SY0-601 Exam Question 186
An attacker is attempting, to harvest user credentials on a client's website. A security analyst notices multiple attempts of random usernames and passwords. When the analyst types in a random username and password.
the logon screen displays the following message:
Which of the following should the analyst recommend be enabled?
the logon screen displays the following message:
Which of the following should the analyst recommend be enabled?
SY0-601 Exam Question 187
A security analyst is investigation an incident that was first reported as an issue connecting to network shares and the internet, While reviewing logs and tool output, the analyst sees the following:

Which of the following attacks has occurred?

Which of the following attacks has occurred?
SY0-601 Exam Question 188
A security analyst sees the following log output while reviewing web logs:

Which of the following mitigation strategies would be BEST to prevent this attack from being successful?

Which of the following mitigation strategies would be BEST to prevent this attack from being successful?
SY0-601 Exam Question 189
Joe. a security analyst, recently performed a network discovery to fully understand his organization's electronic footprint from a "public" perspective. Joe ran a set of commands and received the following output:
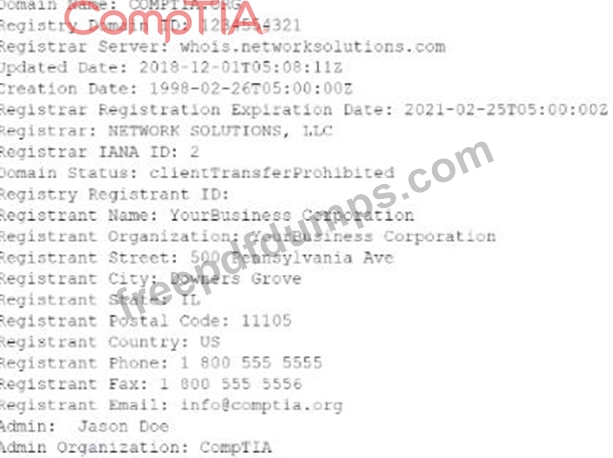
Which of the following can be determined about the organization's public presence and security posture? (Select TWO).

Which of the following can be determined about the organization's public presence and security posture? (Select TWO).
SY0-601 Exam Question 190
Local guidelines require that all information systems meet a minimum-security baseline to be compliant. Which of the following can security administrators use to assess their system configurations against the baseline?

