SY0-601 Exam Question 206
A small business office is setting up a wireless infrastructure with primary requirements centered around protecting customer information and preventing unauthorized access to the business network. Which of the following would BEST support the office's business needs? (Select TWO)
SY0-601 Exam Question 207
A financial institution would like to stare is customer data a could but still allow the data ta he accessed and manipulated while encrypted. Doing se would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concern about computational overheads and slow speeds, Which of the following cryptographic techniques would BEST meet the requirement?
SY0-601 Exam Question 208
A security analyst needs to generate a server certificate to be used for 802.1X and secure RDP connections.
The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task?
The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task?
SY0-601 Exam Question 209
A company has discovered unauthorized devices are using its WiFi network, and it wants to harden the access point to improve security. Which of the following configuration should an analyst enable to improve security?
(Select Two)
(Select Two)
SY0-601 Exam Question 210
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
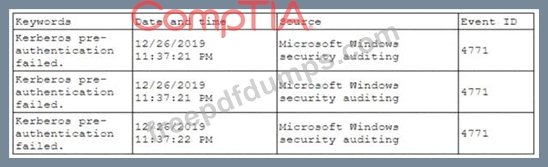
To better understand what is going on, the analyst runs a command and receives the following output:
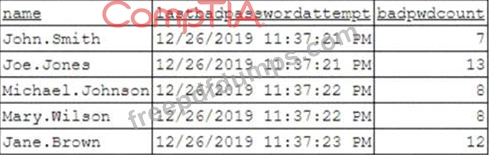
Based on the analyst's findings, which of the following attacks is being executed?

To better understand what is going on, the analyst runs a command and receives the following output:

Based on the analyst's findings, which of the following attacks is being executed?

