SY0-601 Exam Question 51
Local guidelines require that all information systems meet a minimum-security baseline to be compliant.
Which of the following can security administrators use to assess their system configurations against the baseline?
Which of the following can security administrators use to assess their system configurations against the baseline?
SY0-601 Exam Question 52
A company is setting up a web server on the Internet that will utilize both encrypted and unencrypted web-browsing protocols. A security engineer runs a port scan against the server from the Internet and sees the following output:
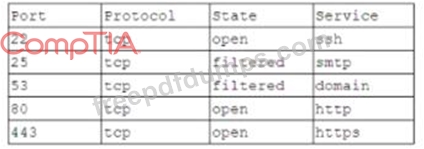
Which of the following steps would be best for the security engineer to take NEXT?

Which of the following steps would be best for the security engineer to take NEXT?
SY0-601 Exam Question 53
A global company is experiencing unauthorized logging due to credential theft and account lockouts caused by brute-force attacks. The company is considering implementing a third-party identity provider to help mitigate these attacks. Which of the following would be the BEST control for the company to require from prospective vendors'?
SY0-601 Exam Question 54
A security analyst is reviewing logs on a server and observes the following output:
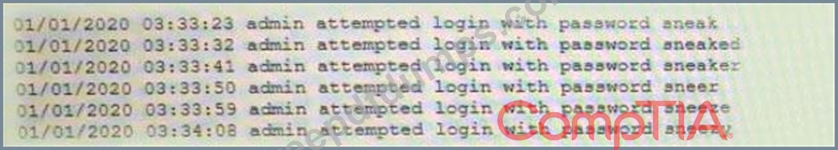
Which of the following is the security analyst observing?

Which of the following is the security analyst observing?
SY0-601 Exam Question 55
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
To better understand what is going on, the analyst runs a command and receives the following output:
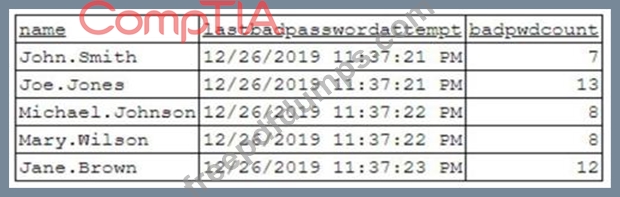
Based on the analyst's findings, which of the following attacks is being executed?
To better understand what is going on, the analyst runs a command and receives the following output:

Based on the analyst's findings, which of the following attacks is being executed?

