SY0-601 Exam Question 246
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst MOST likely seeing?
A)
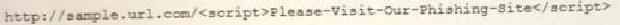
B)

C)
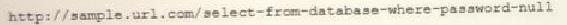
D)
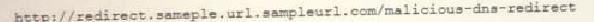
A)
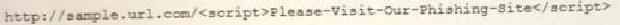
B)

C)
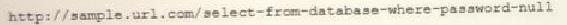
D)
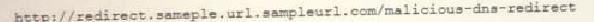
SY0-601 Exam Question 247
Which of the following environments minimizes end-user disruption and is MOST likely to be used to assess the impacts of any database migrations or major system changes by using the final version of the code?
SY0-601 Exam Question 248
A security analyst is reviewing the output of a web server log and notices a particular account is attempting to transfer large amounts of money:
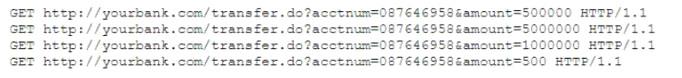
Which of the following types of attack is MOST likely being conducted?

Which of the following types of attack is MOST likely being conducted?
SY0-601 Exam Question 249
A security engineer has enabled two-factor authentication on all workstations. Which of the following approaches are the MOST secure? (Select TWO).
SY0-601 Exam Question 250
A cybersecurity department purchased o new PAM solution. The team is planning to randomize the service account credentials of the Windows server first. Which of the following would be the BEST method to increase the security on the Linux server?

