posture of the system?