N10-009 Exam Question 11
Which of the following routing protocols uses an autonomous system number?
N10-009 Exam Question 12
A network administrator configured a router interface as 10.0.0.95 255.255.255.240. The administrator discovers that the router is not routing packets to a web server with IP 10.0.0.81/28. Which of the following is the best explanation?
N10-009 Exam Question 13
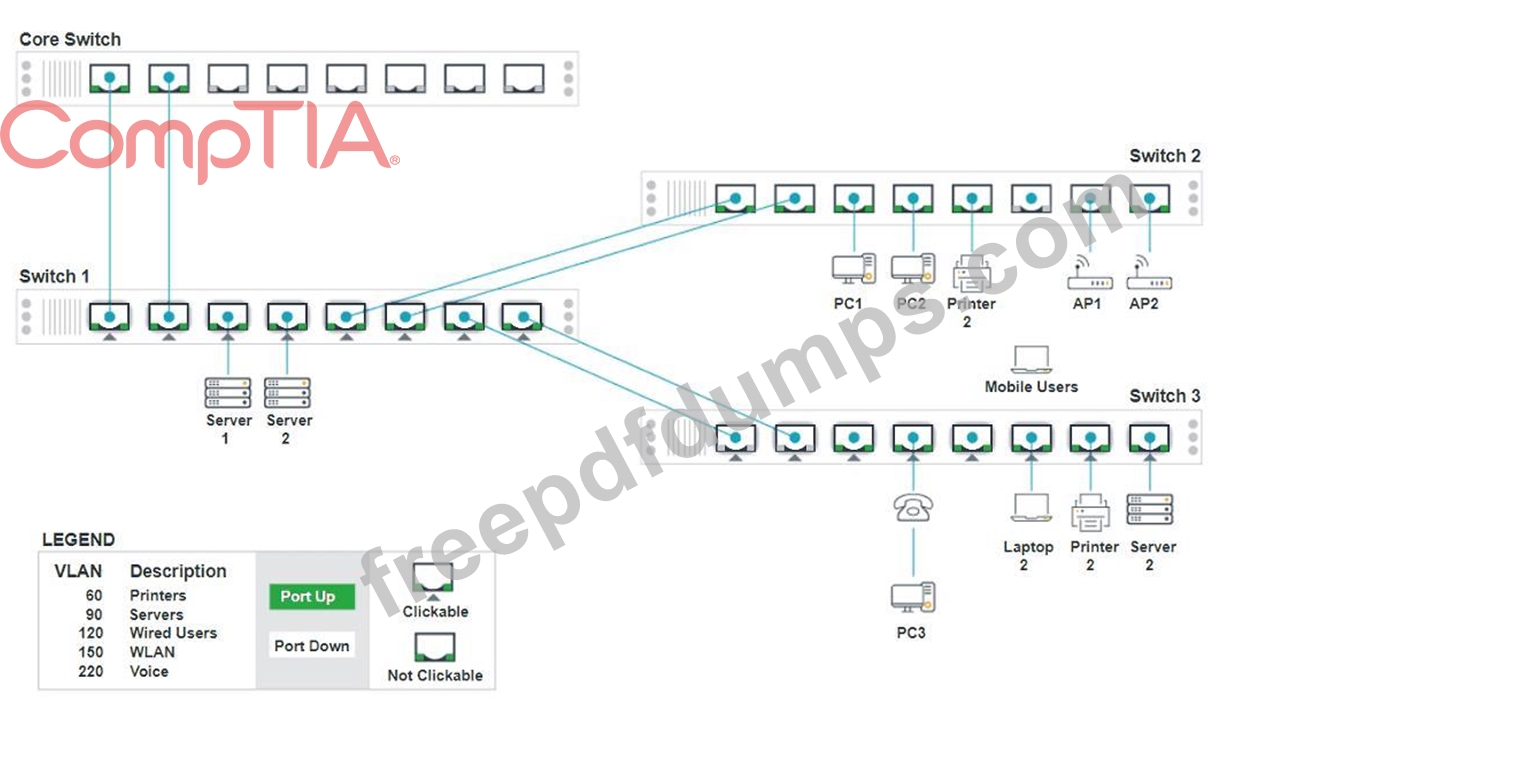
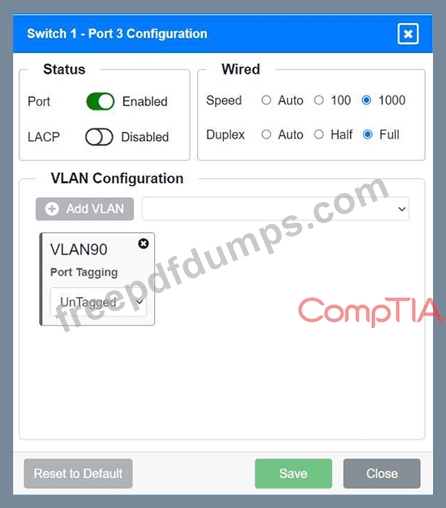
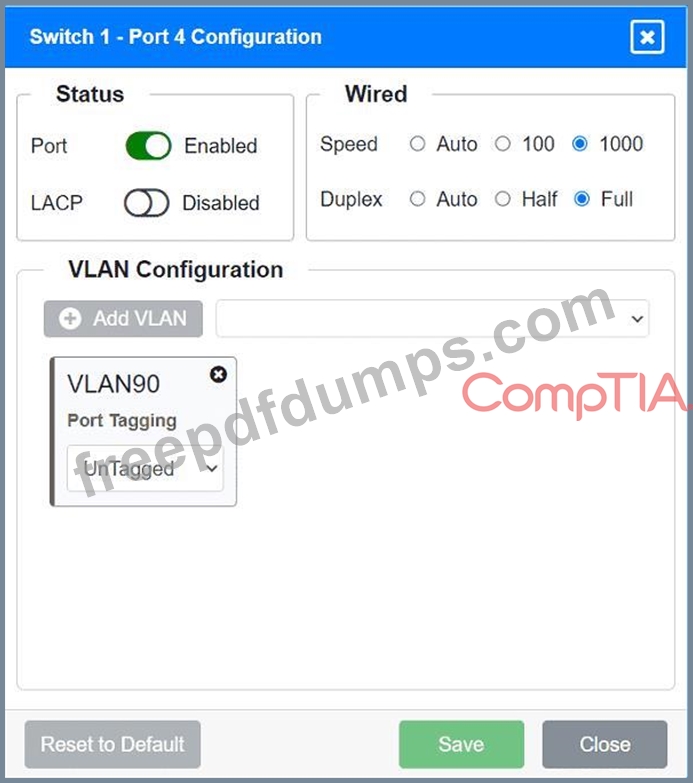
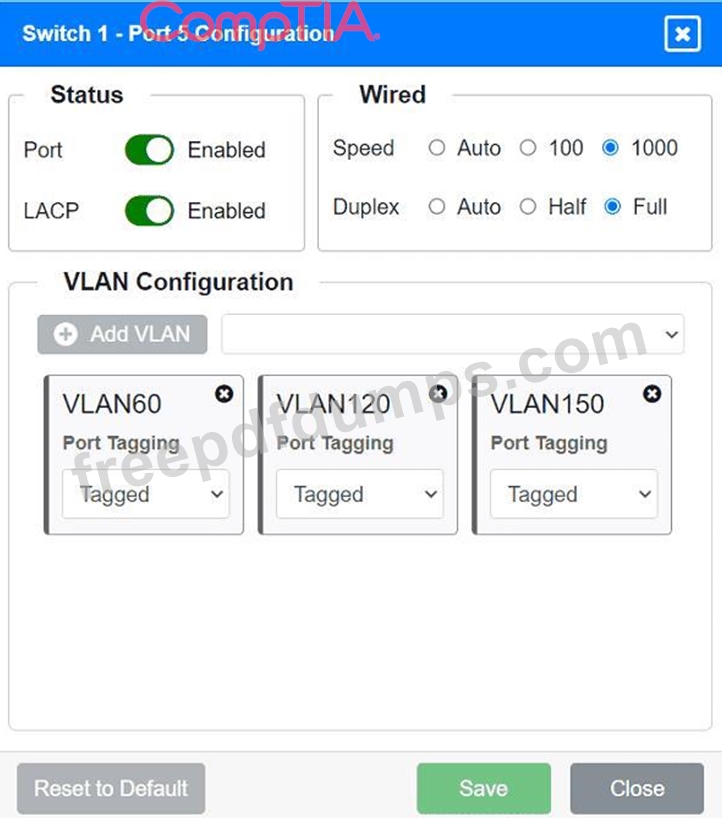
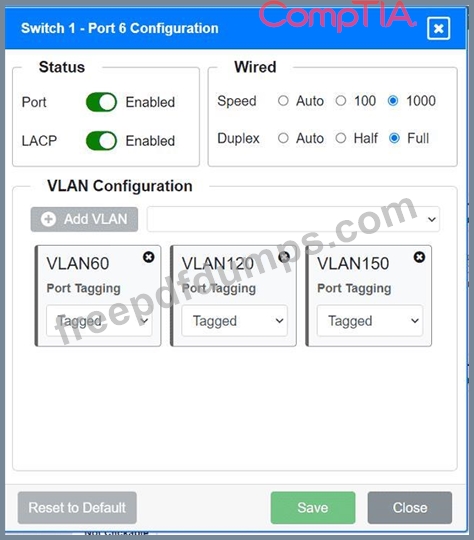
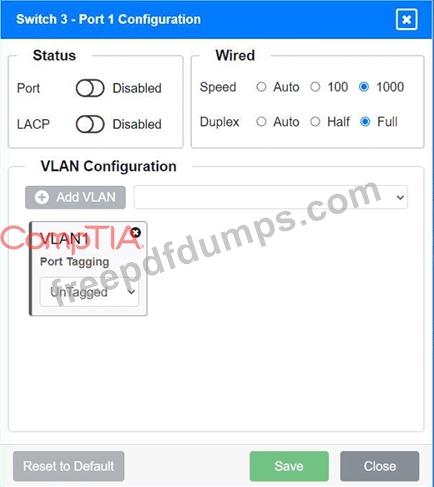
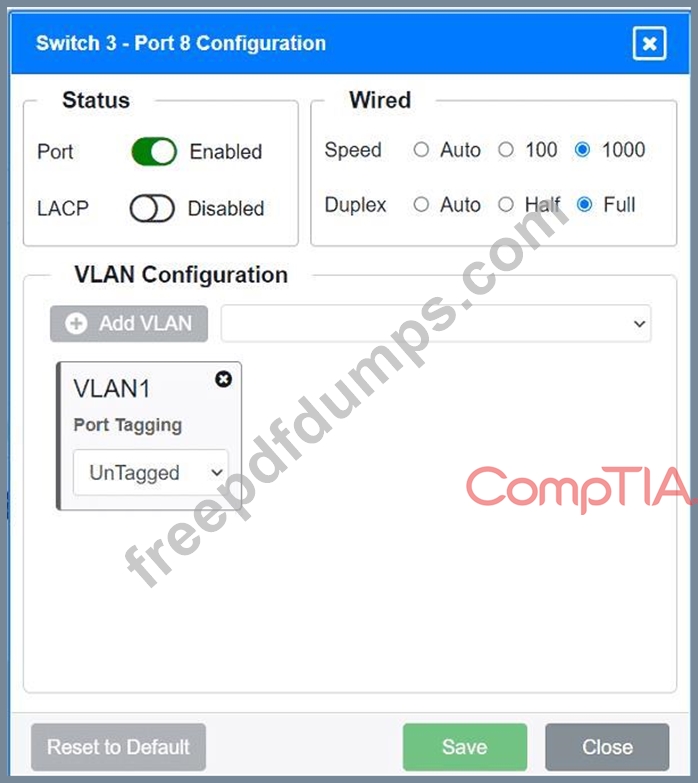
A network technician replaced an access layer switch and needs to reconfigure it to allow the connected devices to connect to the correct networks.
INSTRUCTIONS
Click on the appropriate port(s) on Switch 1 and Switch 3 to verify or reconfigure the correct settings:
Ensure each device accesses only its
correctly associated network.
Disable all unused switchports.
. Require fault-tolerant connections
between the switches.
. Only make necessary changes to
complete the above requirements.
INSTRUCTIONS
Click on the appropriate port(s) on Switch 1 and Switch 3 to verify or reconfigure the correct settings:
Ensure each device accesses only its
correctly associated network.
Disable all unused switchports.
. Require fault-tolerant connections
between the switches.
. Only make necessary changes to
complete the above requirements.







N10-009 Exam Question 14
Users usually use RDP to connect to a terminal server with hostname TS19 that points to 10.0.100.19.
However, users recently have been unable to connect to TS19. The technician pings 10.0.100.19 and gets an unreachable error. Which of the following is the most likely cause?
However, users recently have been unable to connect to TS19. The technician pings 10.0.100.19 and gets an unreachable error. Which of the following is the most likely cause?
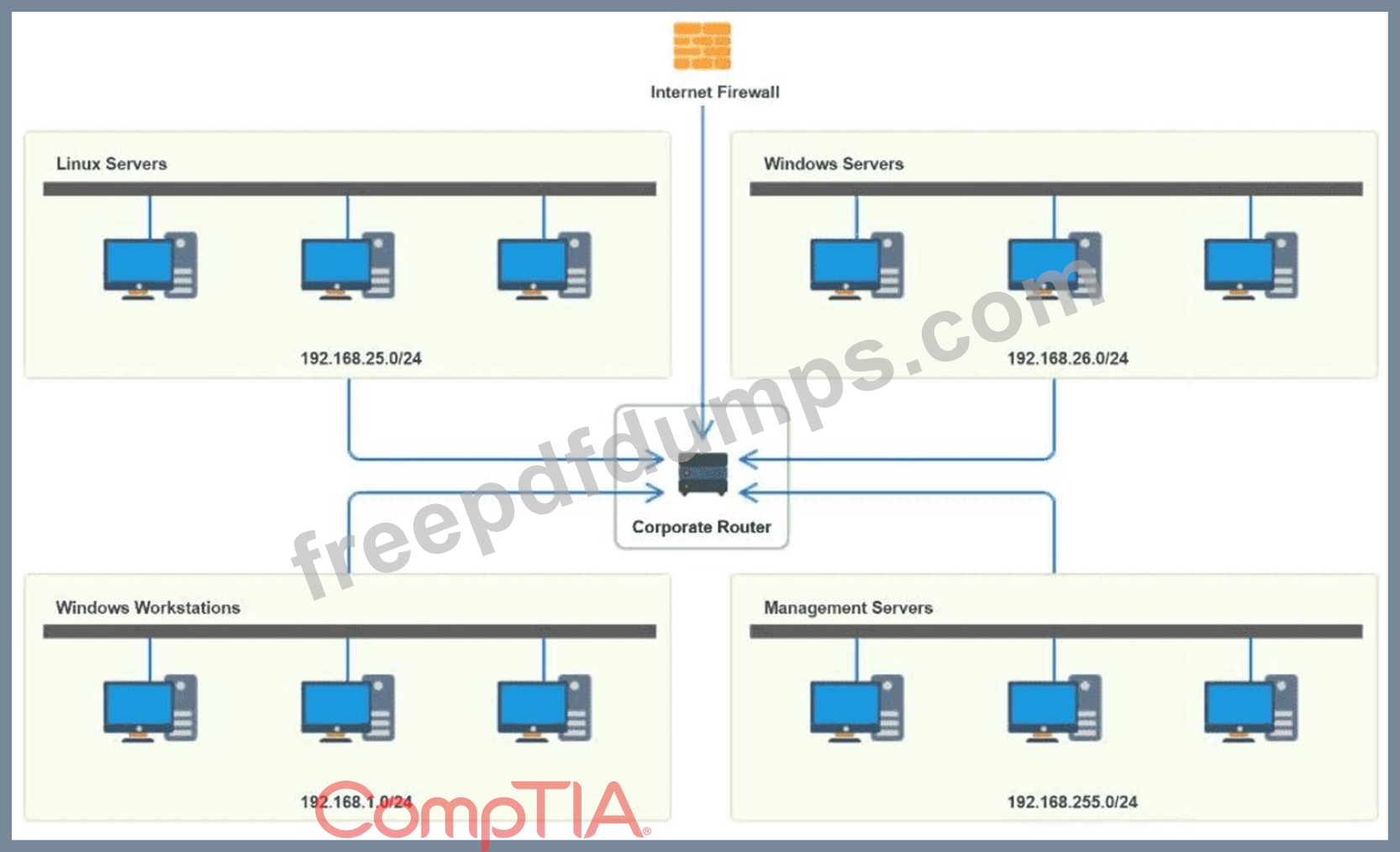
N10-009 Exam Question 15
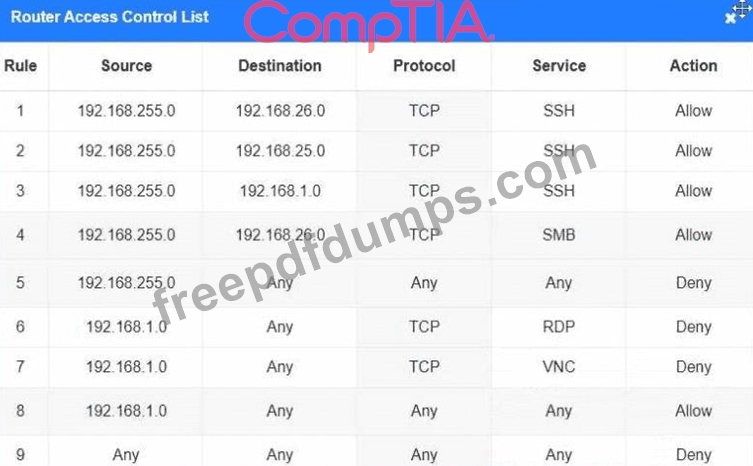
You have been tasked with implementing an ACL on the router that will:
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.