SY0-601 Exam Question 351
Which of the following disaster recovery tests is The LEAST time-consuming for the disaster recovery team?
SY0-601 Exam Question 352
During a routine scan of a wireless segment at a retail company, a security administrator discovers several devices are connected to the network that do not match the company's naming convention and are not in the asset Inventory. WiFi access Is protected with 255-Wt encryption via WPA2. Physical access to the company's facility requires two-factor authentication using a badge and a passcode Which of the following should the administrator implement to find and remediate the Issue? (Select TWO).
SY0-601 Exam Question 353
A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log:
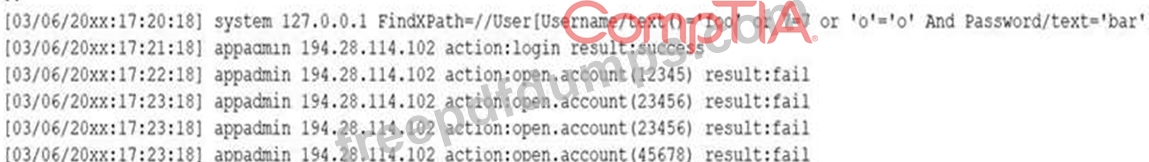
Which of the following can the security analyst conclude?

Which of the following can the security analyst conclude?
SY0-601 Exam Question 354
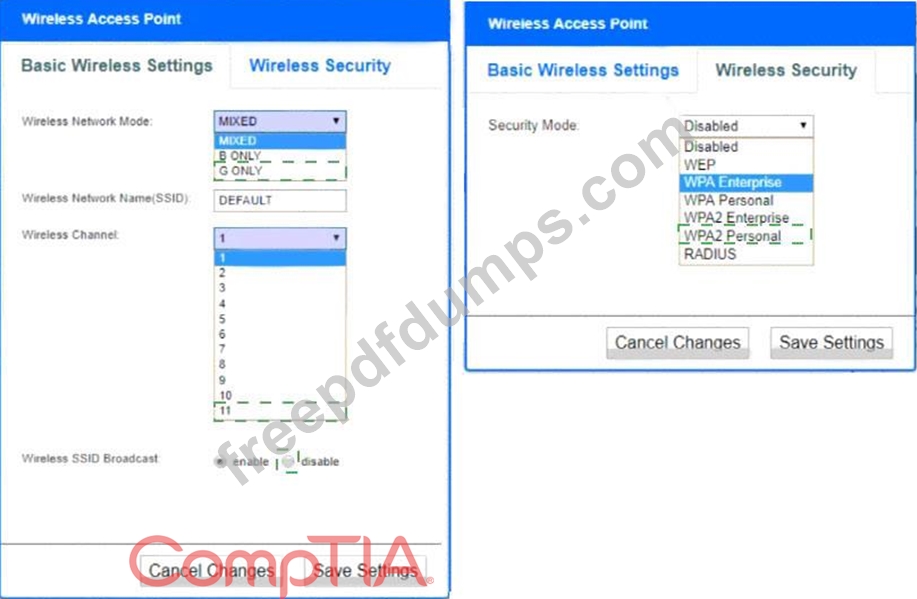
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
* WAP
* DHCP Server
* AAA Server
* Wireless Controller
* LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
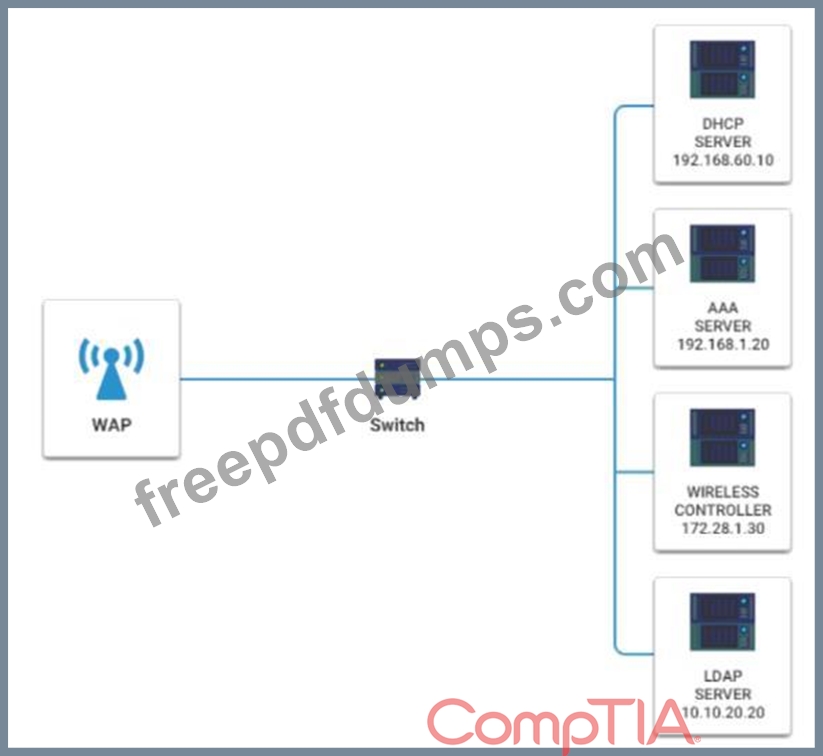
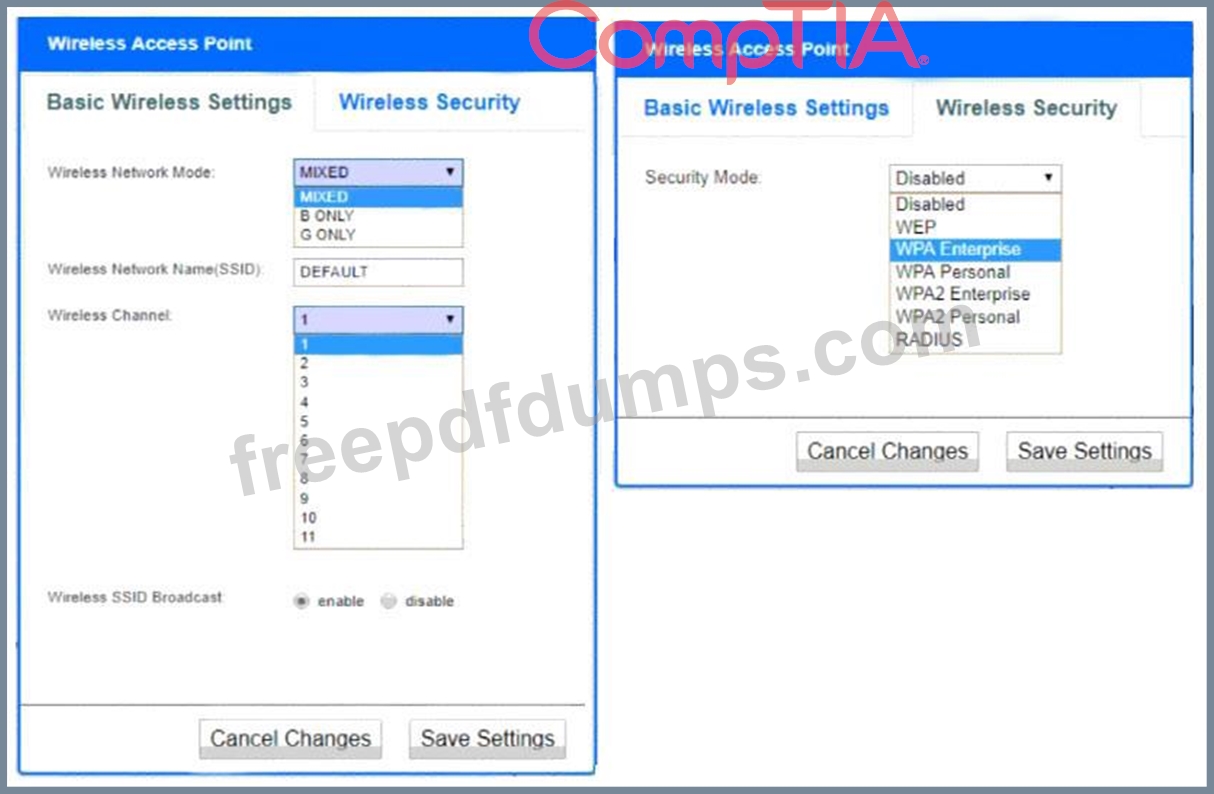
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
* WAP
* DHCP Server
* AAA Server
* Wireless Controller
* LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


SY0-601 Exam Question 355
While checking logs, a security engineer notices a number of end userssuddenly downloading files with the
.tar.gz extension. Closer examination of the files reveals they are PE32 files. The end users state they did not initiate any of the downloads. Further investigation reveals the end users all clicked on an external emailcontaining an infected MHT file with an href link a week prior. Which of the following is MOST likely occurring?
.tar.gz extension. Closer examination of the files reveals they are PE32 files. The end users state they did not initiate any of the downloads. Further investigation reveals the end users all clicked on an external emailcontaining an infected MHT file with an href link a week prior. Which of the following is MOST likely occurring?