SY0-601 Exam Question 6
The Chief Information Security Officer directed a nsk reduction in shadow IT and created a policy requiring all unsanctioned high-nsk SaaS applications to be blocked from user access Which of the following is the BEST security solution to reduce this risk?
SY0-601 Exam Question 7
Which of the following BEST reduces the security risks introduced when running systems that have expired vendor support and lack an immediate replacement?
SY0-601 Exam Question 8
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to connect network traffic between workstation throughout the network. The analysts review the following logs:
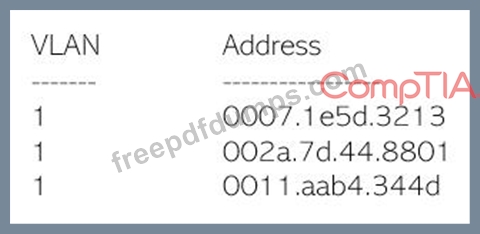
The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?

The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?
SY0-601 Exam Question 9
Which of the following prevents an employee from seeing a colleague who is visting an inappropriate website?
SY0-601 Exam Question 10
A recent security breach exploited software vulnerabilities in the firewall and within the network management solution. Which of the following will MOST likely be used to identify when the breach occurred through each device?

