SY0-601 Exam Question 26
An organization blocks user access to command-line interpreters but hackers still managed to invoke the interpreters using native administrative tools Which of the following should the security team do to prevent this from Happening in the future?
SY0-601 Exam Question 27
A company is required to continue using legacy software to support a critical service. Which of the following BEST explains a risk of this practice?
SY0-601 Exam Question 28
A company just implemented a new telework policy that allows employees to use personal devices for official email and file sharing while working from home. Some of the requirements are:
* Employees must provide an alternate work location (i.e., a home address)
* Employees must install software on the device that will prevent the loss of proprietary data but will not restrict any other software from being installed.
Which of the following BEST describes the MDM options the company is using?
* Employees must provide an alternate work location (i.e., a home address)
* Employees must install software on the device that will prevent the loss of proprietary data but will not restrict any other software from being installed.
Which of the following BEST describes the MDM options the company is using?
SY0-601 Exam Question 29
Which of the following is a risk that is specifically associated with hosting applications in the public cloud?
SY0-601 Exam Question 30
A company is setting up a web server on the Internet that will utilize both encrypted and unencrypted web-browsing protocols. A security engineer runs a port scan against the server from the Internet and sees the following output:
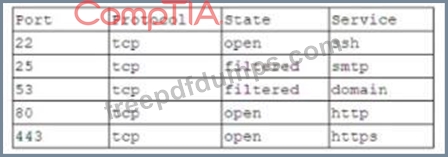
Which of the following steps would be best for the security engineer to take NEXT?

Which of the following steps would be best for the security engineer to take NEXT?

